How a Nostr VPN Works
Node operators verify their identity?!

WireGuard uses ed25519 keys to establish a tunnel.
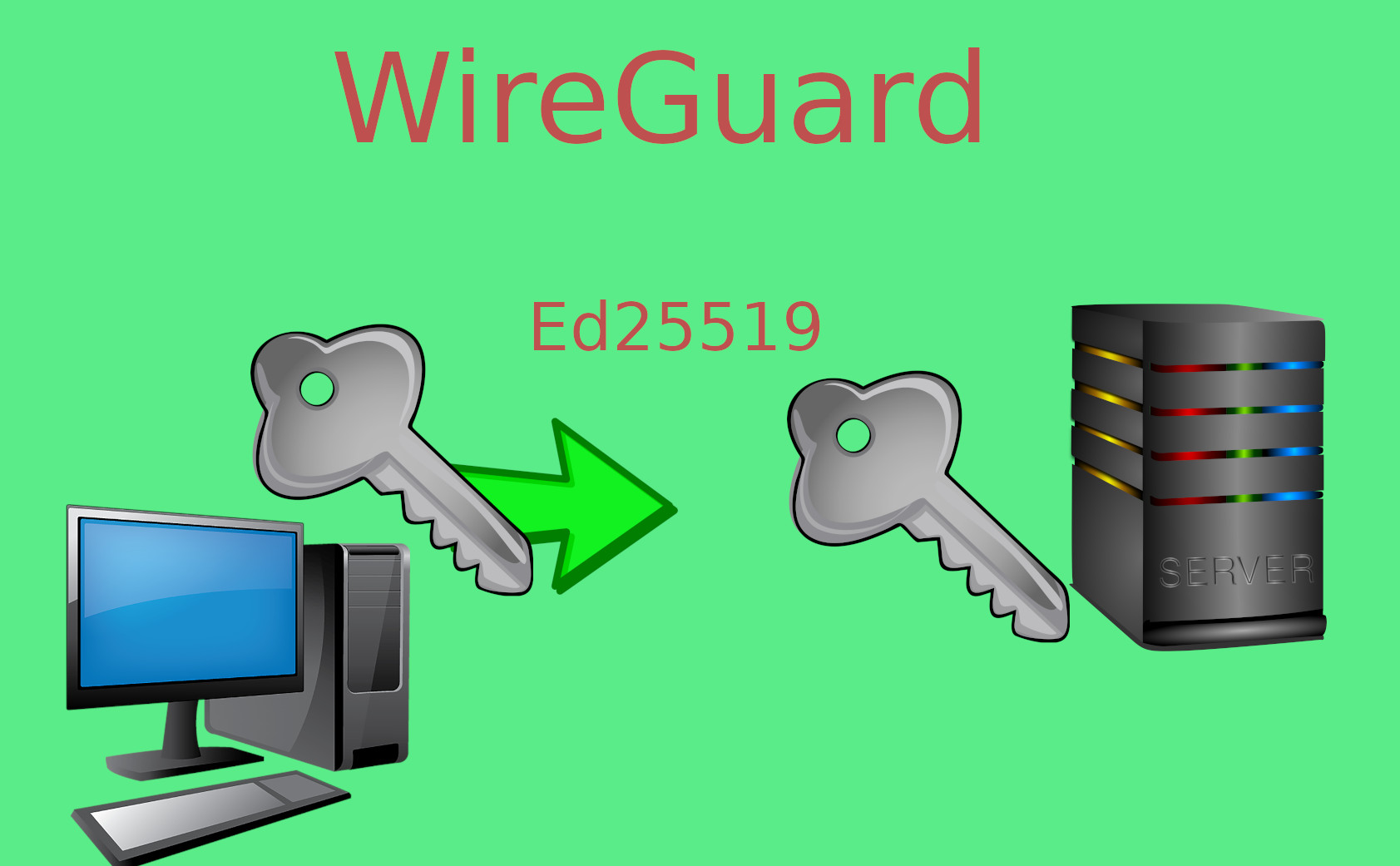
But that only identifies a server.
We want to identify an operator with Nostr keys. The problem with doing this directly is it leads to spam, as endpoints change.
