They Update Your Fingerprint Every 5 Minutes
Like the Matrix, the Machines Eat Your Data

Video Form
This content is also available in video form on Arweave.
Browser Fingerprints are Misunderstood
People think they have way more protection than they actually do. You’re likely living in the Matrix.

LibreWolf is marketed as “anti-fingerprint”, but this web browser can’t even beat fingerprint-com’s free demo,
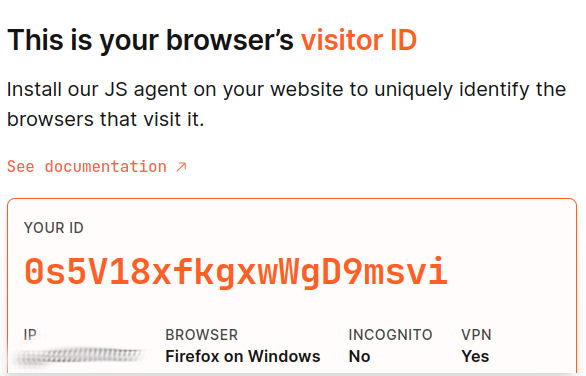
I closed Librewolf, then re-opened it. And that same ID comes up on repeat visits, even in private mode.
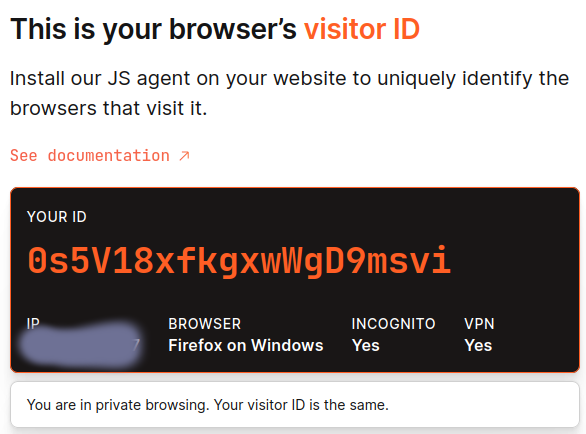
New VM
But then Librewolf installed on a different VM: with the same default settings and version, produces a DIFFERENT UNIQUE fingerprint,
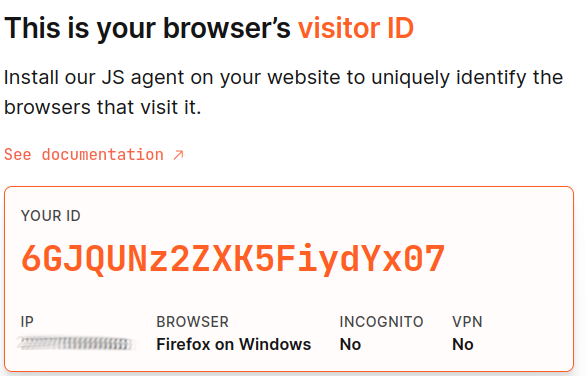
Brave
Brave Browser is also vulnerable to complete fingerprinting.
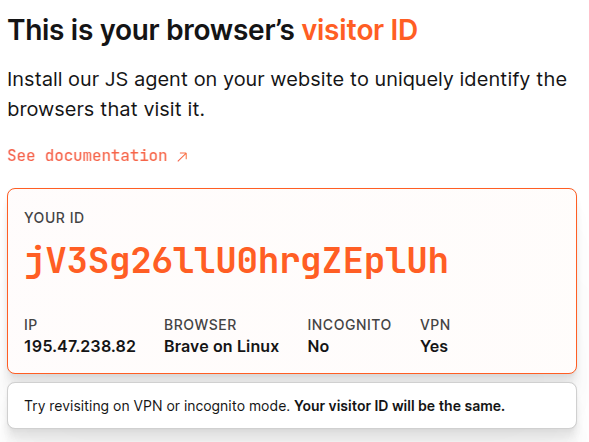
Closing and re-opening in a private window, yields the same unique ID,
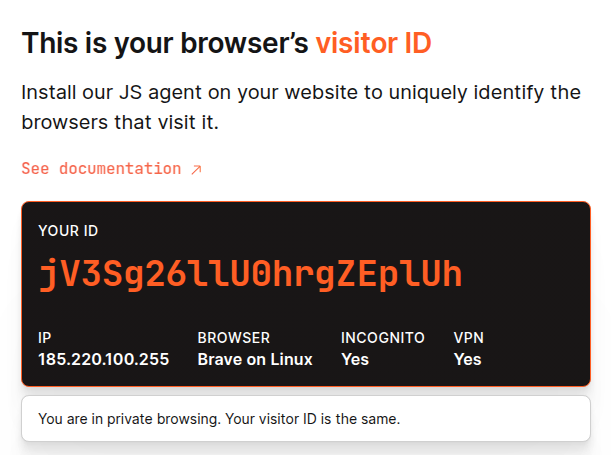
Brave’s “anti-fingerprint” mode does not change these results.


Fingerprint.com is on THOUSANDS of websites, through their Javascript and API calls.
TrustPilot
Western Union
TD-Ameritrade
Dropbox
6 thousand others
You’re very likely using sites with their services, without even knowing it.

Fingerprint-com updates your fingerprint often for changes.
Quote from their docs:
The properties (e.g. browser version, extensions, screen resolution, IP address, etc) that Fingerprint collects from a browser often change over time. When these incremental changes are captured as soon as they occur, Fingerprint can identify a returning browser with industry-leading accuracy. [1]
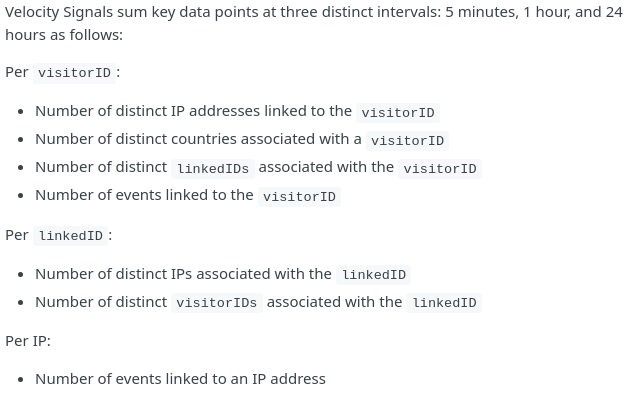
Every 5 minutes the AI feeds off your data.

