Web Browsers Can't Resist
LibreWolf, Mullvad, & Tor Browser all fail for this reason..


Full Dark Fi Quote:
"The Web is monopolized by Big Browser. We essentially have three companies developing infrastructure (web browsers) that the entire population of the Internet blindly uses for all aspects of their lives. Personal data is stored everywhere without concern for privacy or security." [2]
Conflict of Interest
Google’s revenue is ads. That’s a conflict of interest to design a browser to hide your activity from Google, even if the direct Chrome spyware is removed.
I’m NOT talking about Chrome’s calls to Google, I’m talking about how the underlying browser engine system is designed.
Nick

Nick @ The Linux Experiment:
You only have two viable choices for browser engines on most platforms: Firefox, with its Gecko engine, and everything else, based on Blink. Mac users have the option to use Safari as well, based on Webkit. That’s right, every other browser out there depends on Blink (most of the time being based on Chromium, the open source version of Chrome). Opera ? Ditched its own engine ages ago. Vivaldi ? Same. Brave browser ? Blink. [3]
Firefox
Mozilla’s revenue is Google paying them. That’s a conflict of interest to hide from Google as a Google alternative.

DigDeeper Quote:
"Firefox sends 112 requests to various moz domains during your first run of it. But that's not enough for them. They have this crap called Firefox Glean that reports almost every interaction you have with Firefox to Mozilla, with a browser session ID, unique user ID, precise timestamp and various system information included. These requests happen anytime you visit a menu (Addons, Passwords, Settings, etc), change a preference, open a new tab, click through one of the four prompts that appear when you first run the browser, or do literally anything else. And every time you turn off Firefox, it sends a giant request to Mozilla containing information about pretty much the entire state of your browser at the moment of closure. [4a]
Can’t Hide True Nature
All web browsers can not hide their true nature, including Firefox forks. They can only BLOCK many types of JavaScript or web techniques in order to prevent fingerprinting.
DigDeeper Quote:
On Tor Browser:
So instead of just disabling JavaScript by default, they [Tor Browser] try to submit fake data for every value that could possibly be used to fingerprint you. This is just enumerating badness and inferior to the uMatrix approach of blocking it all by default. It is impossible to have a truly mitigated browser when you allow websites to do whatever they want; but the TOR Browser - hoping to avoid "site breakage" - is trying that, regardless. When it is the bloated sites and the technology they are based on that are the problem. [4c]
Daniel Micay shares this view:

Same Quote in Text Form:
"Fingerprinting is not something any mainstream browser has meaningful defenses against, including Firefox. Even for the Tor browser it hardly accomplishes much with JavaScript enabled." [13]
Not just Tinfoil hats
Some will say that Daniel Micay and DigDeeper are extreme. But even the creator of Arkenfox, who worked with the Tor Project and Firefox on fingerprinting, and has a much more tame view, said:

Thorin Oakenpants Quote:
Owner of arkenfox, Worked with Tor Project and Firefox on fingerprinting for 7 years
"The only way to protect against advanced scripts is to be in a crowd. If you do nothing, you're already unique" [9]
Break Services
The only way browsers can stop surveillance is blocking many types of JavaScript. But Blocking causes websites to break, not only because the devs don’t design for them, but you’re cutting off the web apps’ money-maker, which is user data.

Luke Smith Quote:
Soydevs are destroying the internet and now preventing me from eating. The internet is becoming so prohibitively bloated that doing very basic normie life things has become a huge affair and inconvenience. I just want to consooom informational content on the internet without being overburdened by trackers, ads, server-side scripting and other trash. [10]
Luke Smith’s blog comments on how devs focus on Chrome.
This means you can’t even use regular Firefox on some web apps.

