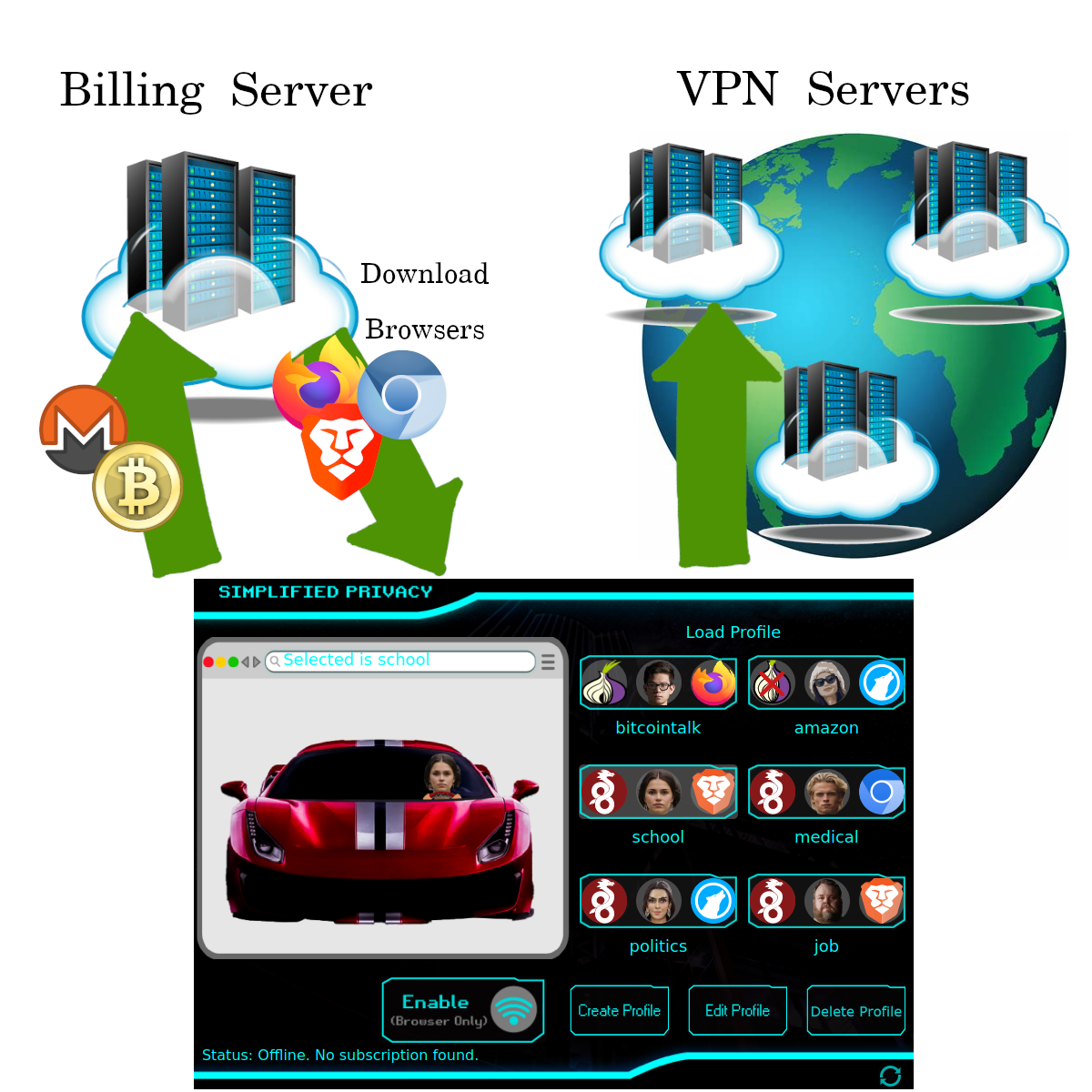
How HydraVeil Works
Technical Deep Dive: The Yellow Paper

Yellow Paper
This is a deeper technical dive into exactly how HydraVeil works. If you’re unfamiliar with topics such as Linux, networking, and security, please see our beginner guides, for basics such as what a socks5 proxy is.
This is not a tutorial:
This level of knowledge is not required for casual use. If you’re looking to use it, please see the tutorials section.
