Doxxed Through VPNs: Former Cybercrime Detective
Our Interview with Travis West on identifying VPN users

Travis West caught our attention with the following quote:
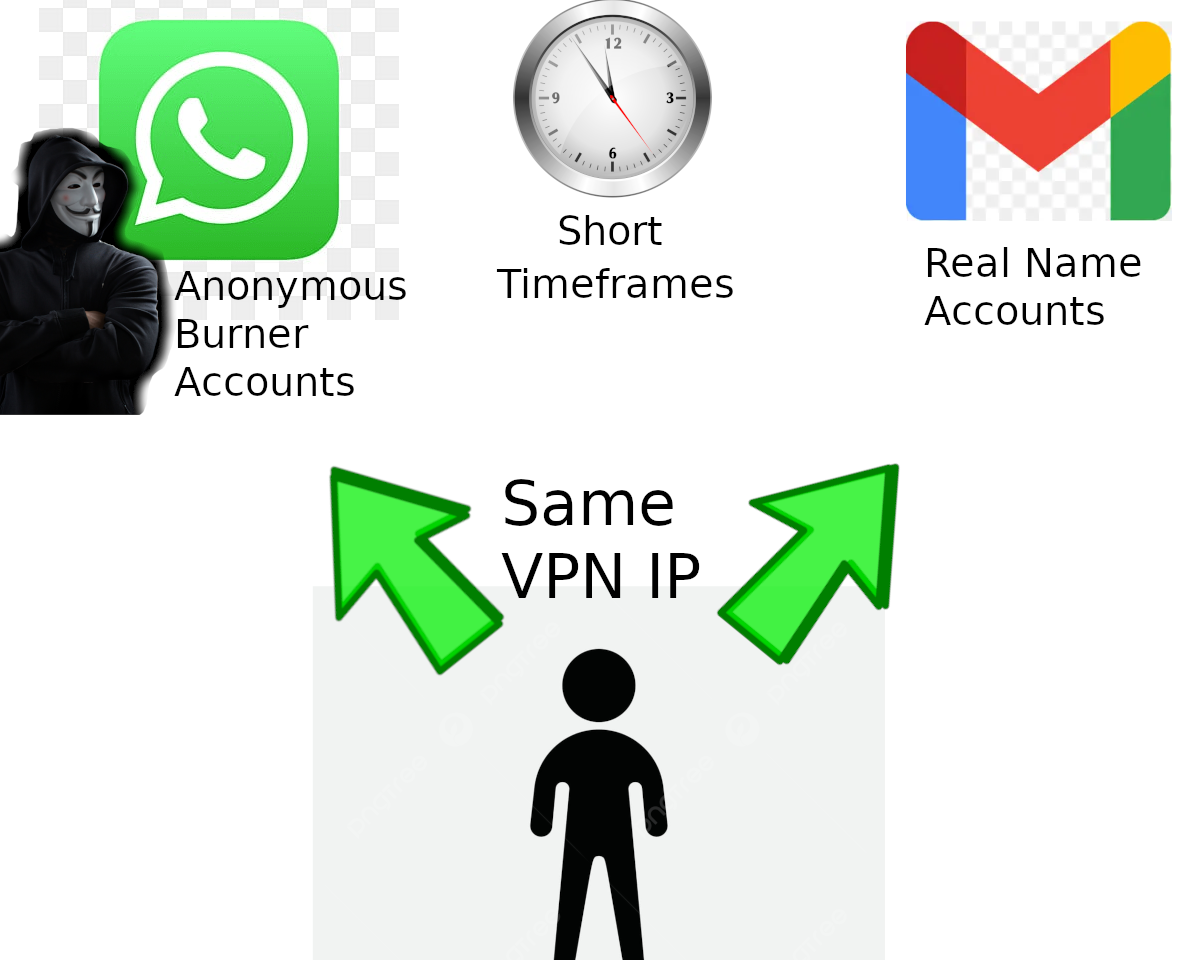
"A common mistake I have seen people who want to remain anonymous online make is using a VPN consistently with burner accounts, but then they use the same VPN with the same IP address at around the same time to access accounts already associated with them, such as their online banking or a Gmail they have used since they were a teenager. So if they were targeted by the State for whatever reason already, their IP address logs for their known accounts would have the same IP addresses as the burner accounts at around the same time. If the timing is less than 10 minutes apart, and even if this occurs just once, there will be assumptions it is the same person."
Background
Travis West is a former detective that specialized in cybercrime investigations, so he is no longer in this role. His background in his own words:
A Sheriff's Office in Oregon, worked local cases, regional cases, and some federal/other state assists. I helped a couple foreign investigators too. Poland, Ukraine. Hard to not help when someone has a good case and they don't know what to do or they aren't sure the next steps.
He has quite a few certifications:
Certified Cyber Crime Investigator (National White Collar Crime Center)
Certified Cyber Investigator (Carnegie Mellon University)
Certified Anti-Money Laundering Specialist (CAMS)
Advanced Crypto Investigator (TRM-ACI)
Certified Investigator (TRM-CI)
Crypto Fundamentals Certification (TRM-CFC)
Digital Forensics and Cryptocurrency (TRM-DFC)
Crypto Compliance Specialist (TRM-CCS)
Certified Cryptocurrency Forensic Investigator (CCFI)
Certified Bitcoin Professional (CBP)
Advanced Police Officer Certification (OR, USA)
Child Forensic Interviewer (OCFIT)
Nostr
We first met him on Nostr. He can be found at:
npub18hqtw4vjsg6s0a0kyhugn5mt5fs8fp64pd8nsv66vqld5qg090pqe75kus
Libertarian
We asked for an interview based off the above quote. He agreed to do the interview in the context of helping privacy and individual liberty. And this interview does NOT mean he encourages crime. In fact, even libertarians would agree on his actions.
I was very libertarian the entire time I was a detective, just went after people I perceived that violated private property rights or were violent offenders. I think they get used to not being investigated. Especially if they are stealing less than $10k from individuals.
Fair enough, so it’s primarily theft and violence?
Drug laws I enforced initially. But my mind changed on those after mainly listening a lot to libertarian podcasts.
He later went on to discuss helping track down scammers who had stolen from elderly victims, often from buying data on the darkweb. And in some cases, Travis West became the hero, as he got the scammers to pay the victims, in situations where it was too small a case for federal law enforcement.
VPN IPs
Can you elaborate on the original quote about identifying users through a VPN?
If it is the same IP with nearly the same time frame, even if it is an IP associated with a VPN, there will be an assumption it is the same user. Sometimes other fingerprints, like browser, but if the IMEI can be seen at all, that is definitely used. And this assumption isn't going to be a conviction, but it will be used to justify further subpoenas, warrants, etc.
How is the fingerprint used?
Device timezone is a fingerprint used a lot. Gives a good idea of at least where your target might be. For me, gave me an idea of whether or not I pursue the investigation further. If the suspects appear to be from India, for example, may not be worth the work/time.