Nick @ The Linux Experiment:
"Blink is fast becoming the only engine web developers even test on" [7a] "Giving Google the reins of the engine that allows people to display and interact with these webpages means that, if they were so inclined, they would be able to deprecate features, outright kill any technology they don’t like, hamper any technological advance a competitor could try to make, and generally dictate what you can, or can’t use when building your websites." [7b]
Despite most websites being designed for Chrome/Blink,
LibreWolf, Mullvad, and Tor Browser are pushed forward as the only solutions.. But they suffer the baggage of Firefox.
Librewolf:
DigDeeper Quote:
"LibreWolf is nothing special.. It's nothing more than Firefox with a few settings changed" [4b]
Daniel Micay Quote, GrapheneOS developer:
"Firefox is easier to exploit, lots more low-hanging vulnerabilities and a half-baked weak sandbox. On Android, it has no sandbox at all. [13]
Mozilla is hosted on Google Cloud.
Everyone’s favorite place to monitor packet speeds
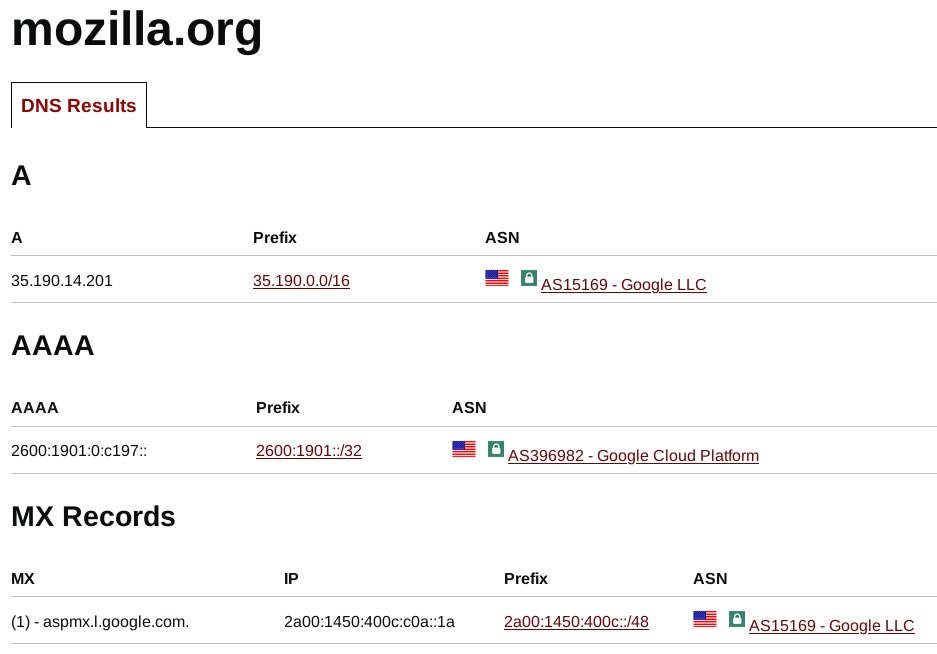
Negligent Librewolf developers use the CIA contractor Amazon. You can’t have privacy software, if it’s being served to you by the CIA’s database.
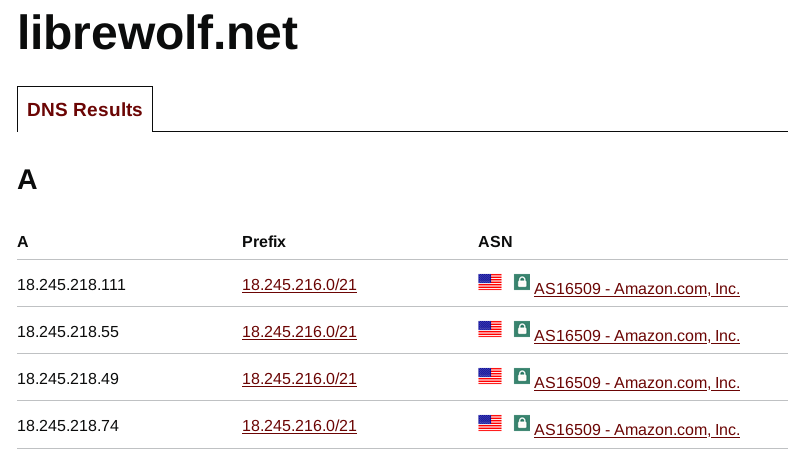
I ran WireShark to capture the packets, and when Librewolf is opened, it hits up Google Cloud, Cloudflare, and more.
Even if I disable auto-updates for the add-ons and the browser.
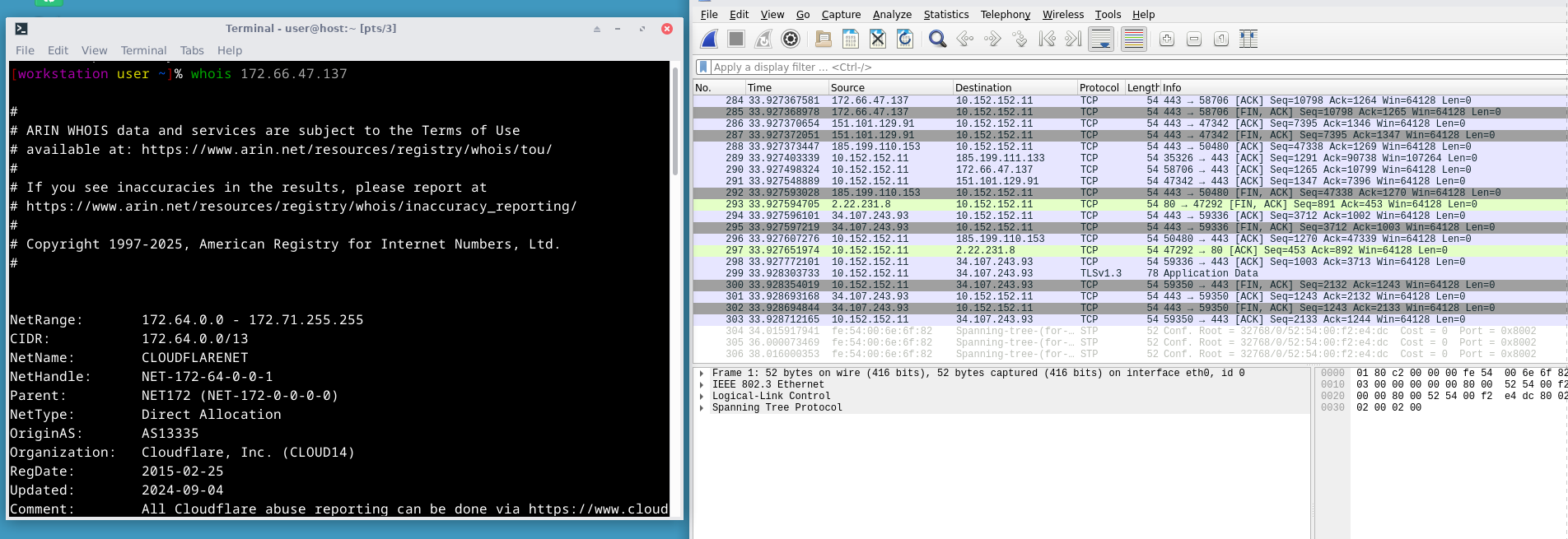
Even if we forgive connections against my will at the start,
Why does Librewolf need to connect to Google Cloud when the browser is CLOSED?!
Maybe that’s why they name it after a wolf, you’re howling your fingerprint each time,
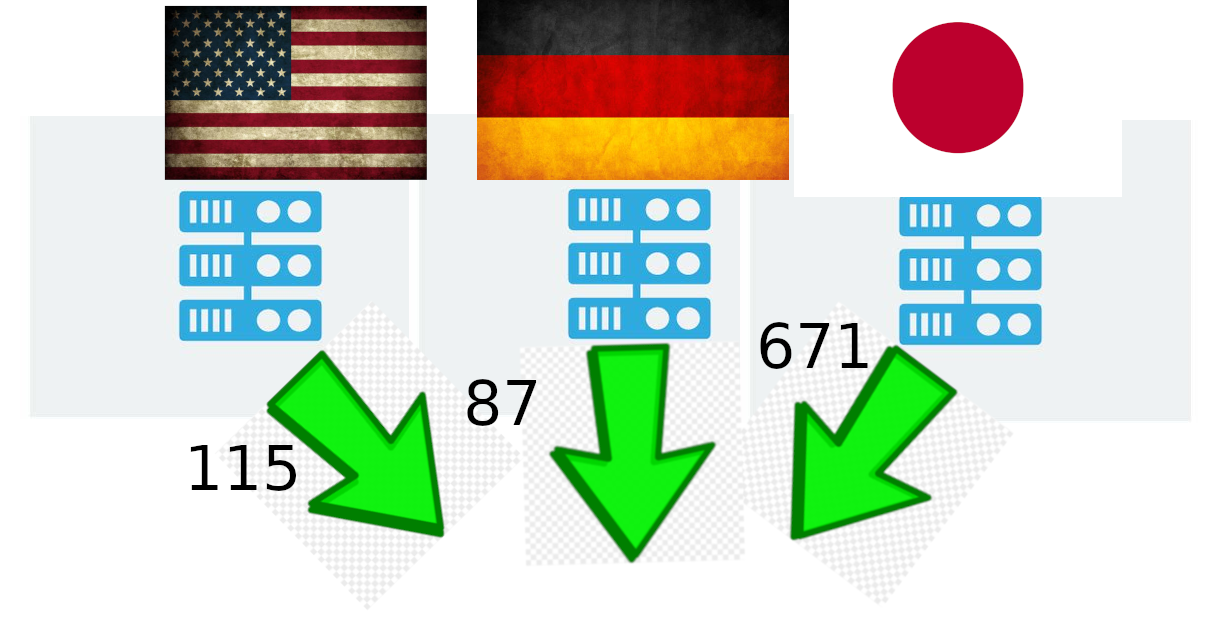
Content Delivery Network (CDN)
You’re hitting up the same companies’ CDN servers, that are then serving you the websites you’re trying to hide from. And CDNs match you with their closest server, so it’s likely the same ping time for most services.
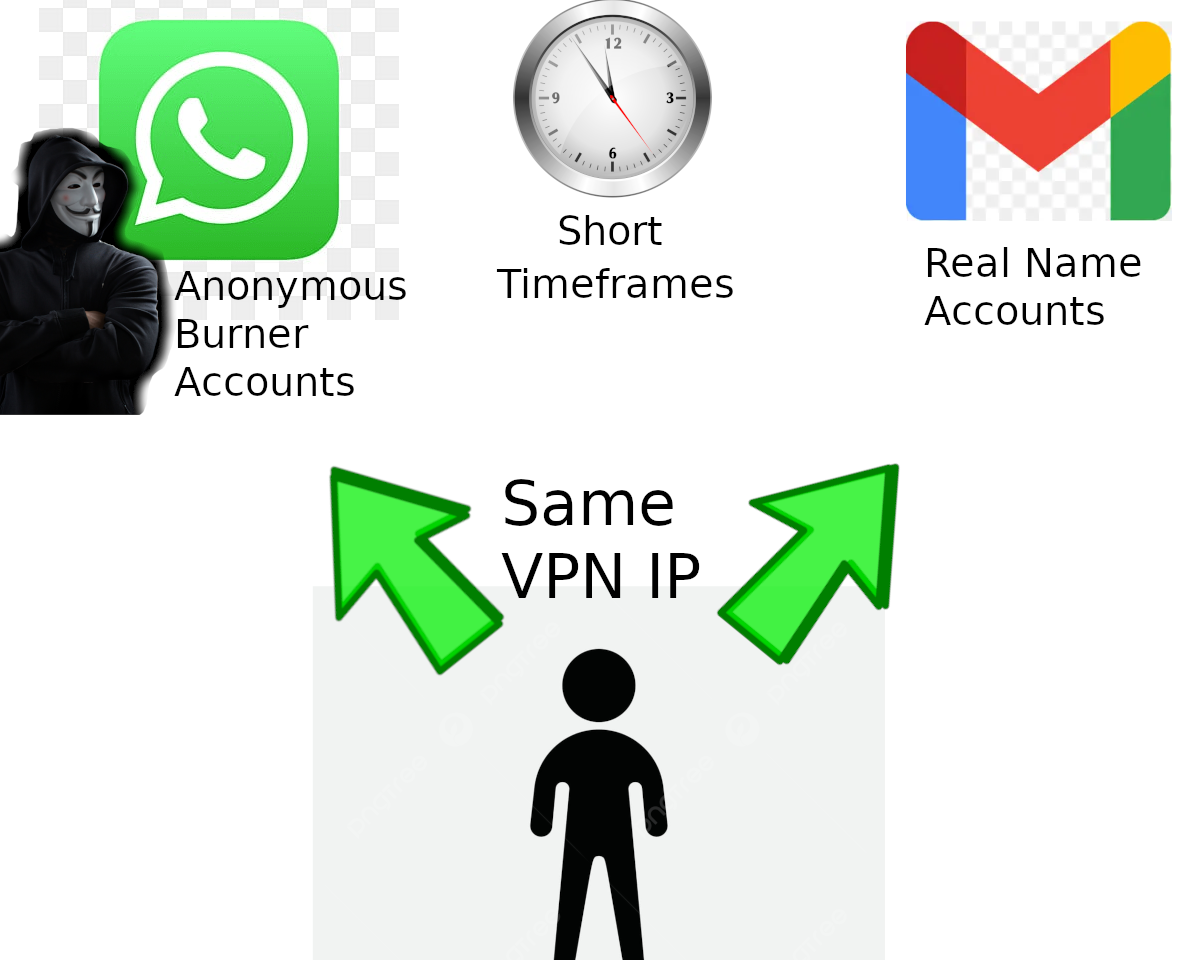
Remember our interview with the former Cybercrime Detective?