Fingerprint-com’s API docs show it updates your fingerprint every 5 minutes, every hour, and every 24 hours. This is a screen shot:
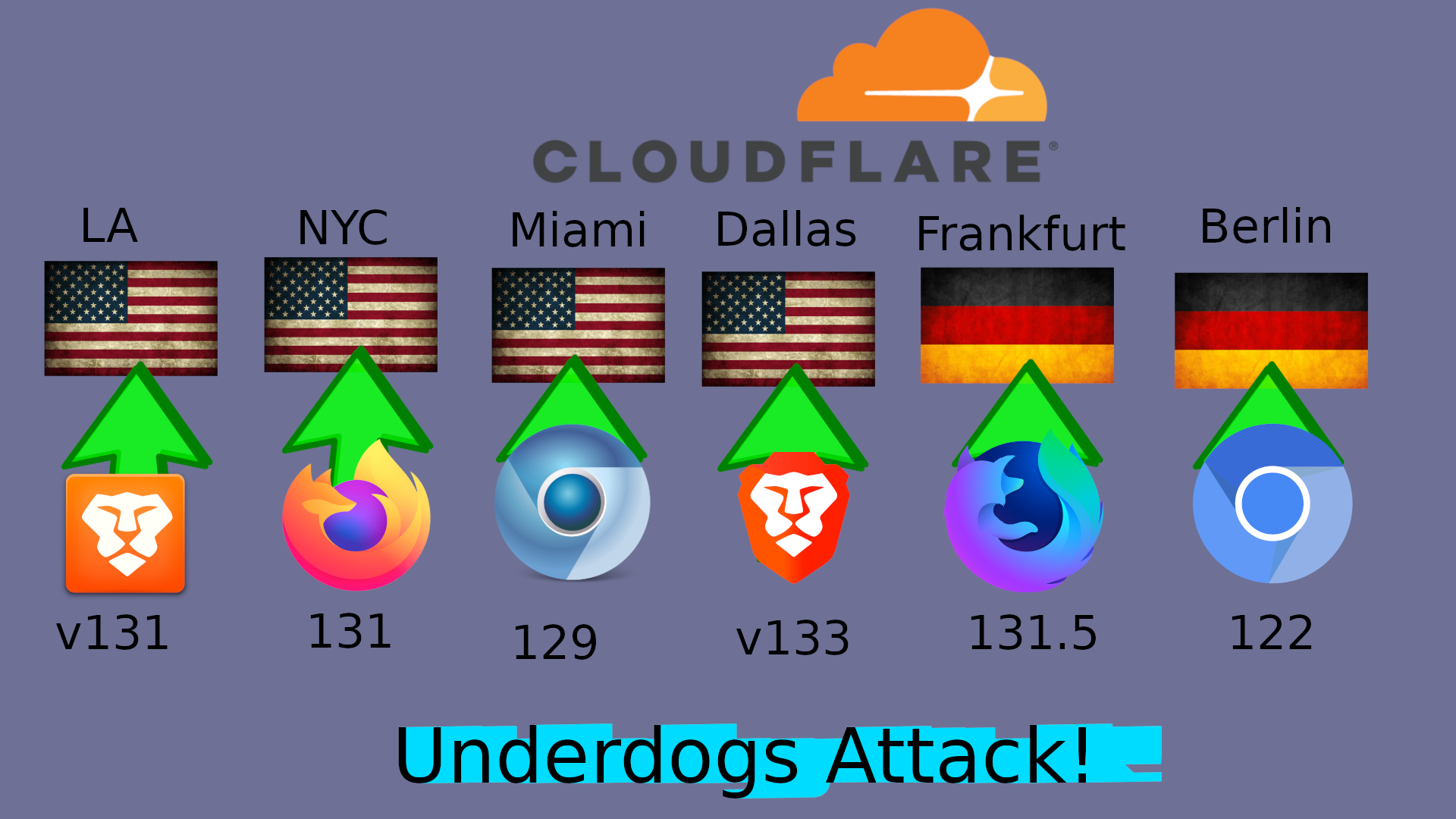
Cloudflare is Worse
Cloudflare is among the largest and most aggressive Fingerprinters.

According to Cloudflare’s blog, they do this every hour. Quote:
JA4 Signals are inter-request features computed based on the last hour of all traffic that Cloudflare sees globally. On a daily basis, we analyze over 15 million unique JA4 fingerprints generated from more than 500 million user agents and billions of IP addresses. This breadth of data enables JA4 Signals to provide aggregated statistics that offer deeper insights into global traffic patterns – far beyond what single-request or connection fingerprinting can achieve. [2]
Anything you do on Librewolf, Brave, or almost all browsers is very likely DOXXED if you ever logged into any Big Tech site in your real name ONCE.

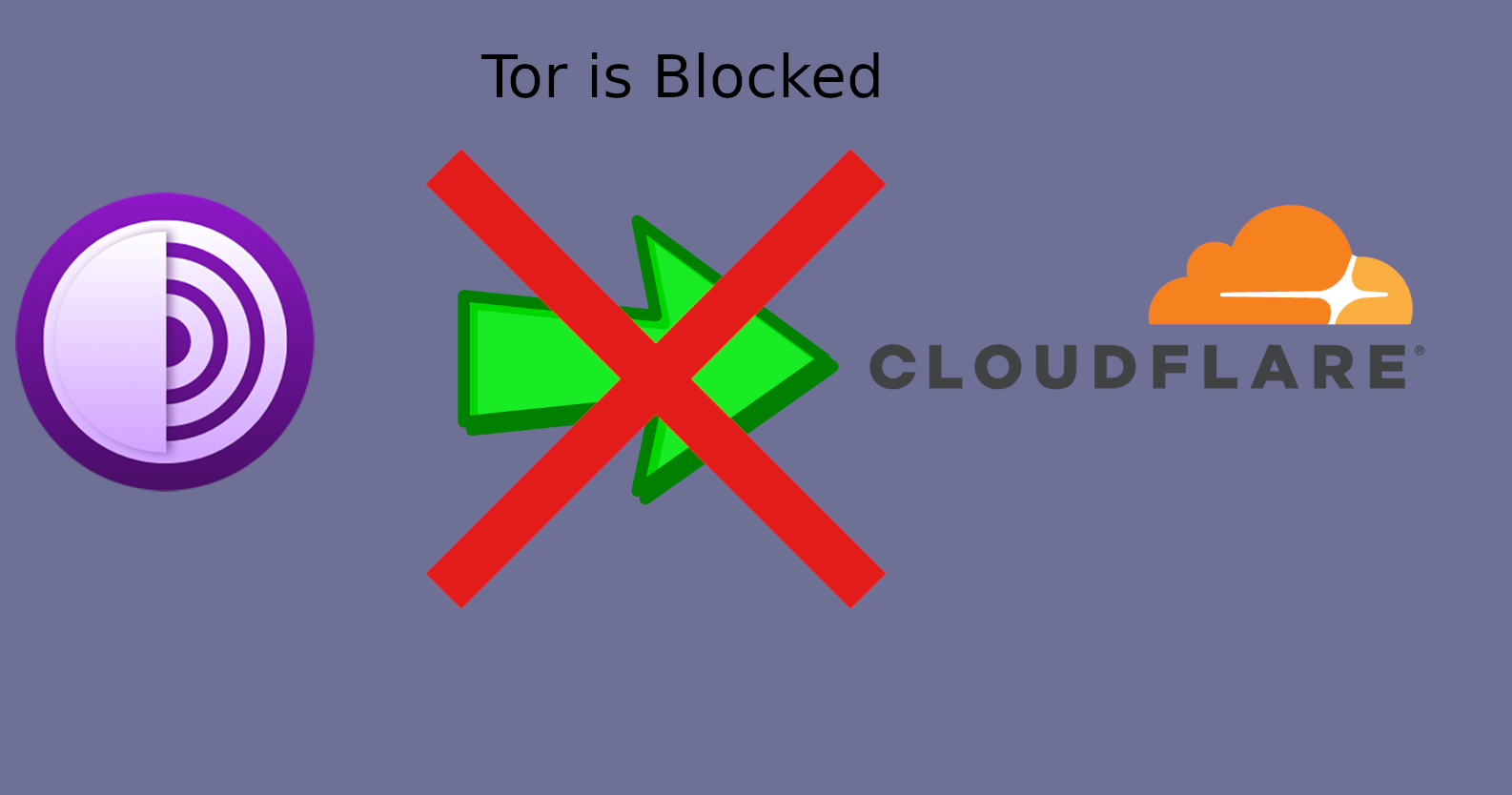
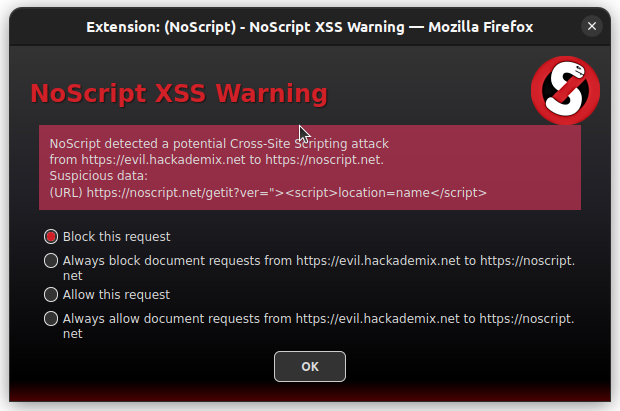
You’re saying, “Oh I’ll use Tor Browser”.
Well many sites block Tor. Or they won’t load right in Tor Browser.
In our previous article,
We went over how Mozilla’s Firefox has fundamental flaws that apply to Tor Browser:

Tor Only Works By Blocking Many Types of JavaScript
This causes websites to break.
So when you hit “Allow”, it fingerprints you.
The US Government made it.
You’re saying, “I’ll use many different browsers”.
Most browsers don’t hide your timezone, screen size, and have even weaker system-wide fingerprinting. So the more you switch to these weaker browsers, the more things you now have to hide.
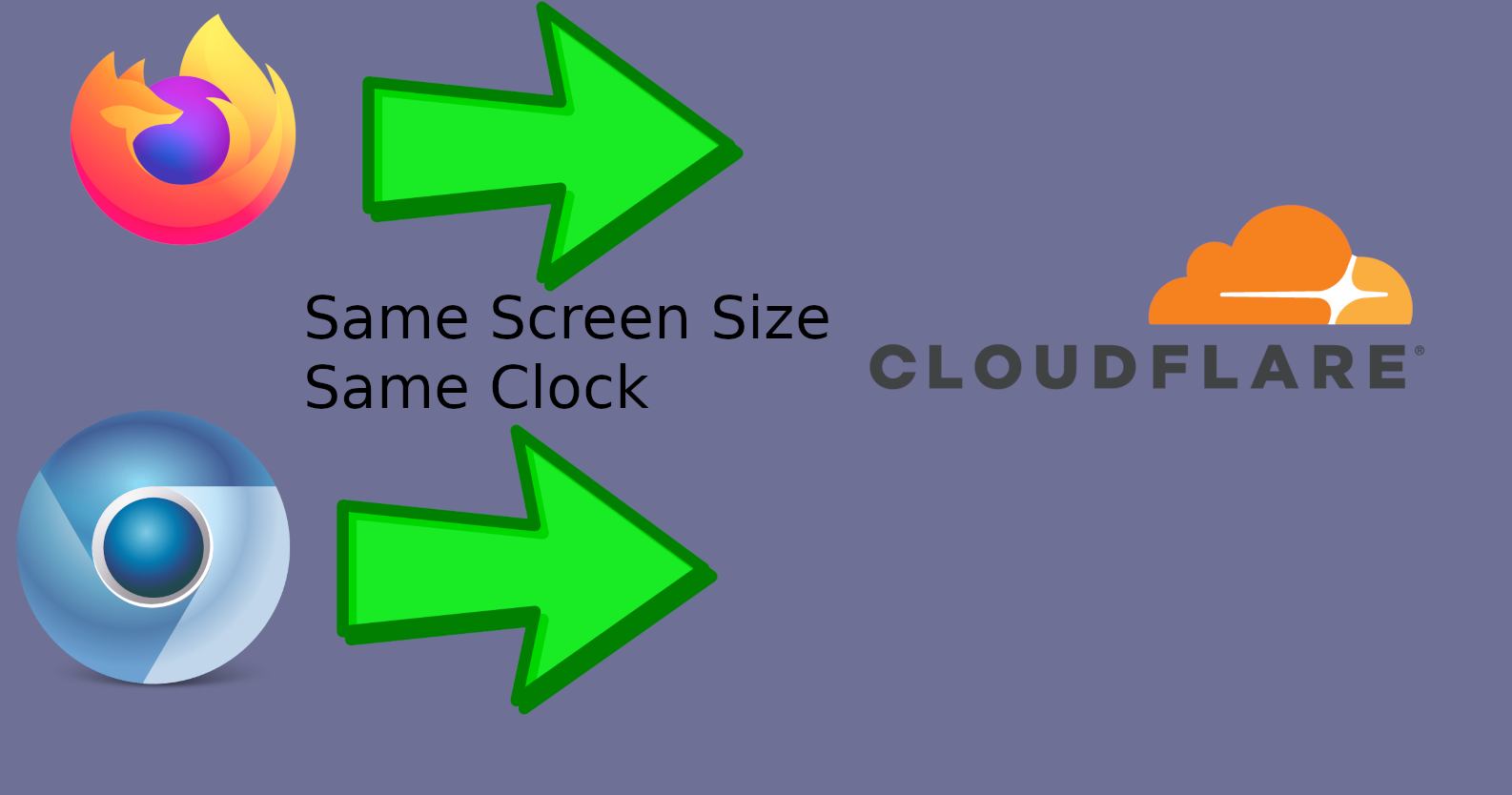
Fingerprint.com loves to catch you on timezone.
Quote from their marketing material:
"Quickly identify key characteristics of users such as a VPN with mismatched time zone" [3]
Their documentation confirms studying timezone mismatch, Quote:
Fingerprint's VPN detection is capable of detecting whether the user is in a different timezone compared to their originating IP address indicated by the timezoneMismatch flag. [4]
Fingerprint-com tells website operators to update data as often as possible:
We strongly recommend a maximum cache expiration time of 1 hour. [1]