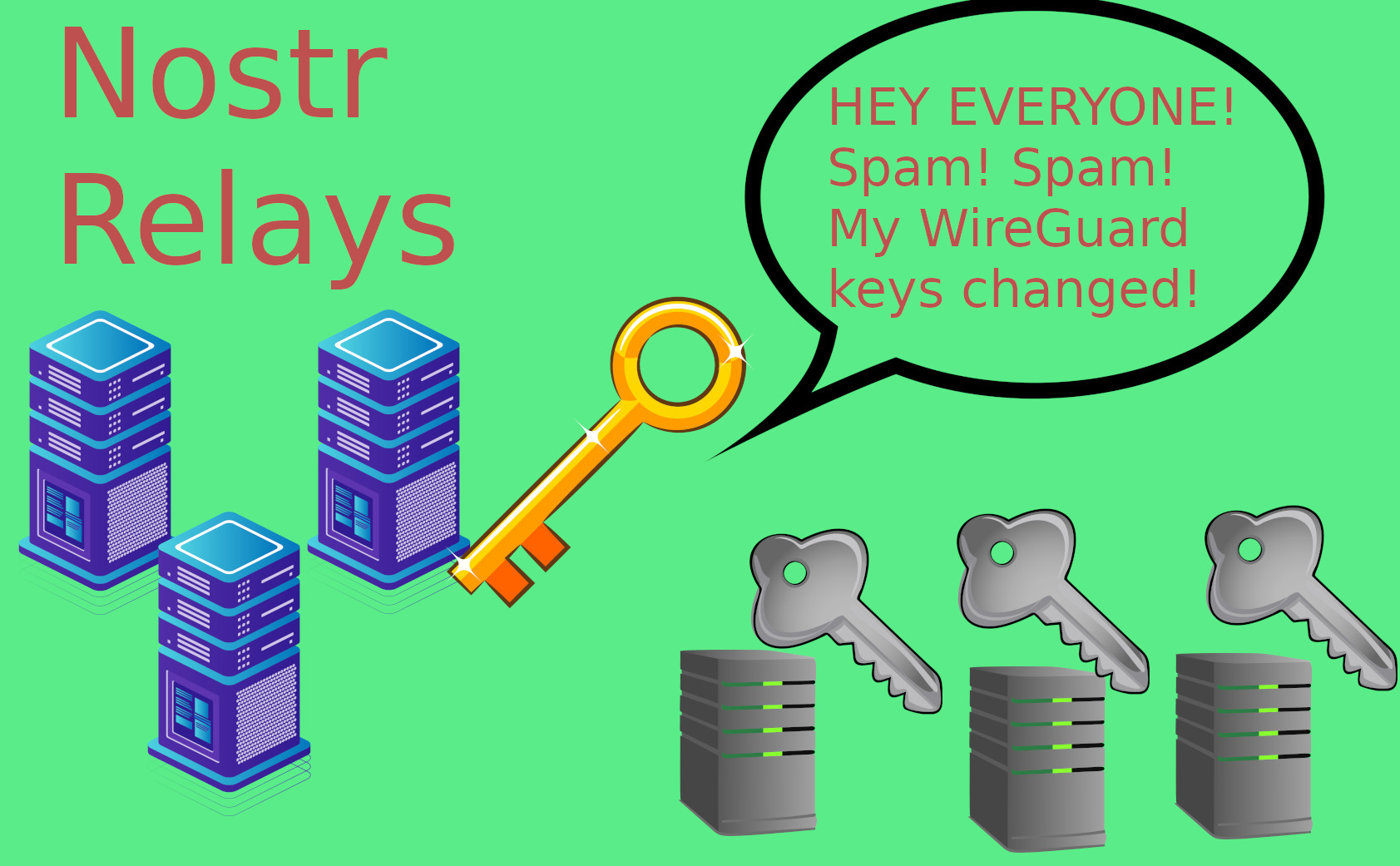
Instead, we have operators broadcast a single ed25519 key to the Nostr network.
This ed25519 key is in the same format that Wireguard originally uses, and then it signs for all the others. So this way, the Operator doesn’t need to spam jibberish on Nostr each time endpoints change.
