Bareass Mullvad
How any app can rip these VPNs down without sudo

Video Format
We have a short demo video to explain these concepts and showcase the tool. If you are new to these concepts, please see the video first:
Video Link
No Sudo to Doxx
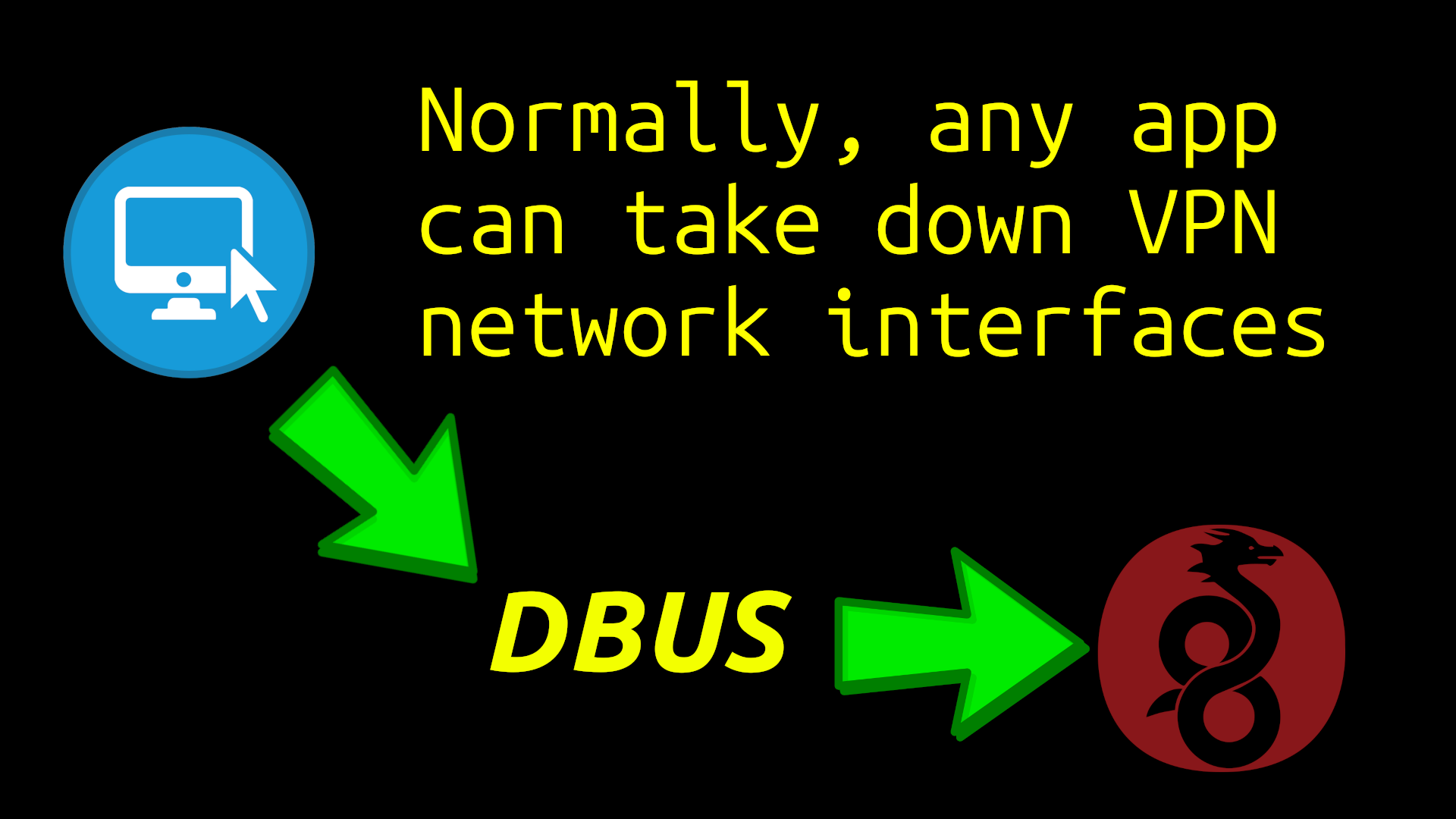
Traditional VPNs such as Proton and Mullvad are vulnerable on Linux to be immediately ripped down by any application without even needing sudo permission. An attacker can do so by using the DBUS, to take down virtual networking interfaces. By not even requiring sudo to rip down networking interfaces, the way Linux handles DBUS, provides a clear-cut method for any app to doxx a user behind a VPN. Once the real IP address is visible, then any app can then do an API call to any server for doxxing.
 When we consider that having multiple web browsers for resisting fingerprinting means installing large amounts of new software. And when combined with any potential web browser vulnerability, or even malicious intent from Mozilla, Google, or other apps, this is a dangerous path for the privacy of end-users to be potentially compromised by sophisticated attackers.
When we consider that having multiple web browsers for resisting fingerprinting means installing large amounts of new software. And when combined with any potential web browser vulnerability, or even malicious intent from Mozilla, Google, or other apps, this is a dangerous path for the privacy of end-users to be potentially compromised by sophisticated attackers.
Bubblewrap DBUS
To deal with these types of threats, HydraVeil bubblewraps the DBUS to prevent apps from touching the host’s networking interfaces and taking them down. This provides much stronger protection for the layer-1 ‘host’ Wireguard from these types of attacks.