Outline with Links
Intro
Networking
Networking Overview
Wireproxy
Masked Tor
Billing Identity
Sync
Decentralization
Security Features
Filesystem Isolation
DBUS Isolation
Sudo Daemons
Direct Connections
Key Isolation
Fingerprint Profiles
Screen Size
Graphical Isolation
Timezone
Fonts & Canvas
Web Browsers
Server-side
Intro Context
AI
The rise of artificial intelligence has ushered in a new age of surveillance. Because of the flawed nature of web browsers, hundreds of characteristics can be fed into machine learning models to perform analysis of user’s internet traffic. So what was once too vast a dataset for a corporation or government to sift through, can be saved for long periods of time and looked back upon indefinitely for patterns, without requiring large amounts of human labor.
CDNs
With millions of dollars pouring into companies like Fingerprint-com, combined with the centralization of the internet to mega-corporation Content Delivery Networks such as Cloudflare, Google, and Amazon, oversee massive amounts of data. CDNs fingerprint users web browsers, connection speeds, and break SSL encryption.
JavaScript
Big Tech websites have become more and more bloated with scripts, captchas, and surveillance tools. Yet solutions such as Tor Browser, solely rely upon heavily restricting Javascript, and have no magic tech outside of that.
HydraVeil’s Goals
Our primary goal is to provide isolated browser fingerprints that realistically fool known fingerprinters, with minimal friction or negative downsides such as a virtual machine. Our secondary goal is to create a decentralized VPN using “encryption