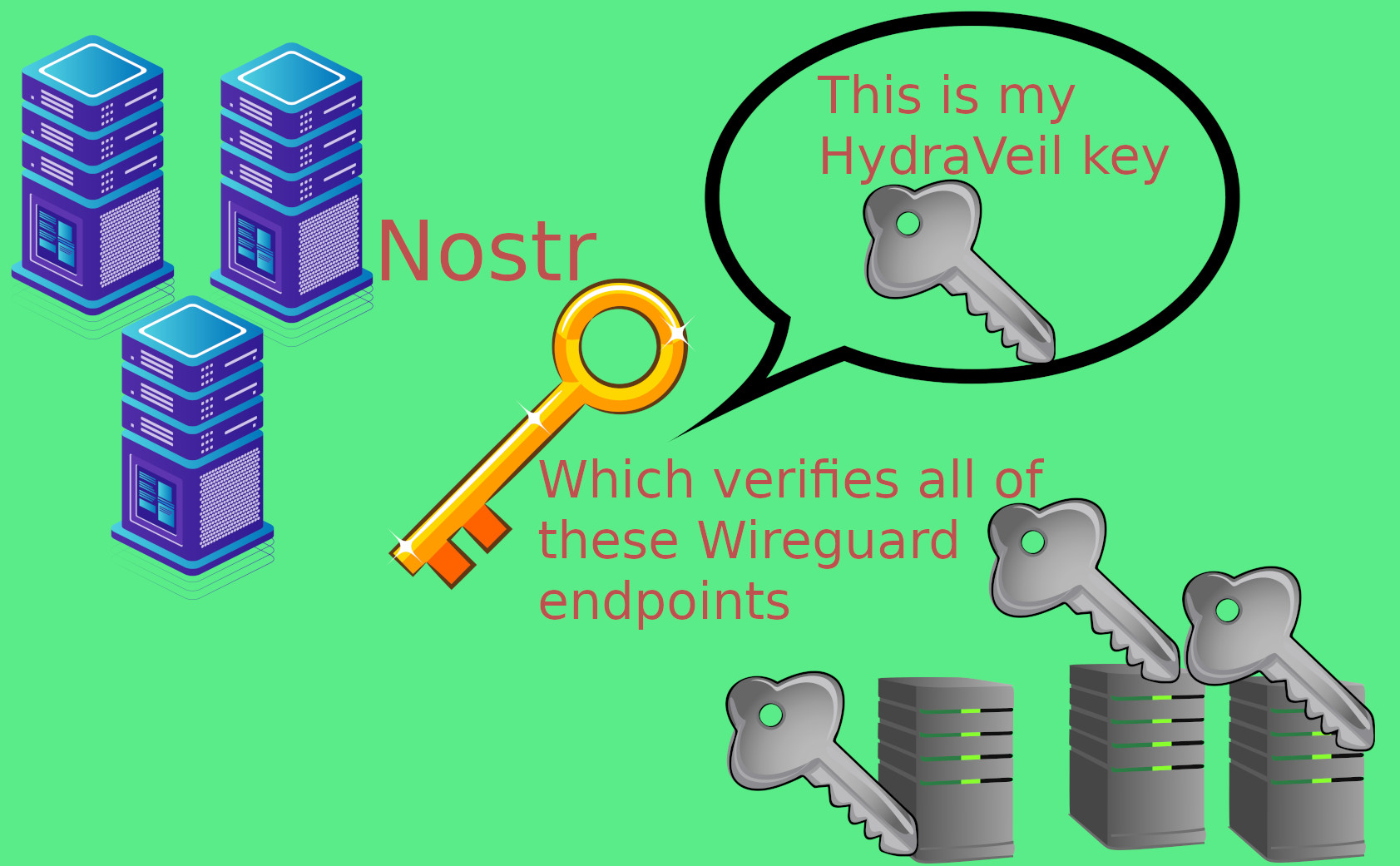
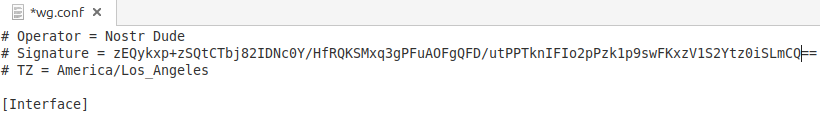
Wireguard configuration files then come signed by the Operator,
HydraVeil automatically and instantly verifies the signature prior to connecting.