Travis West, Law Enforcement Quote:
"A common mistake I have seen people who want to remain anonymous online make is using a VPN consistently with burner accounts, but then they use the same VPN with the same IP address at around the same time to access accounts already associated with them, such as their online banking or a Gmail they have used since they were a teenager. So if they were targeted by the State for whatever reason already, their IP address logs for their known accounts would have the same IP addresses as the burner accounts at around the same time. If the timing is less than 10 minutes apart, and even if this occurs just once, there will be assumptions it is the same person."
Source: Full interview
AI will make this worse,
Harvard Professor & Cybersecurity Expert Bruce Schneier,

Full Bruce Schneier Quote:
A.I. is about to change that. Summarization is something a modern generative A.I. system does well. Give it an hourlong meeting, and it will return a one-page summary of what was said. Ask it to search through millions of conversations and organize them by topic, and it’ll do that. Want to know who is talking about what? It’ll tell you.
Mass surveillance fundamentally changed the nature of surveillance. Because all the data is saved, mass surveillance allows people to conduct surveillance backward in time, and without even knowing whom specifically you want to target. Tell me where this person was last year. List all the red sedans that drove down this road in the past month. List all of the people who purchased all the ingredients for a pressure cooker bomb in the past year. Find me all the pairs of phones that were moving toward each other, turned themselves off, then turned themselves on again an hour later while moving away from each other (a sign of a secret meeting). [14]
You think I’m being a tinfoil hat extremist?
But even developers of “more mainstream” browsers disagree with the settings.
Thorin Oakenpants Quote, Arkenfox dev working w/ Tor Project & official Firefox:
"LibreWolf has Conflicting preferences, outdated preferences, and no clear strategy" [9]
Tor is a little better but,