as identity”, where the end-user can pick where and how to use these fingerprint profiles. Our third goal is to provide a secure environment within these profiles, to hinder an attacker from accessing the networking interfaces, filesystem, timezone, or graphical data of the host.
Overview of Environments
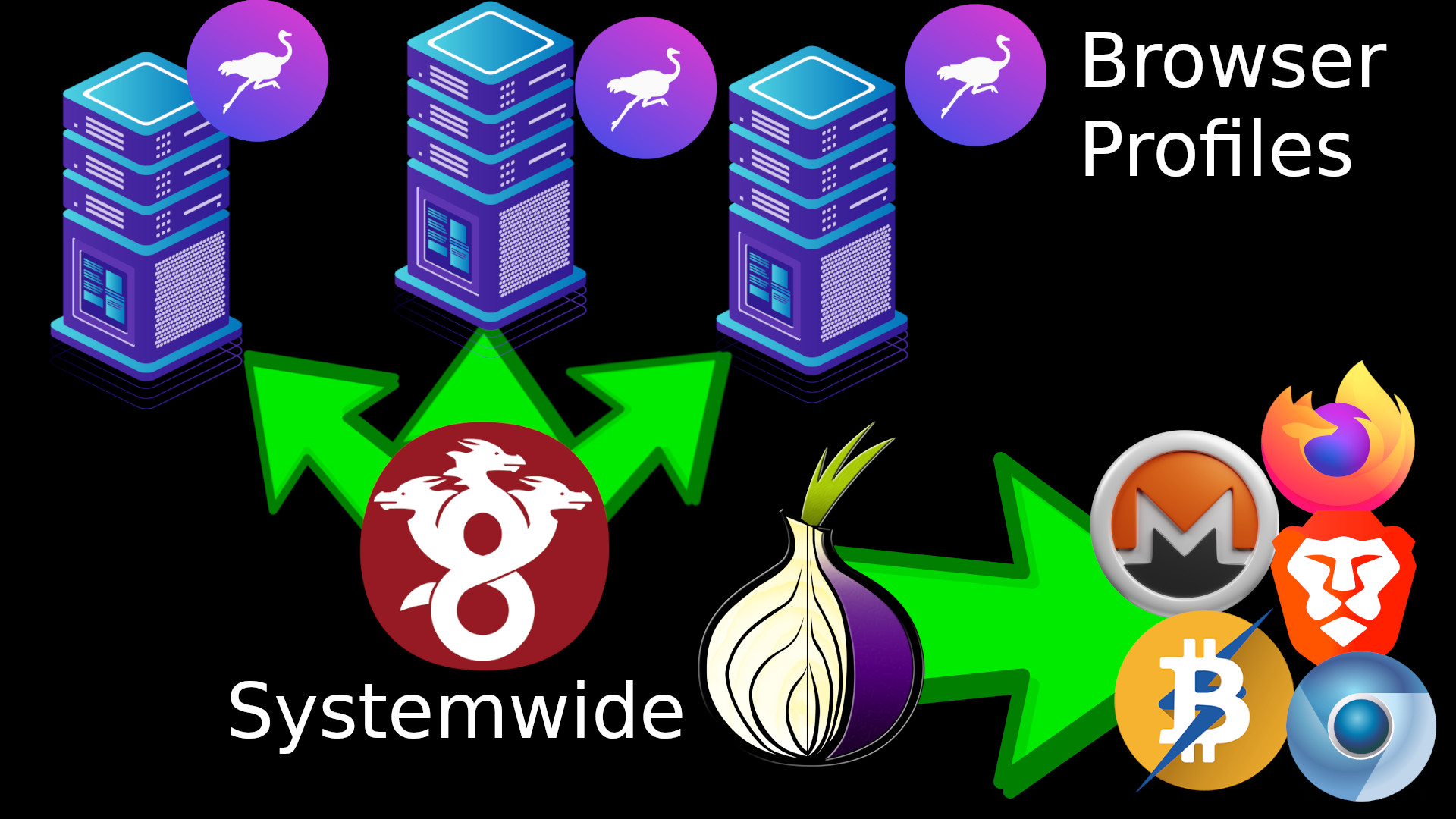
HydraVeil uses a two-layer system, with a traditional system-wide Wireguard connection on the host computer. Then we create a second unique “layer”, using a combination of tools including Bubblewrap, Proxychains, Wireproxy, Xephyr, Cage, and others as described below. This second layer is very modular and dynamic, and is currently networking neutral, so it could be used for Wireguard or routing through Tor. And it’s also “app neutral”, so it could be used for more than just web browsers.
System-wide Layer One
For the systemwide Wireguard connection, we literally use ‘nmcli’. By using Linux’s nmcli at a high level directly, we draw upon pre-existing tools with a proven track record. This provides an easily verified, and reliable foundation for our original layer two work to build upon with little skepticism.
In it’s current implementation, profiles require sudo permission a single time to setup up, and put Wireguard configurations in the /etc/hydra-veil/profiles folder. However, nmcli would not require sudo every single time to enable the same configuration.
Two Layer Networking