Using the well-established and highly reviewed openssl library.
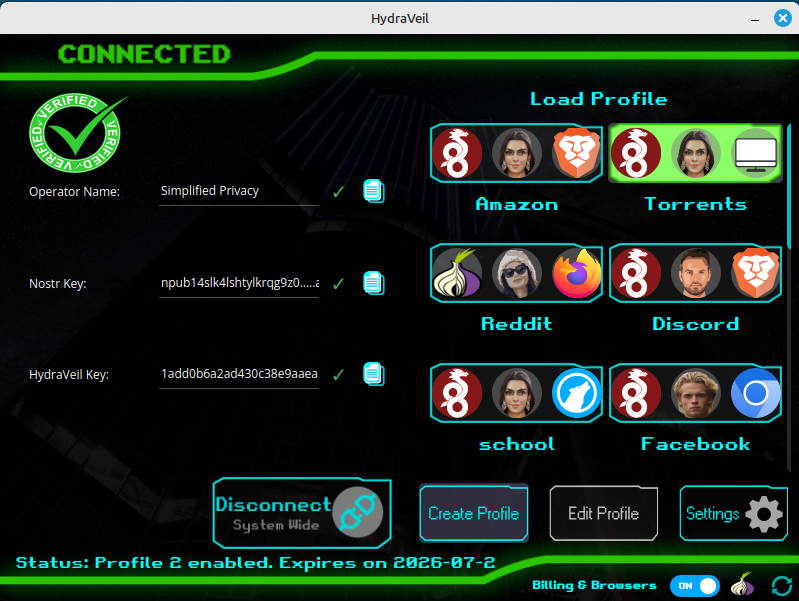
The original Nostr note broadcasting the HydraVeil key is displayed to the end-user.
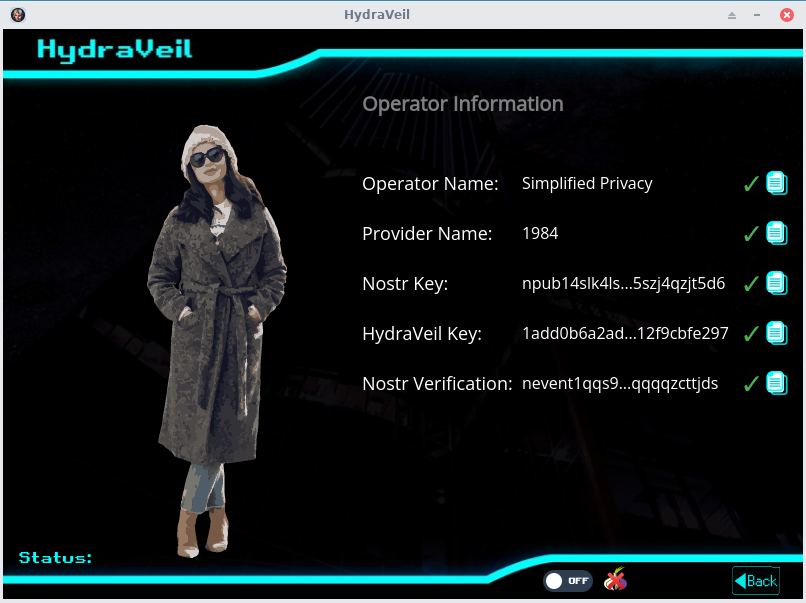
After you pay and download a browser, you connect directly to the node from then on.