You’re saying, “Oh I’ll change browsers, timezone, and screen size”.
Well, you still got the same VPN IP address pulling from Cloudflare at the same speed.
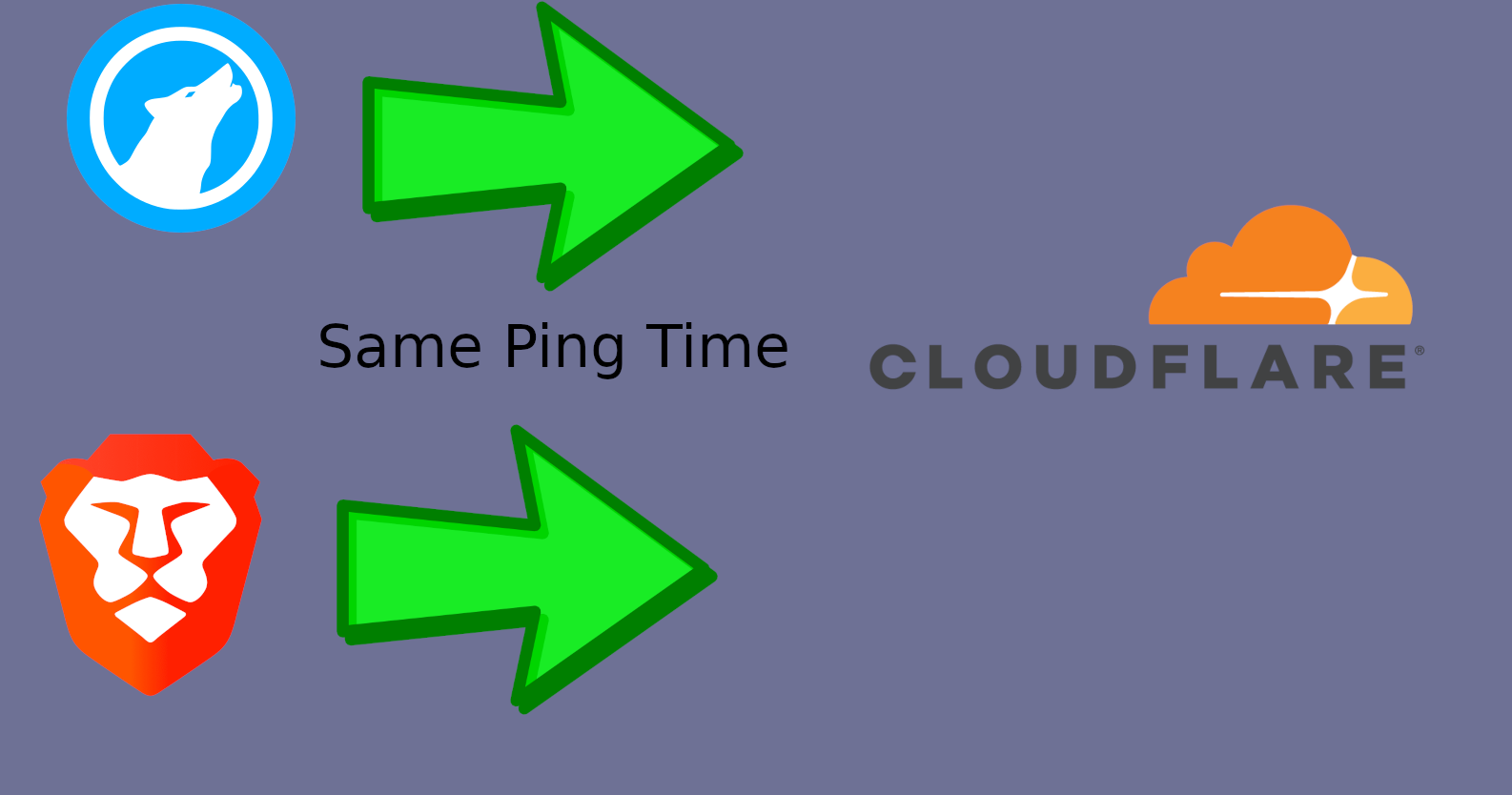
Not only does Cloudflare save your ping times, but they even let the web host view them in an admin panel
They advertise this in the Cloudflare Observatory, here’s a screen shot:
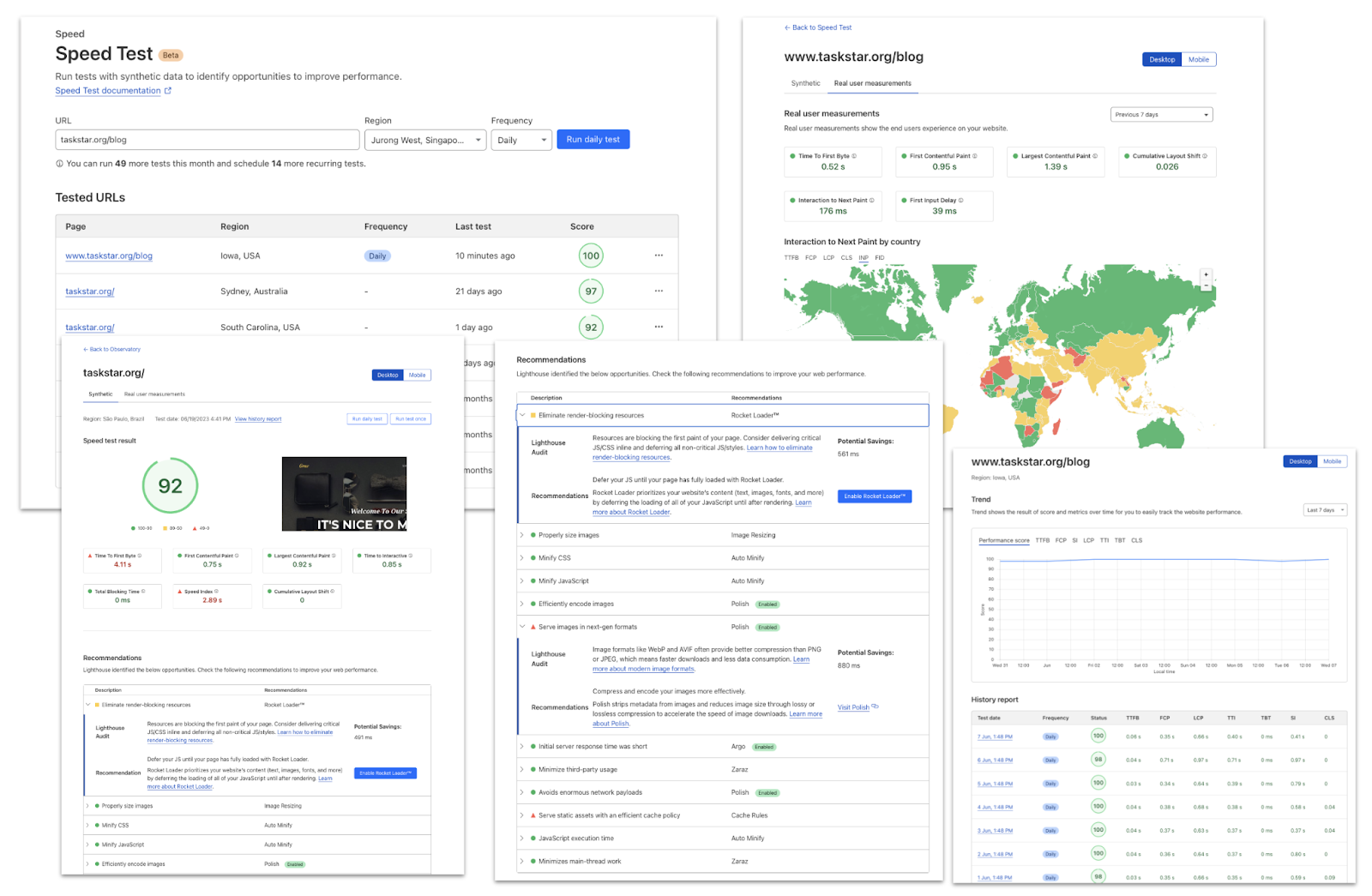
Cloudflare studies the “Origin Response Time”, Quote:
How long did it take to reach, and receive a response from your origin?
These and many other time based metrics are available in their APIs. Which they get from “Real-User Monitoring”:
Real-User Monitoring (RUM) involves collecting data directly from real users as they interact with the website, capturing their actual experiences in different environments and network conditions. RUM tests offer insights into the true end-user perspective.
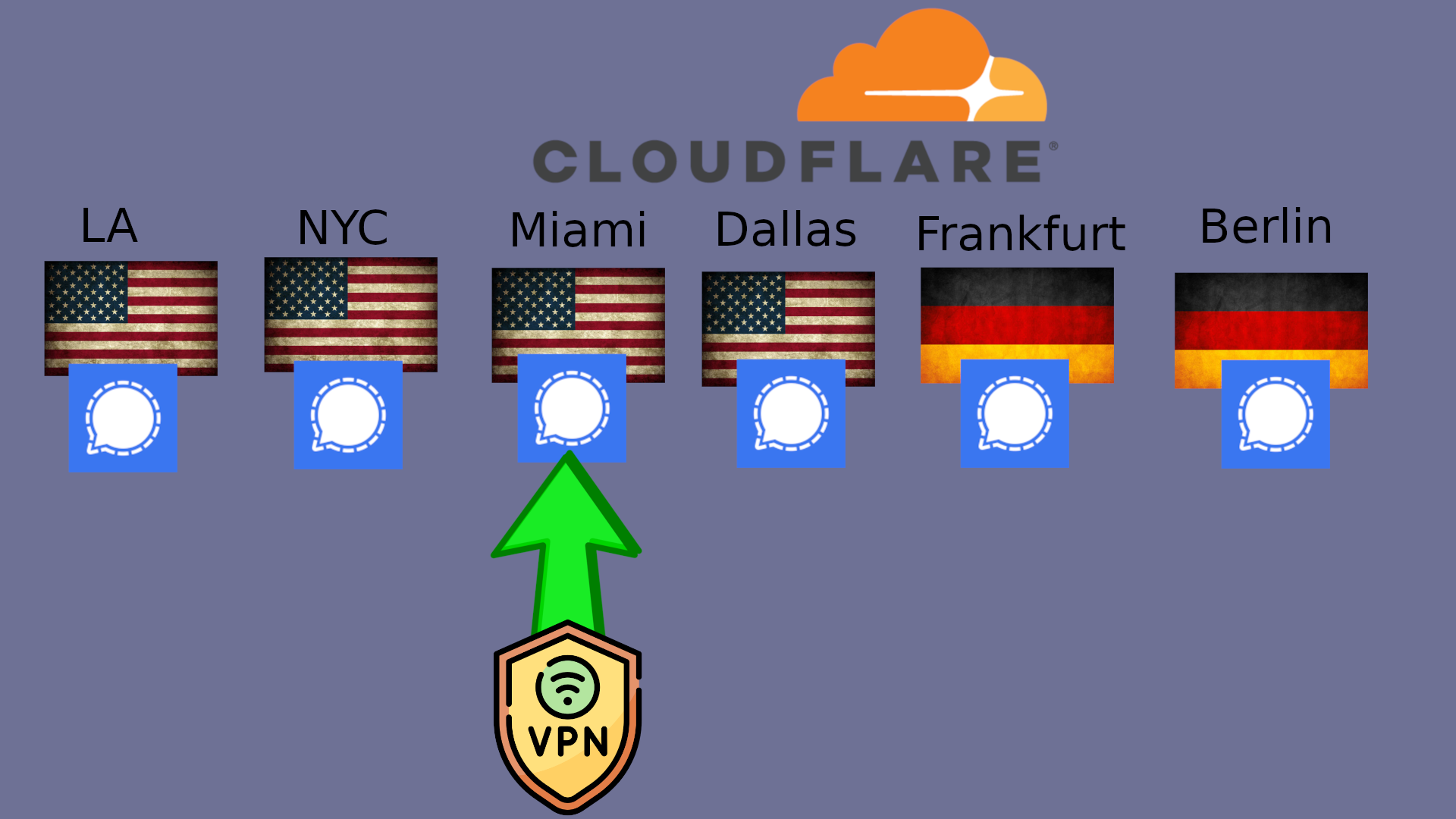
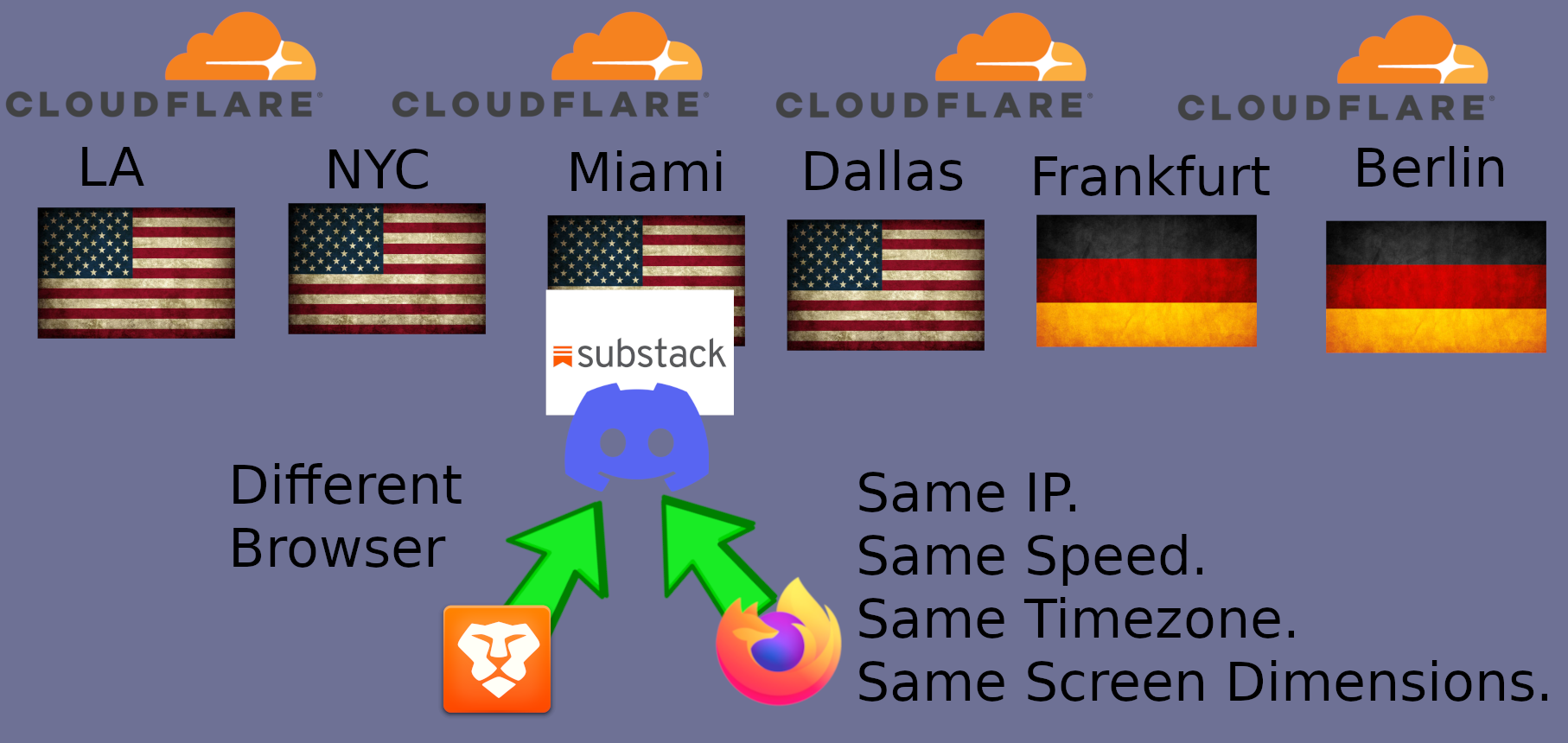