For the second “layer”, HydraVeil uses bubblewrap to modify and trick apps into thinking artificial networking files are global configurations. While Bubblewrap is traditionally only thought of a security sandbox tool, we also use it to modify the behavior of applications. Within this artificial environment, apps use the ’localproxy’ that apps believe is happening systemwide. The networking exposed to the app, could be any type of proxy, but the current two choices are Wireproxy or Tor.
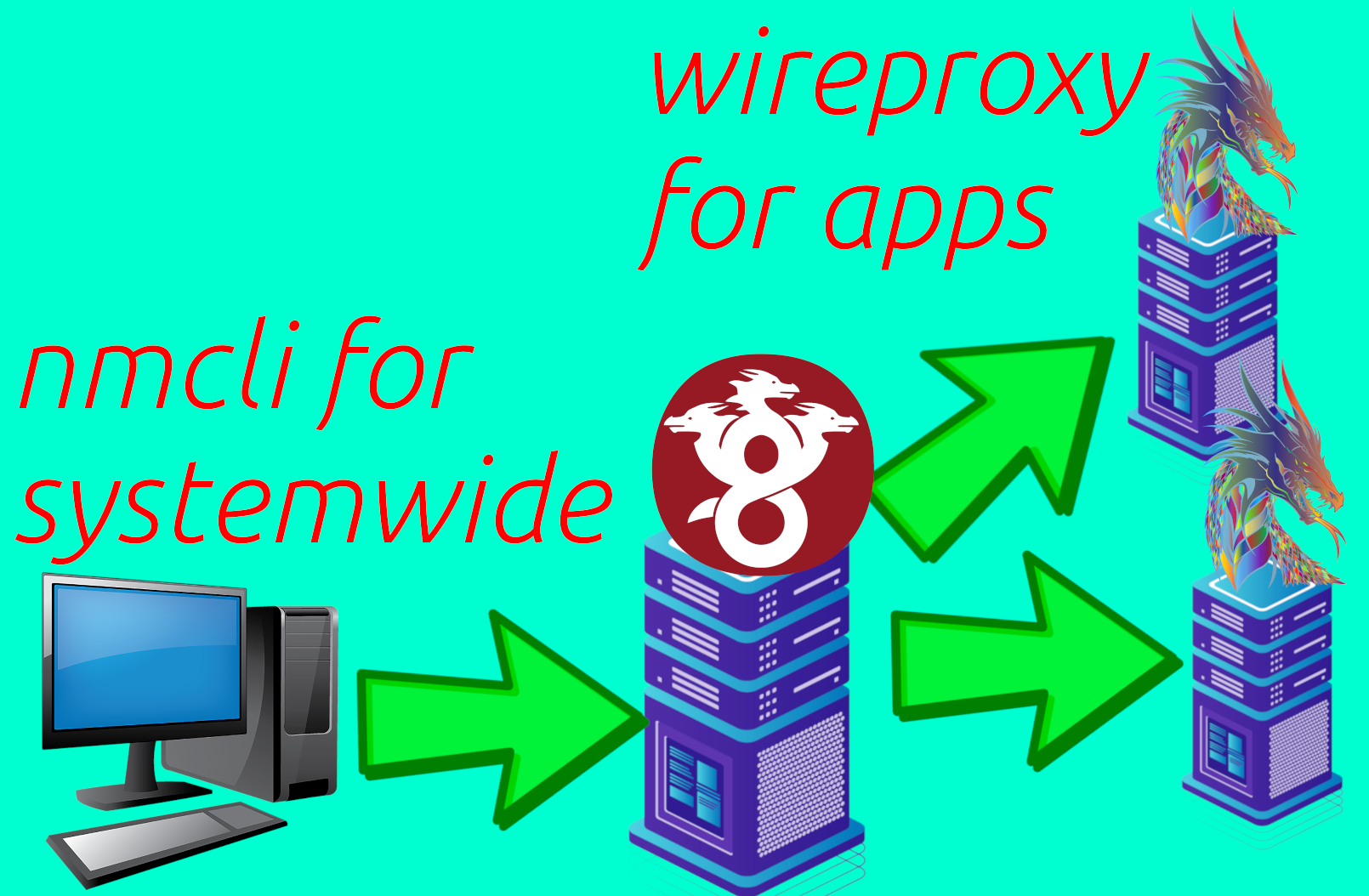
Wireproxy
Wireproxy is a pre-made tool, that allows the user to create Wireguard connections as a socks5 proxy, without requiring access to the host’s networking interfaces. This allows the connection to be disposable, but still provide the encryption and privacy of traditional Wireguard.
What Apps See
It’s important to note that Simplified Privacy has created a custom networking environment that exposes Wireproxy. And so within this environment, it’s acting as the ’localproxy’. Therefore, the apps aren’t concerned or aware of what networking protocol is used beyond it being the ’localproxy’.
What Servers See
As far as what data the server operator can see, it’s the same as regular Wireguard. The user’s home ISP can not see through encrypted content, however the VPN operator can. But by having one operator for system-wide Wireguard, and another operator for Wireproxy at the layer-two application level, the user is anonymous to the second-layer’s operator. And the first operator can not see the traffic.
But how does the end-user know it’s really different operators for each layer? This is where “encryption as identity” comes in, and we link ed25519 keys to the decentralized social media Nostr. Please see our Operator Encryption section.
