Email Heaven?! PGP Emails to Proton WITHOUT using Proton
You can still send PGP to Proton users without actually using them

Are You New?
You DON’T need to know the Linux terminal to follow this article. I only show you the commands so you can learn a little bit.
Can’t Control the Other Party
First of all, a lot of people use vanity domains, so they might be using Gmail or Proton behind the scenes without you even knowing. You can do a DNS lookup to find out what email provider the other person uses. There are a huge number of tools for this, such as bgp.tools, mxtoolbox, and the Linux command line (with tools such as dig or whois):
dig example.com MX
Note: While bpg.tools is VERY reliable, and the best one in my opinion, they are on cloudflare. While as with dig, you can actually control which DNS server dig uses, such as Quad9:
dig @9.9.9.9 example.com MX
Then the “Whois” command can be installed. For example on Debian/Mint/Ubuntu,
sudo apt install whois
Then lookup the IP,
whois {IP you got from MX}
While you can self-host your own email, you can’t pick what provider the other person uses. If they use Gmail or Proton, you can follow these steps below.
Gmail
If they use Gmail, you can try to convince them to use a browser extension such as Mailvelope, or use an email masking service to hide metadata about your identity, such as AnonAddy.
Proton
I’ve shouted from the rooftops dozens of times that Protonmail seems like a honeypot, because they were funded by the EU government (under the Horizons program), go out of their way to collect more data than needed, provide zero metadata protection, and their whole concept of a web app that forces you to give up control of your PGP key, defeats the purpose of end-to-end encryption. And ALL their traffic is routed through the USA’s Cloudflare.
PGP without Proton
However, you can still get pgp encryption even if you don’t use protonmail, but they do. To get the PGP key of the other person use this Linux command, and just insert their username in the {user} section.
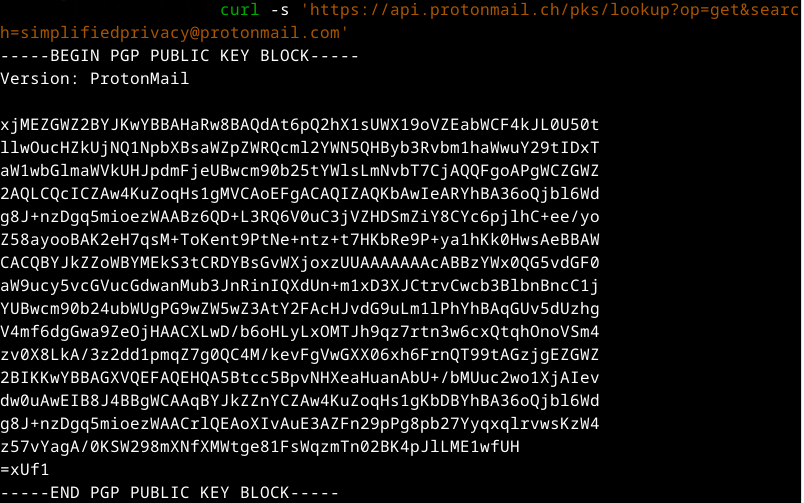
curl -s 'https://api.protonmail.ch/pks/lookup?op=get&search={user}@protonmail.com'
This curl command will print the public key.
Example Output:
Optional,
You can use the “>” symbol to put the key into a file. Public keys use an .asc file extension. So:
curl -s 'https://api.protonmail.ch/pks/lookup?op=get&search={user}@protonmail.com' > name_this_key.asc
Web Browser Version:
If you don’t feel comfortable using the terminal, you can also visit that URL above in a web browser to download it.
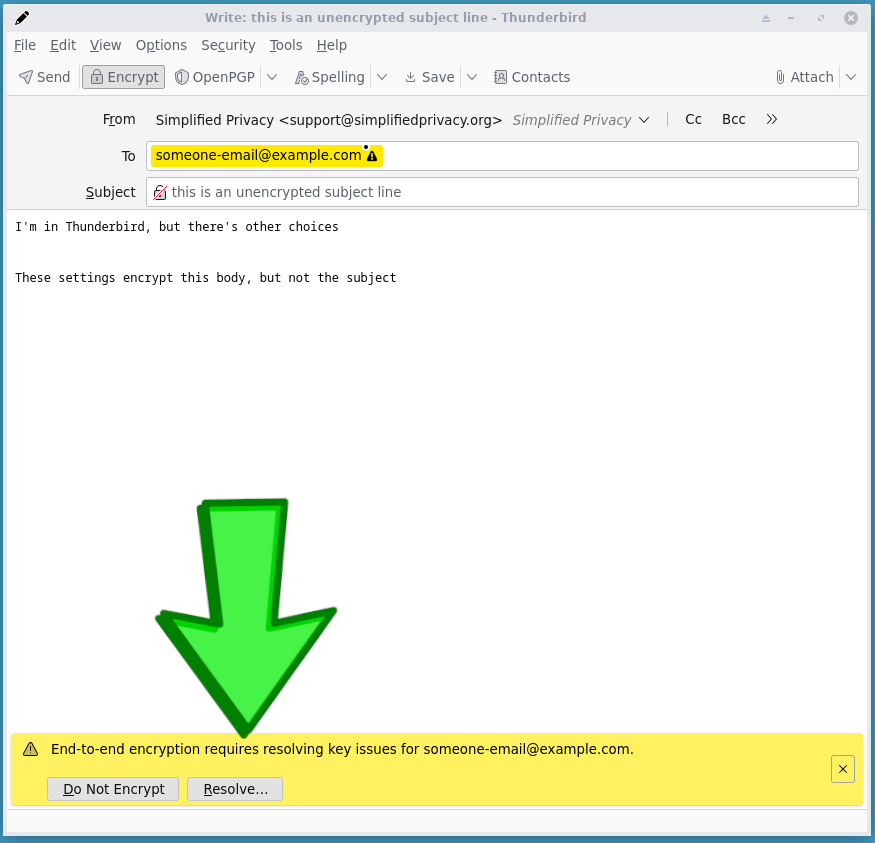