DigDeeper Quote (On Tor Browser):
Tor Browser is an auto-updating piece of trash. Default addons include NoScript, which is much inferior to uMatrix. Yet, the TOR Project discourages modifying the addon setup, even though the whole basis for this has been refuted by Moonchild. [8c]
He elaborates further on Tor Browser:
Tor Browser is still dependent on the evil Mozilla - which means that when a bug happens (like, the one that disabled all addons) TB is also affected, and its security laid bare. [4c]
Manfred Paul hacked Tor Browser in 2022 to leak the real IP address. [11]
Mozilla Firefox has a long history of being vulnerable to malicious JavaScript injections. Malicious script hacks caused Tor to have to patch to correct them in 2019 [5], 2016 [6], and 2013 [8].

Mozilla’s new CEO wants to focus on AI. With her background being eBay.

eBay is one of the most privacy invasive companies,
eBay bans Tor, restricts many VPNs, and has harsh verification requirements, that even includes research if the SMS number is being re-used for other names on other services. Then eBay outright sells this user data..
Yet now her decisions will be Tor’s infrastructure.
Daniel Micay says:

Daniel Micay, GrapheneOS developer:
"Exploitation is also far easier, and even more so for the Tor browser compared to regular Firefox. There is no sandbox containing anything afterwards beyond the app sandbox. All sessions and data for other sites is compromised." [13]
If you won’t hear from hackers or developers, then hear it from the corporations that sell surveillance. Mullvad Browser & Tor Browser both rely on letterboxing.
Yet Fingerprint Pro sells fingerprinting to corporations through Mozilla’s letterboxing. [15]

Tor, Mullvad, LibreWolf, and Brave browsers all depend upon Firefox’s Gecko and Chromium’s Blink engines, but Mozilla and Google created the toolkits and technology for web devs to do surveillance itself.