Aren’t there like a thousand or more people on a VPN IP?
The shared IPs with VPNs will be argued for sure to cast doubt that it could be another person, for sure. But if you are looking at a bunch of IPs with specific dates and times of a suspect's access and it matches pretty close with your known target's activity, there will be an argument that is likely the same person.
He gave an example of things beyond just an IP address:
A lot of "I will use a VPN and a burner Google account on my phone to commit this crime. Then I will log into my normal, everyday use Google account (that has all my data in Google Drive) with that same device."
Phones
You mentioned IMEIs on phones, which is a big talking point for our website.
IMEI is big because that can be given to all the cell phone providers, Apple, Google, etc. And records can be demanded from them. Most folks use some sort of service connected to something responsive to legal service.
This is from closed source mobile operating systems?
It was Google and Apple for the most part that had them usually. Which is probably due to OS shenanigans. Cell phone providers have them, and the IMSI.
Bitcoin
The conversation went to Bitcoin, and he discussed How Bitcoin Layer 1 is already traced by many companies. And how Lightning may be traced by Chainalysis. He was saying IF he was Chainalysis then:
I would start on lightning by running a lot of router nodes and I would hope that large LSPs dominate the network. Then demand records/data from the LSPs. Or become the dominant LSPs.
Monero
When asked his views on Monero, he first brought up the leaked Chainalysis video going around. Then commented briefly:
I have never bothered to trace Monero tx's but I am aware of cases that have. Tools that analyze Monero. A lot of users are lazy on Monero and can get caught when they are sending quickly to an offramp service.
When you say lazy, you mean the monero guys do zero hops, just send direct to and from a KYC exchange, or with the same VPN IP that puts in the transaction on chain?
Yeah, lazy like one or two hops is all.
Bird’s Eye View
Many people are going to comment on this interview that this is obvious information and these are very low level criminals, stealing less than 10k with horrible op-sec. However, the reason I am showing you this is to demonstrate that EVEN FOR low-level crime, this type of fingerprint and timing analysis can be done by local authorities through a VPN. So just imagine what huge international governments and AI corporations can be doing for money or power.
Why would Travis West do this interview?
My view is that I am far more concerned about State abuse/censorship and a degrading of freedom than I am concerned about scammers and hackers.
Why would I do this interview?
Well, No Libertarian encourages theft, like the kind Travis West investigated. But with knowledge comes power, and I am concerned about people giving away that power to Big Tech, which has become the new propaganda arm of the government.
So our team has put a lot of time into the educational content on this site, invest in yourself to read it. And once again, this makes the case for our VPN that separates segments of your life with different IP addresses and isolated filesystems:
Learn More
If you really want to learn and take your privacy to the next level, Learn about HydraVeil, Access our VPN, and subscribe to our new content via: Arweave Video RSS, Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts

How HydraVeil Works
Technical Deep Dive: The Yellow Paper
[SP]
Feb 20, 2026
Website Makeover
Learn the Concepts with Awesome Visuals
[SP]
Feb 14, 2026
Tor Sync & Tor Profiles Fixed | Release 2.2.1
Faster Initial App Startup
[SP]
Jan 20, 2026

New Sweden VPN Node
Run by AilliA of XMRBazaar
[SP]
Jan 18, 2026