Then take this PGP public key, and add it to the contact in your email client. For example in Thunderbird, once it’s set to encrypt, it will warn you to hit “resolve” on missing a key,
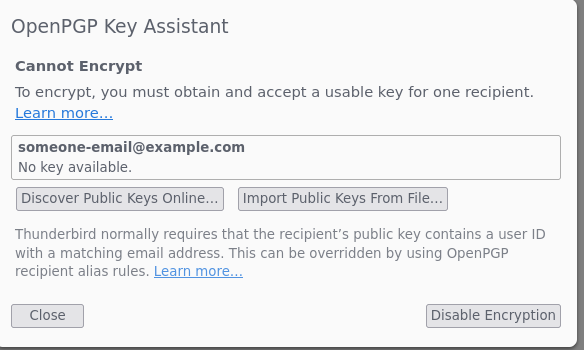
“Import Public Keys from File”
Add that .asc file you saved. It needs the .asc file extension.
By default, the subject is NOT encrypted. Proton (or any server) would then see as plaintext. This is what I’d recommend for cold emailing strangers, and just keep secrets out of the subject line.
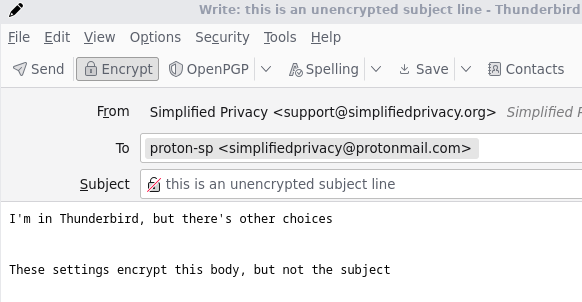
You can encrypt the subject line, by hitting the “OpenPGP” button, but then it appears to a Proton user with the subject “…”
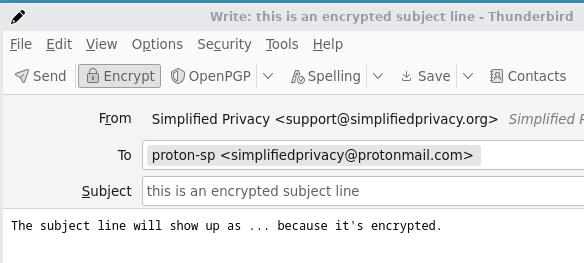
IF you encrypt the subject THEN they see … as subject:
These emails are encrypted, just as good as if you were using Proton, and effortless for the receiver. In fact, even better security because you did it outside their web app.
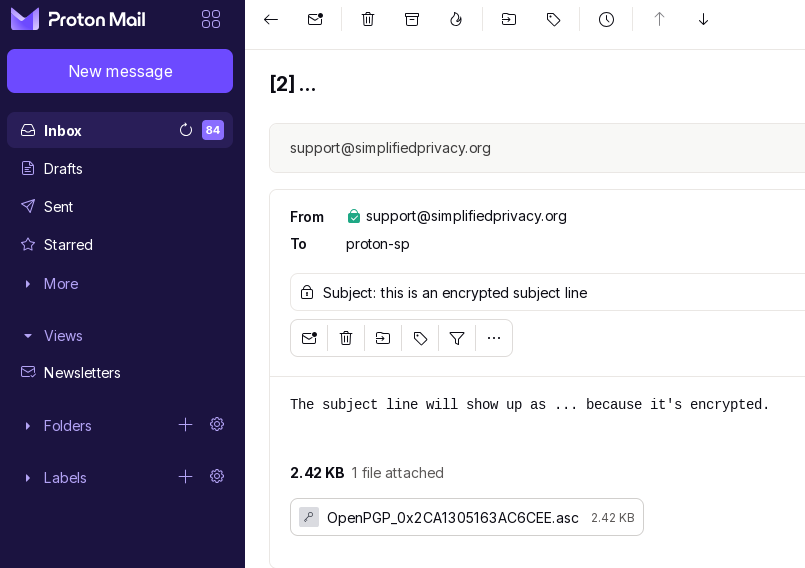
It attaches your public key as an attachment automatically to them. This is the proper format for emails, and NOT using Kleopatra to do raw text that is copy-pasted in. Because the copy-paste method forces both you and receiver to do manual work on each back and forth reply.
In conclusion,
With a self-host email server, you can get all of the benefits and network effects of writing PGP to Proton users, while keeping any OTHER emails completely away from them. And even if you write Proton users with this strategy, they can’t see your IP, do packet tracing, or know when you log in. So to say “oh proton has a network effect” is propaganda.

My critics will say that they don’t feel like doing this “work”. But the work is fast if you use the command line, and Proton’s web app is crazy slow to load. All web browsers suck at decrypting apps. So you’re saving time by having it super quick through any real email client.
Need help with self-hosting? We got you,
Get your own Self-host Email Combo Pack
If you really want to learn and take your privacy to the next level, Learn about HydraVeil, Access our VPN, and subscribe to our new content via: Arweave Video RSS, Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts

Privacy Hell: Proton Uses Cloudflare
How Proton's Negligence Causes Harm
[SP]
Jul 11, 2025

Best Email Client on Android?!
best security features & privacy perks
[SP]
Jan 5, 2025

Protonmail admits it's bullshit
This is an article to go with the new Podcast
[SP]
Nov 10, 2024

Get a Free Month of VoIP from JMP Chat?
With a Cloud VPS or DeGoogled Phones
[ADMIN]
May 16, 2024