[1]
Change is Possible

Real Solutions
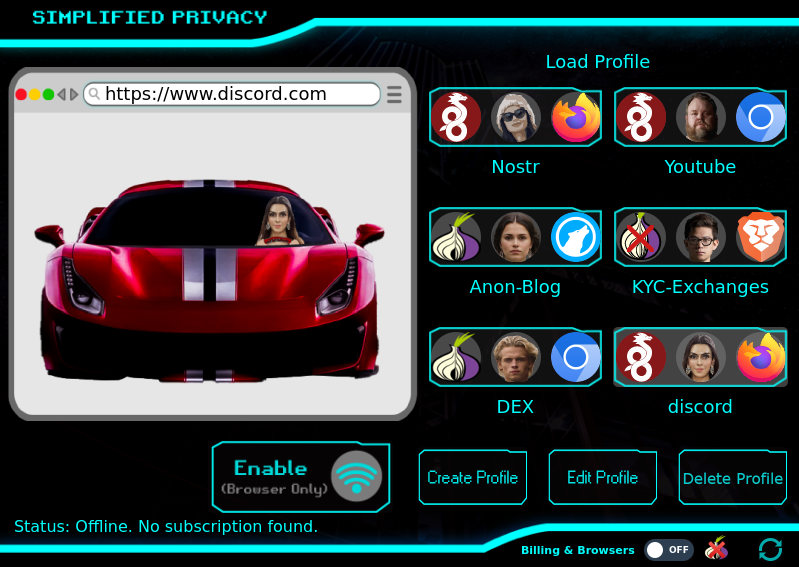
Simplified Privacy’s HydraVeil app gives you multiple identities that are easily managed and launched in one-click. These work OUTSIDE the browser, to keep the browser dumb.
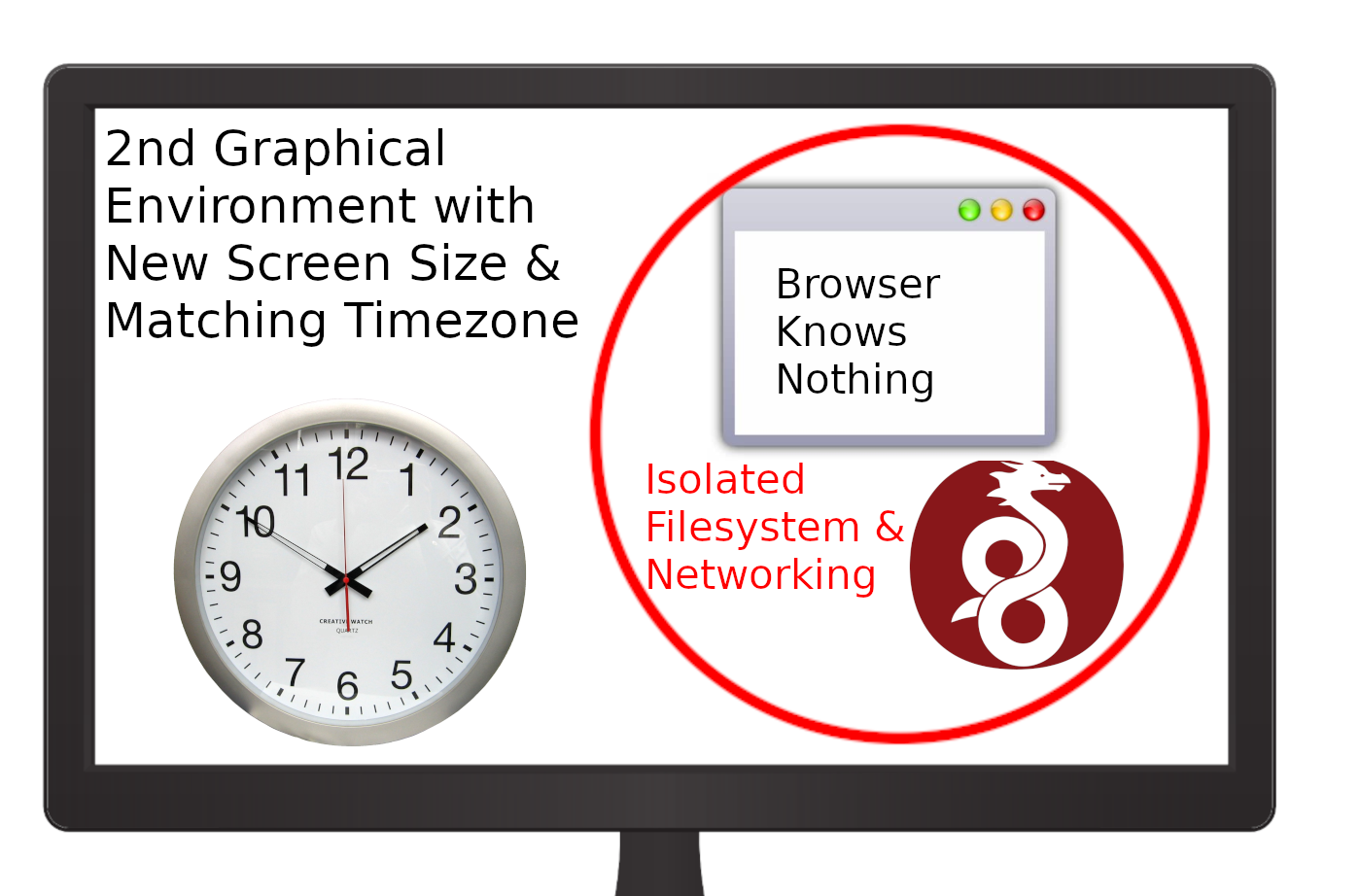
Browser Knows Nothing
We assume the browser will tattle-tale and spill the beans, so we contain it from seeing your real timezone, screen dimensions, filesystem, or anything of value.
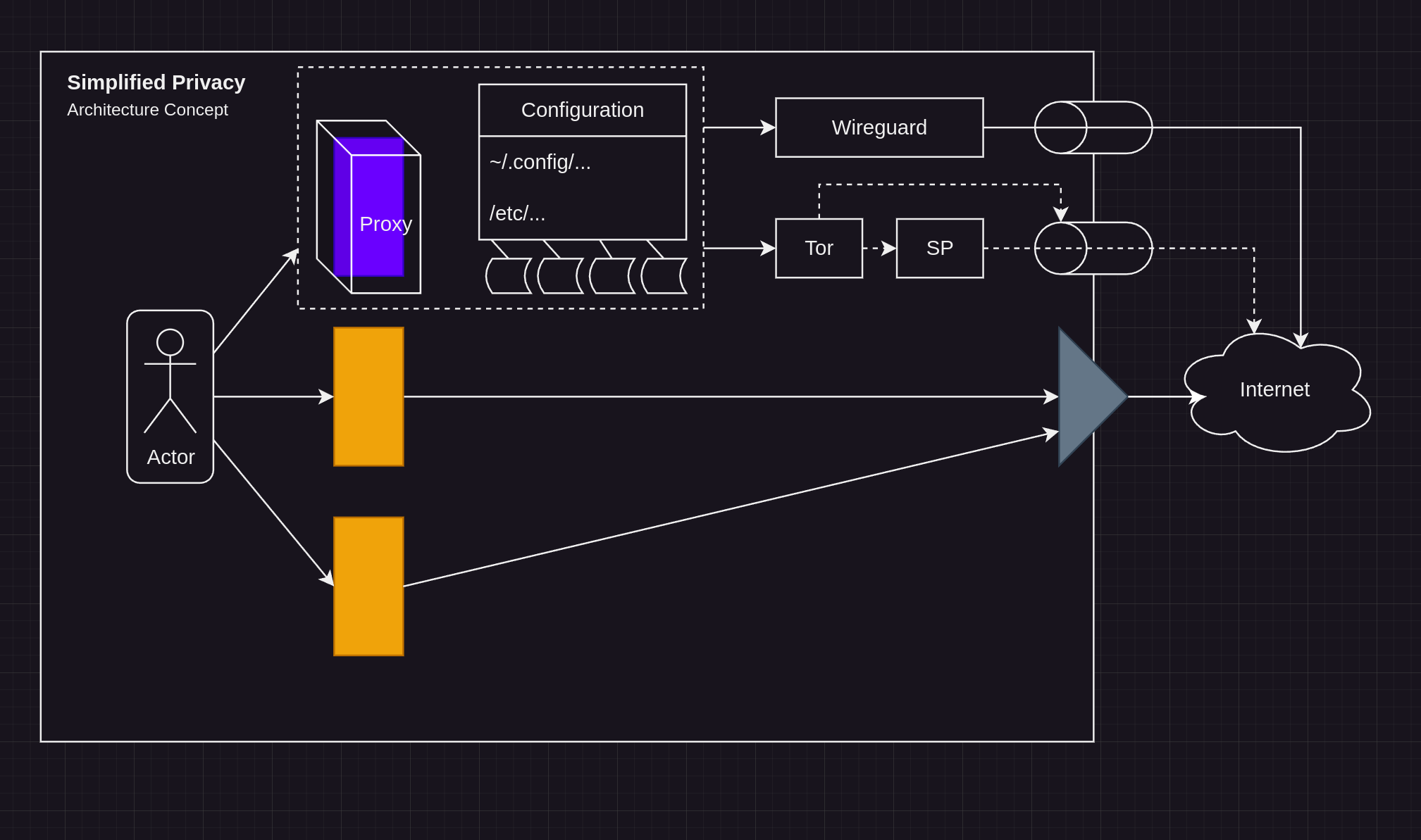
Advanced Security
We isolate the networking outside the browser in a new environment. You don’t need to know the technical details to use it, but if you want them, here’s a: Link
Faster than VMs
Our app is faster (and easier) than virtual machines, but gives you just as much punch.