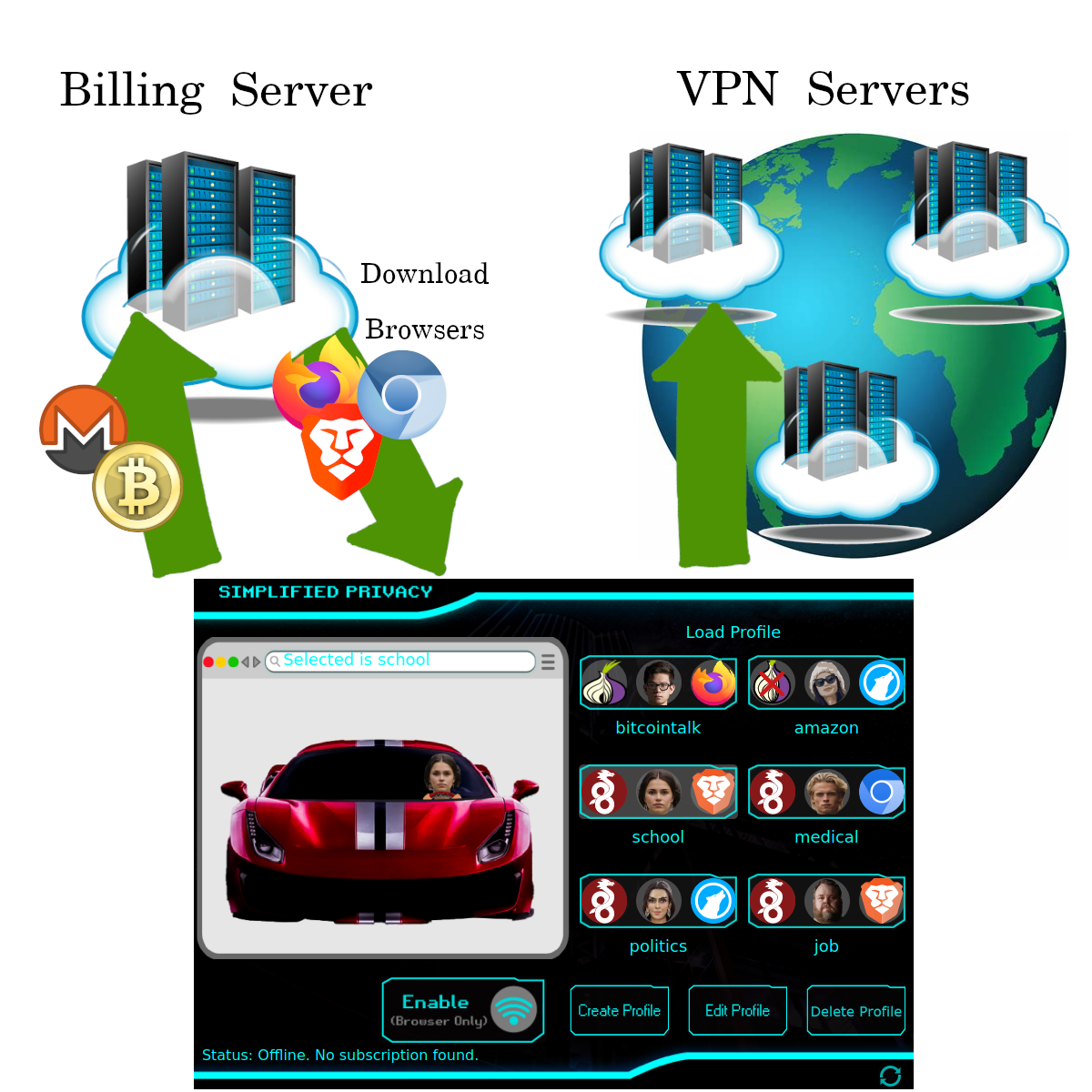
So Simplified Privacy can’t see traffic.
(unless of course you’re using one of the original developer servers)

Are You Interested in Running a Node?
Here’s an Overview Checklist of what’s involved
Technical Decision Docs:
There is an additional long-form technical version of the content in this article, that is strictly for those looking to fully understand our design decisions.
If you really want to learn and take your privacy to the next level, Learn about HydraVeil, Access our VPN, and subscribe to our new content via: Arweave Video RSS, Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts

Bareass Mullvad
How any app can rip these VPNs down without sudo
[SP]
Feb 20, 2026

Why a Nostr VPN?!
How should node operators identify themselves?
[SP]
Dec 17, 2025

Why Run a HydraVeil Node
Get Paid, Help Nostr, Help Privacy, & Be Part of Something
[SP]
Dec 17, 2025

Node Operator Checklist / Overview
Start Here if You're Interested in Hosting a HydraVeil Node
[SP]
Dec 17, 2025