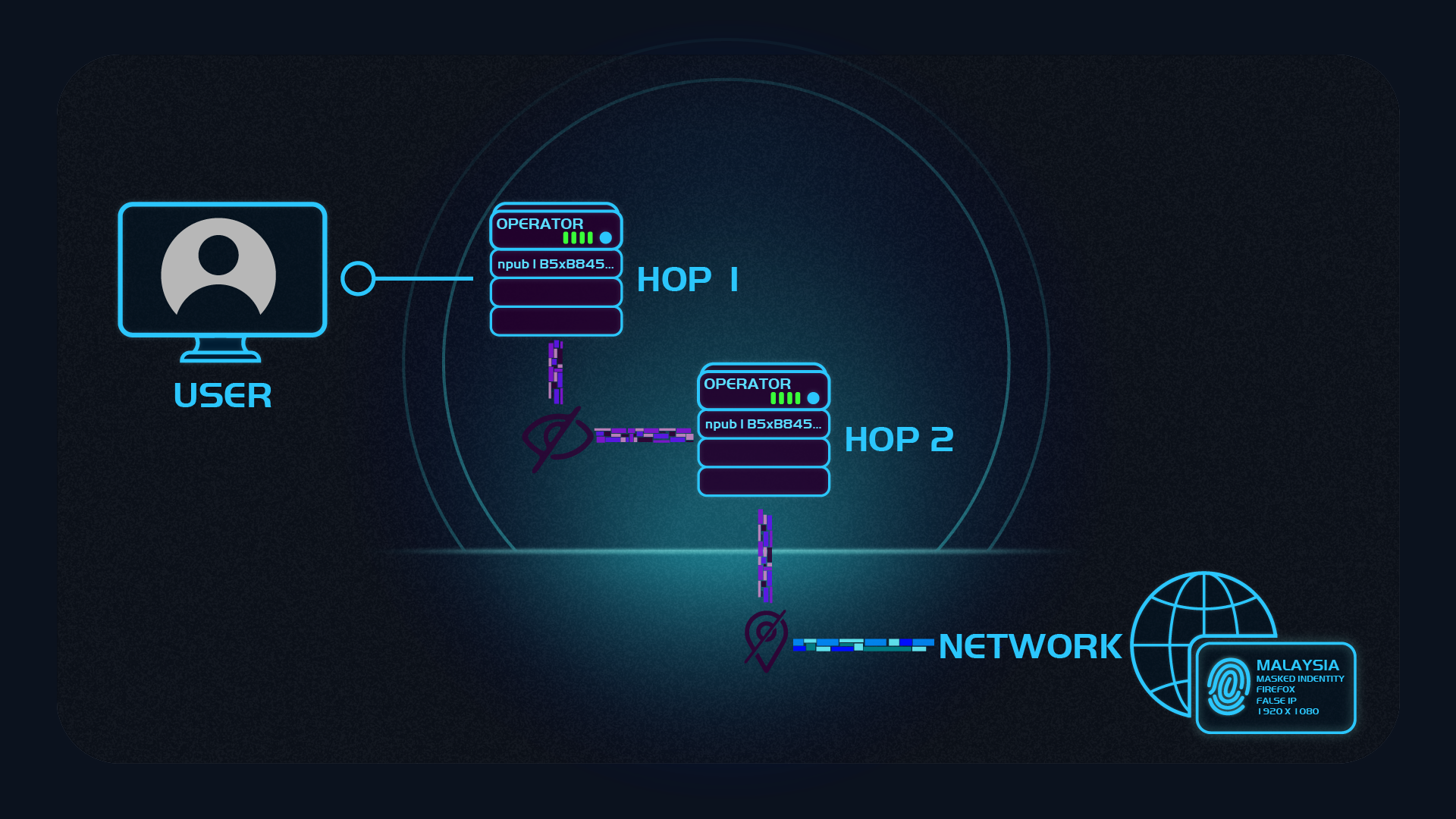
Masked Tor
If the user still prefers Tor networking, HydraVeil also offers a “masked Tor” option. This allows the user to first pass through 3 hops of Tor, then exit to a socks5 proxy using Proxychains and microsocks.
return subprocess.Popen(('proxychains4', '-f', proxychains_configuration_file_path, 'microsocks', '-p', str(proxy_port_number)), stdout=subprocess.DEVNULL, stderr=subprocess.STDOUT)
From ConnectionController in the core libraries.
This hides from the website that the user is using Tor, while also giving fingerprint protection without Javascript restrictions.