Content Delivery Networks (CDNs) match you to the closest server.
For example, let’s say your VPN exit is Miami. Then you connect to Signal via a Cloudflare server near Miami.
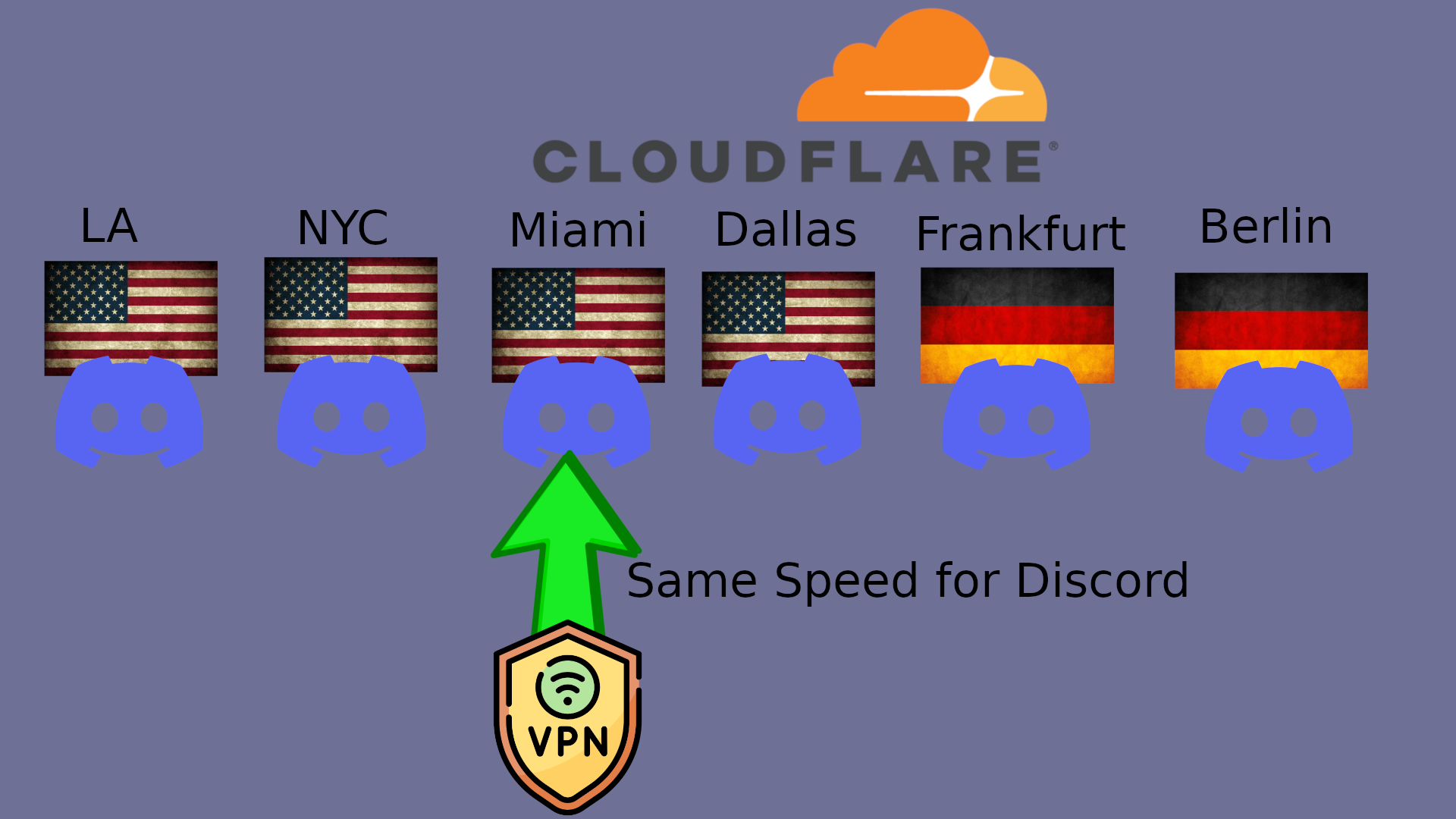
But if you use that same VPN exit for Discord, then the same Cloudflare server is also serving you Discord.
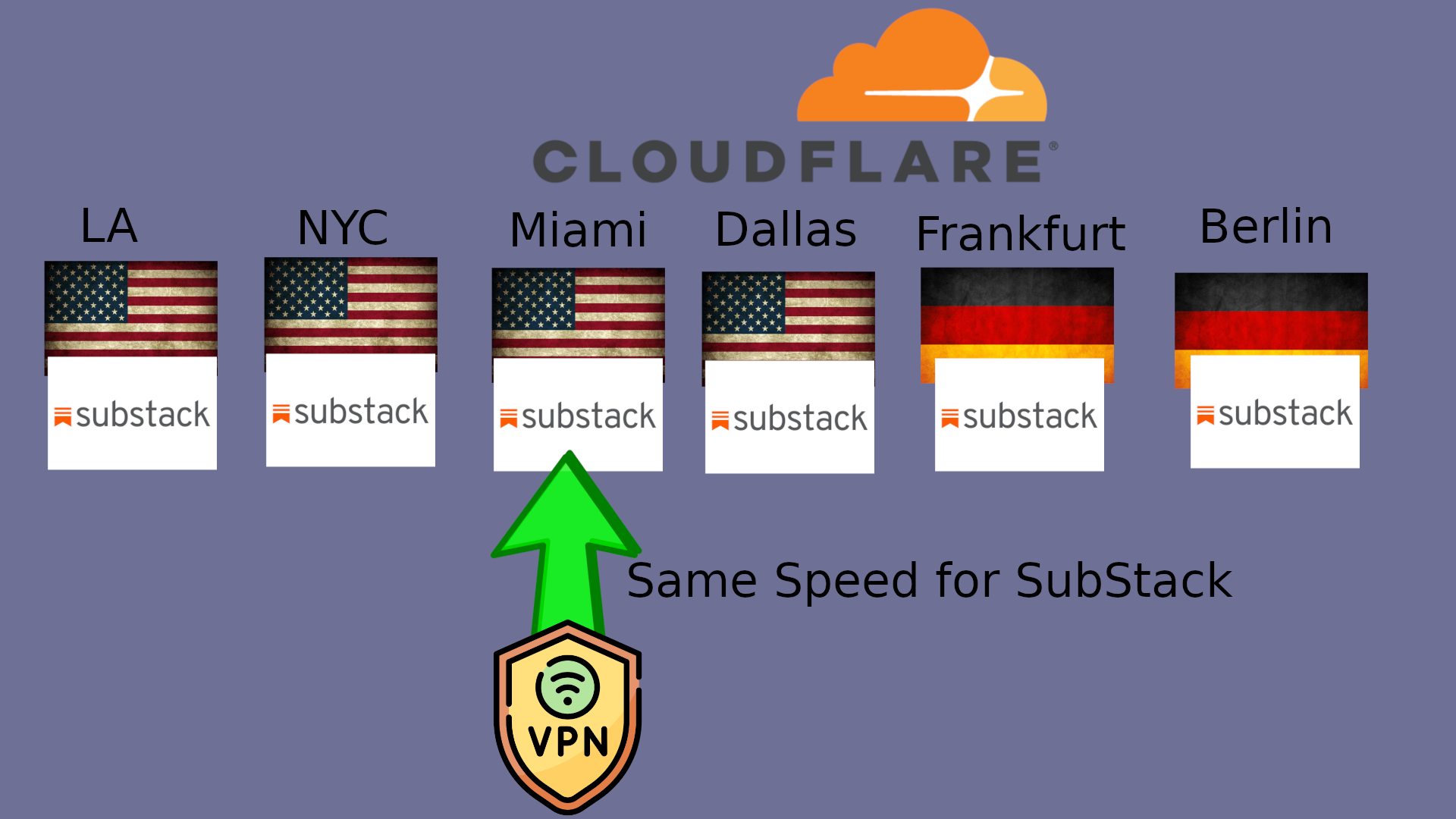
This means you’re connecting to all these services with the same (or very similar) speed. And If you login to Substack, then that speed is connected to your real financial info.
Fingerprint-com Uses Cloudflare Data!
Cloudflare has so much data, that Fingerprint-com has integrated CF Data into their product. Quote:
Insight and control over the identification requests that can be combined with other Cloudflare features like WAF or Analytics. [6]
And AWS and Microsoft:
Fingerprint-com Gets Data From Everyone, Quote:
We have developed integrations for popular cloud infrastructure providers such as AWS CloudFront and Azure Front Door, making integration into your website as simple as possible. [7]