All Apps Inside HydraVeil
HydraVeil’s protection is automatic for all apps found in the Linux app. This is currently web browsers at the time of this writing, but we are looking to expand to chat apps, email clients, and other useful apps. The init.ptl has the bwrap information, and further documentation on our entire strategy for security can be found in our yellow page paper.

BareAss Naked Tool
Simplified Privacy presents an original script for ripping down Mullvad & Proton VPNs without needing sudo, by abusing the DBUS and network interfaces. Any app can easily do these same types of actions, and unfortunately the vast majority of VPNs are exposed. Now this demo implementation just rips down the VPN, but in the wild, any app could make an API call to a server the attacker controls. Please see our self-host git for the code:
https://git.simplifiedprivacy.com/SimplifiedPrivacy/bareass_mullvad
Tool’s Use:
The following are commands to use the BareAss Naked Tool.
List Interfaces
The user can list all interfaces.
bash bareass.sh list
Butt Naked Mullvad
Kill Mullvad, through their “lockdown” mode"
bash bareass.sh kill-mullvad
Please see our podcast on Mullvad’s other poor decisions. Also our yellow paper’s key section, discusses disagreement with their multi-hop strategy.
Rip Down Proton
First list the interfaces, see a proton interface and take it down:
bash bareass.sh kill proton0
Please see our article on Proton’s negligence for other critical points we disagree with them on.
Proof of Concept DBUS Protection
To showcase what apps (such as a web browser) can do or access from inside the bubblewrap, do the following with the layer-one system-wide VPN already on:
bash bareass.sh bwrap-kill wg
And once again to repeat, all the apps inside HydraVeil have this automatically. This script is just a demonstration of the attack being done from inside the Bwrap. So you’re experiencing being denied from the point of view of the app.
If you really want to learn and take your privacy to the next level, Learn about HydraVeil, Access our VPN, and subscribe to our new content via: Arweave Video RSS, Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts

Why a Nostr VPN?!
How should node operators identify themselves?
[SP]
Dec 17, 2025

How a Nostr VPN Works
Node operators verify their identity?!
[SP]
Dec 17, 2025

Why Run a HydraVeil Node
Get Paid, Help Nostr, Help Privacy, & Be Part of Something
[SP]
Dec 17, 2025

Node Operator Checklist / Overview
Start Here if You're Interested in Hosting a HydraVeil Node
[SP]
Dec 17, 2025