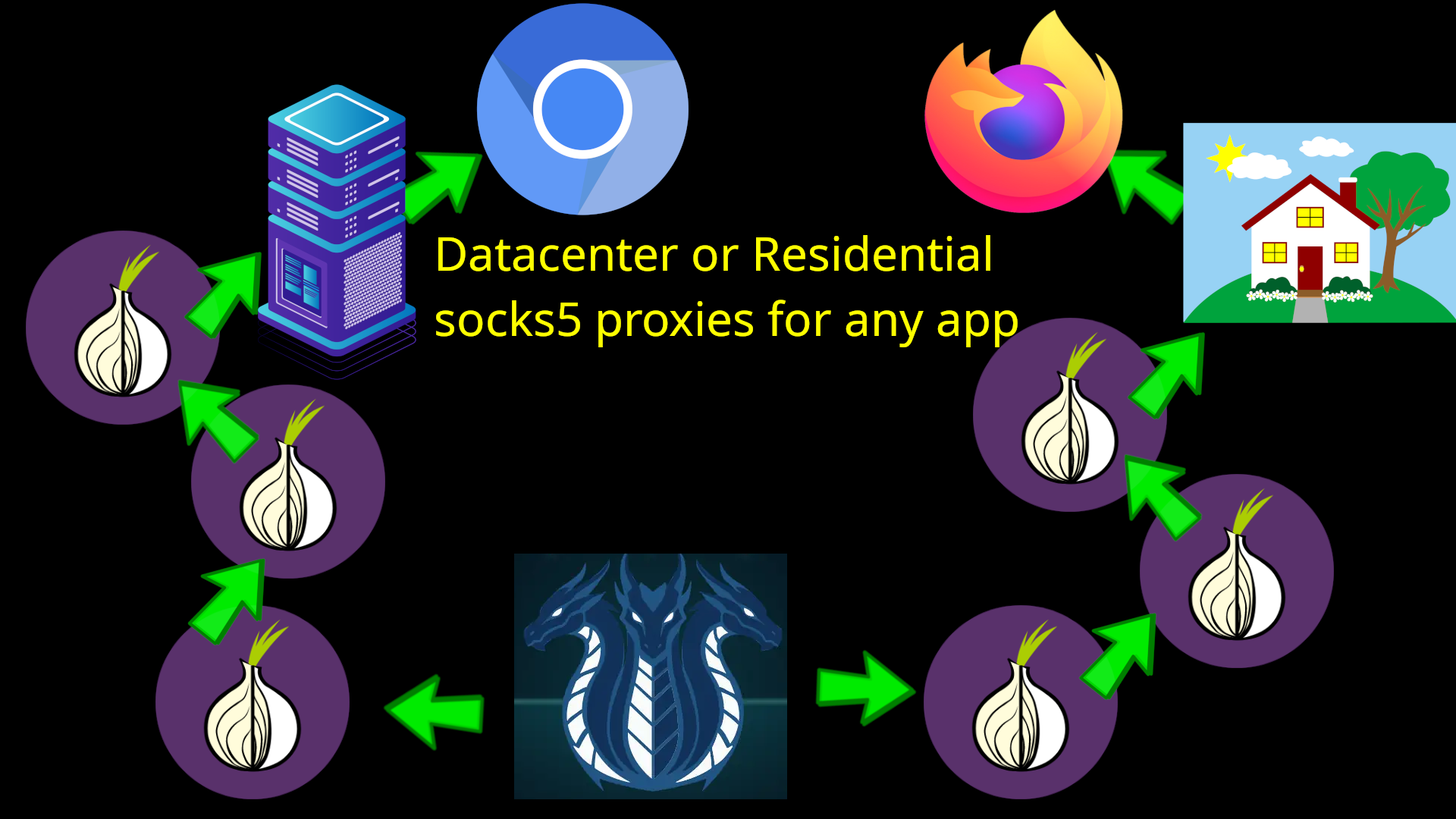
Freedom of Choice
Additionally, many criticize the Tor Project’s team for using Mozilla’s Firefox as the only base, when Chromium based browsers are considered to have better support from websites and more advanced security. Numerous tech journalists criticize Mozilla’s focus on AI and social justice causes, over security.
However, if users stray away from the official Tor Browser, they expose themselves to fingerprinting by going against the herd. With HydraVeil’s numerous isolated profiles, it not only can users effortlessly bypasses Tor IP address blocks, and Javascript requirements, but also separate the chains between Mozilla and Tor.
Stateful Tor sessions
HydraVeil makes no internet connections on startup to avoid metadata leak of different profiles. But if the user enables a Tor profile, or connects to the billing server with Tor billing mode on, then it first bootstraps Tor and and saves the state. This allows new Tor circuits to be created for other app/profiles or billing connections, but without having to bootstrap Tor each time.