Then because all these different websites share the same CDN servers,
Your VPN IP address is showing very similar (or exact) load speeds, between your “different fingerprints”
They are very interested in how many IP addresses, even if it’s a VPN:
The number of unique client IP addresses across all fingerprints in the last hour. Lower values indicate a higher number of distinct client IPs associated with the fingerprint. [5]
The sheer amount of websites using Cloudflare makes this scary. Quote:
The number of networks Cloudflare sees actively using this fingerprint. The number of Cloudflare sites that see traffic from this fingerprint. The frequency that fingerprint requests caches content and generates errors. [8]
Plus as we covered in our other article, there are cross browser identifiers such as fonts or WebGL.
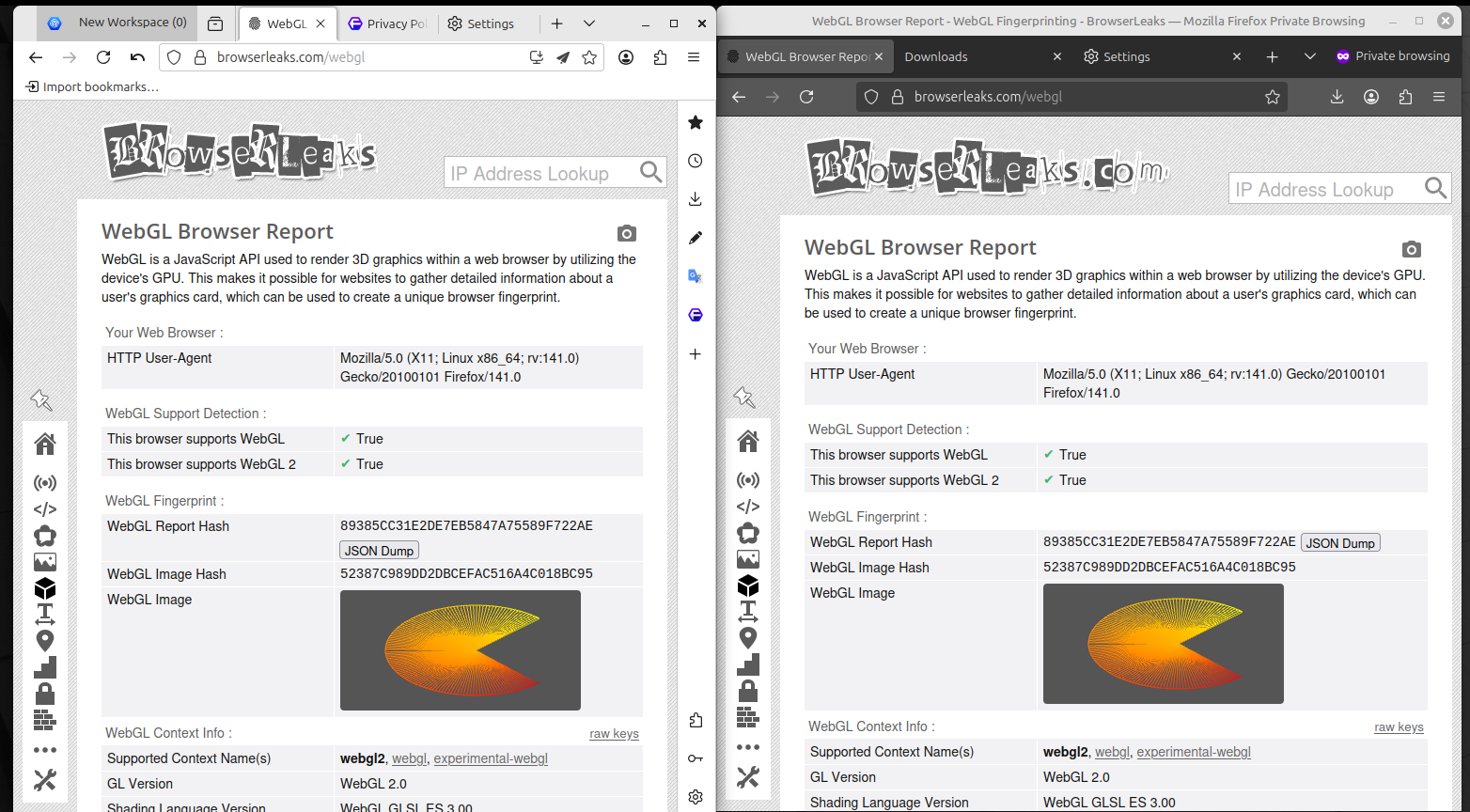
Here’s the point:
If you say “I’ll just use different browsers”, there’s a high chance of leaking across profiles.