Hide Tor IPs
You can even use Tor, when Tor exit IPs are blocked, by routing it through a cheap burner proxy,
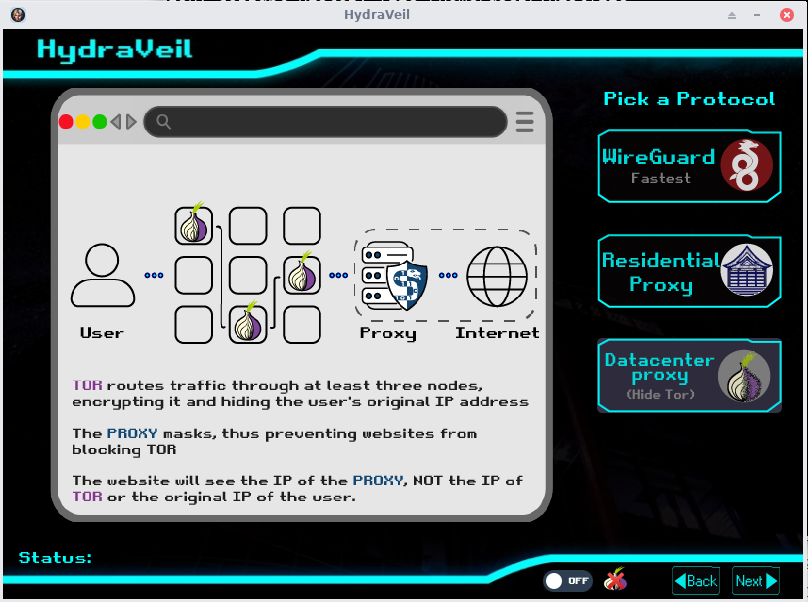
So you still get the privacy of Tor’s routing,
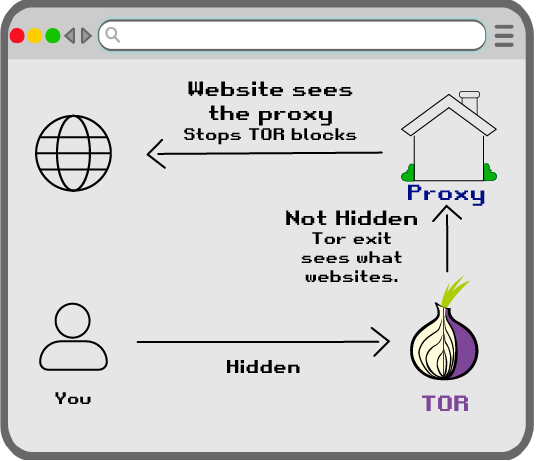
But without being forced to rely on Tor browser. This has a built-in 2nd Linux distro of browsers, configured to use (your choice of) Tor->proxy or WireGuard.