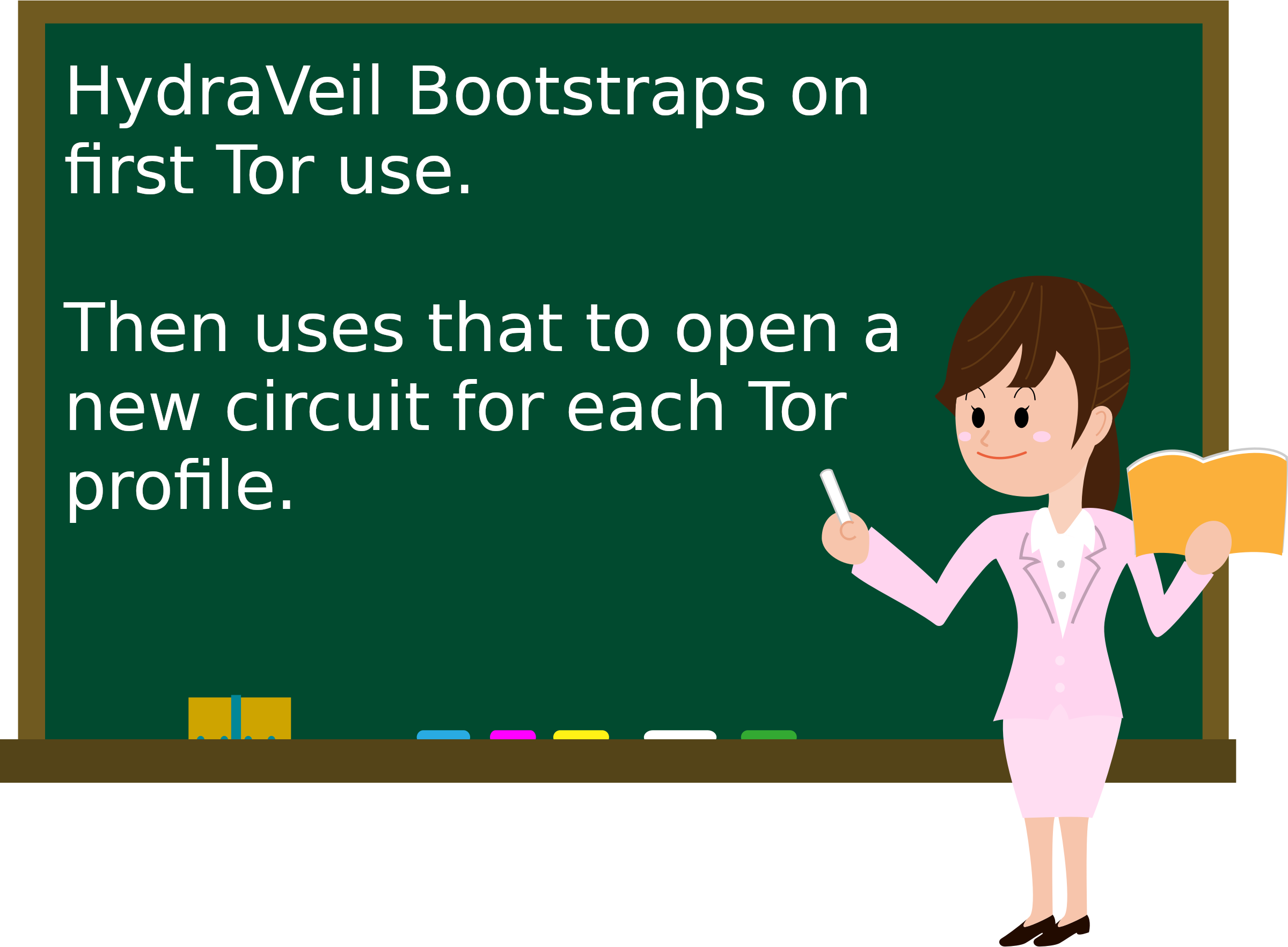
Overall, this increases speed and convenience, but without the burden of bootstrapping Tor each time. While it still gives the privacy new Tor circuits for each profile or app. For further details, please see the commit.
Identities and Billing
When the HydraVeil app starts up, it doesn’t make any calls to the internet. And when a profile is enabled, it first tries to directly connect to that profile. This is so the user can effortless manage their different identities in a controlled way. And can allocate that trust to different operators for isolation.
1 Config = 1 Profile
Under the current implementation, a single Wireguard configuration is tied to each profile. The user can renegotiate a new configuration with the billing server, but this would invalidate the previous configuration tied to that billing code. This allows for simplicity and ease of separation of profiles.