Solution:
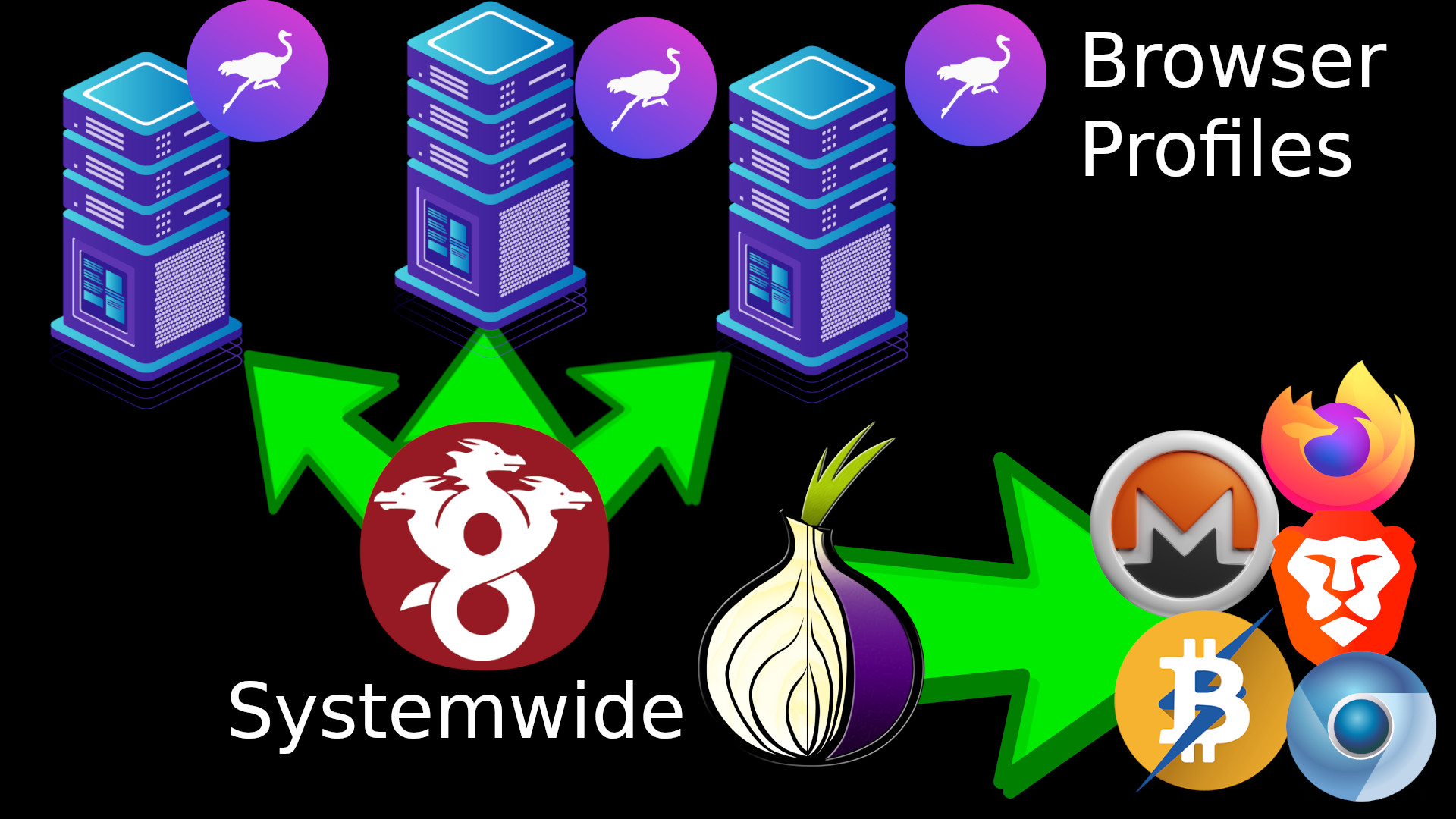
Simplified Privacy’s HydraVeil allows you in one easy click to launch isolated profiles that prevent you from leaking by forcing each fingerprint through a different VPN or Proxy IP address.
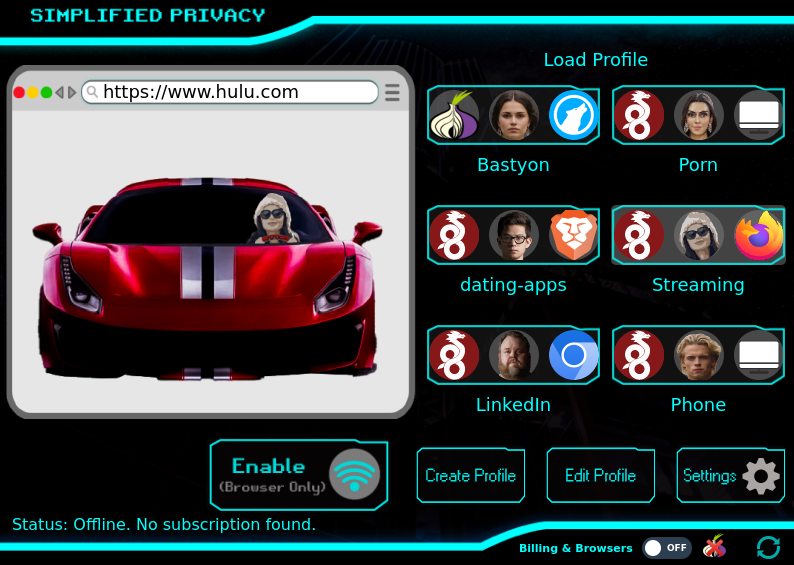
Each profile gets its own IP address, giving you a new load speed.