Easy to Use
Our app is like driving a car. You can study the open source code if you’d like.. But you don’t need to know how it works under the hood, to hop in and drive.
It’s actually much harder to first test if a website works in Tor Browser, then test if it works in Librewolf, and finally give-up on Firefox.
It’s harder to install KVM virtual machines or QubesOS with different VPNs.
Now anyone can get privacy and security, even without a lot of experience.

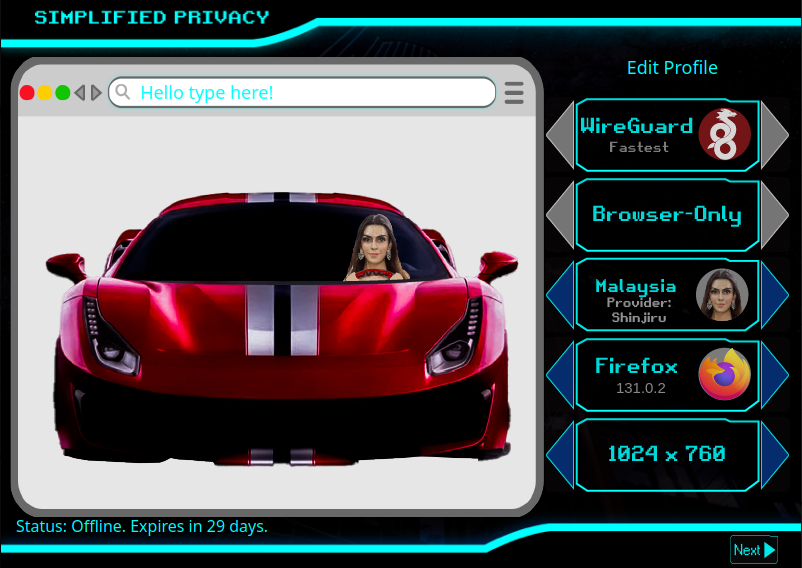
HydraVeil’s Fingerprint Profiles:
In one click get a new:
Browser Version
Screen Size
Ping time & IP address
Matching Timezone (to IP)
& it’s Faster than VMs
So you can use Tor:
Without Tor Browser
Without blocking or restricting JavaScript
When Tor IPs are blocked
When Firefox won’t work for websites
Or with Fast WireGuard Options.
Click to Learn more:
Get Privacy
Sources
Note: These quotes were used without permission, and may lead to direct criticism from the original author. This article’s sources can be found here: [link]
If you really want to learn and take your privacy to the next level, Learn about HydraVeil, Access our VPN, and subscribe to our new content via: Arweave Video RSS, Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts

How HydraVeil Works
Technical Deep Dive: The Yellow Paper
[SP]
Feb 20, 2026
Website Makeover
Learn the Concepts with Awesome Visuals
[SP]
Feb 14, 2026
Tor Sync & Tor Profiles Fixed | Release 2.2.1
Faster Initial App Startup
[SP]
Jan 20, 2026

New Sweden VPN Node
Run by AilliA of XMRBazaar
[SP]
Jan 18, 2026