With a matching timezone, realistic screen size, and browser version… these fingerprints are undetectable!
Websites perceive it as real, so they can’t stop you.

With micro-payments in Monero or Lightning, you dodge any identity ties,

Simplified Privacy has no bank accounts.
Using Nostr, Bastyon, Session, Arweave, and PGP-crypto-arbitration, we are not defined by the dirt upon which we stand,

In the movie the Matrix,
Morpheus gives Neo a choice,

But Unlike, the Matrix,
In the Real World, you can learn the truth, and still go back,

Don’t go back.
Where the AI feeds off your data every 5 minutes.

Choose Simplified Privacy.

Get your Questions Answered
[Docs Link]
Footnote Sources:
If you really want to learn and take your privacy to the next level, Learn about HydraVeil, Access our VPN, and subscribe to our new content via: Arweave Video RSS, Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts
Tor Sync & Tor Profiles Fixed | Release 2.2.1
Faster Initial App Startup
[SP]
Jan 20, 2026

New Sweden VPN Node
Run by AilliA of XMRBazaar
[SP]
Jan 18, 2026

1 Second Saved | Release 2.1.4
Faster Initial App Startup
[SP]
Jan 16, 2026

It takes a lot to admit you're wrong
But that's what I'm doing today. (v-2-1-1 release)
[SP]
Jan 9, 2026