Sync
Sync is the processing of getting the latest data from the billing server, such as which locations, operators, billing plans, and apps such as web browsers are being offered. Sync is currently destructive, and overwrites the existing data on the user’s local machine. Sync does NOT upload any data about the user to the billing server.
Tor Sync
Because HydraVeil offers the possibility of having different profiles for the purpose of isolating identities, there is a large chance the end-user will be interested in hiding the setup of these profiles from the billing server. Especially if the Wireguard node is run by an operator other than Simplified Privacy. For this reason, there is the possibility of using Tor to sync. The ability to use Tor to sync is offered even if the profile being setup uses Wireguard (and not Tor).
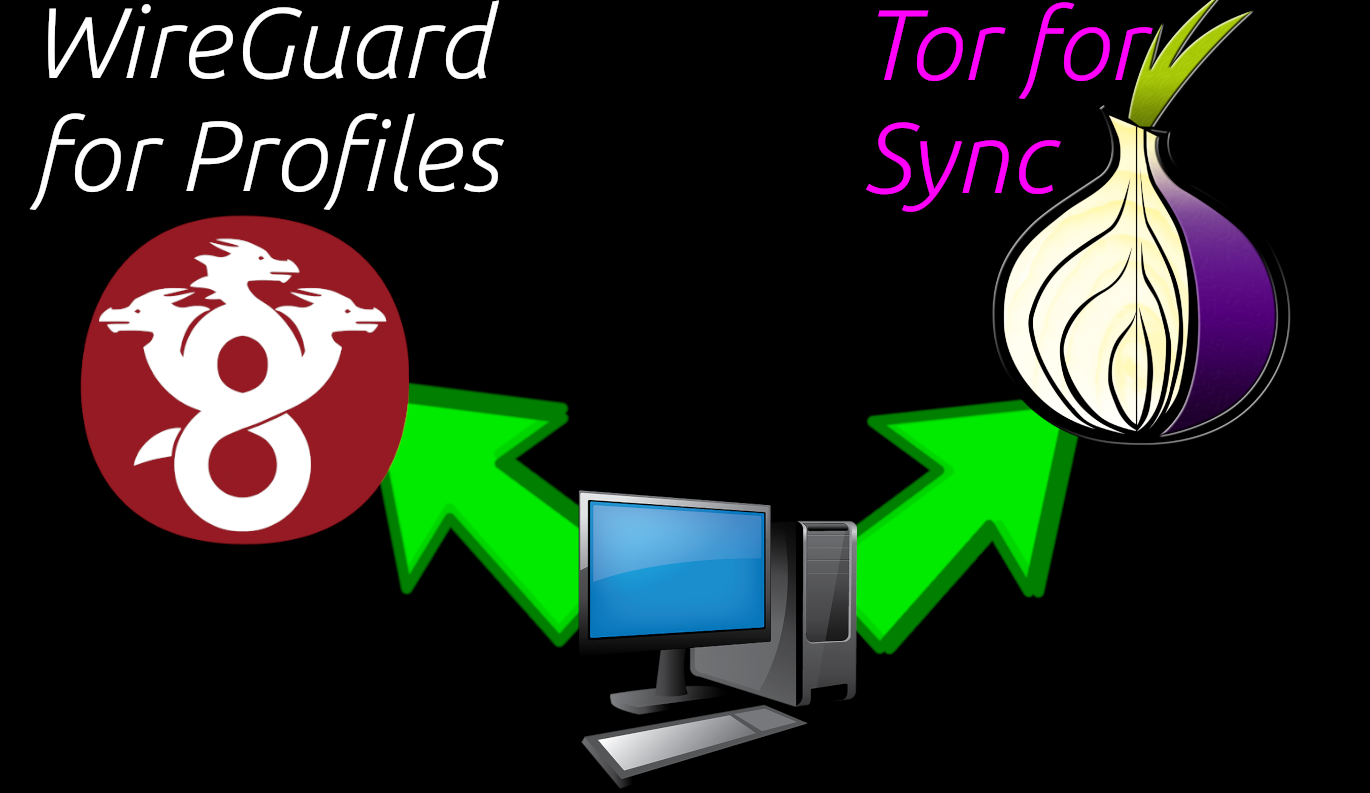
Tor sync follows the same bootstrap and state processes as Tor profiles. And the same bootstrap setup can be used for both Tor->socks5 app profiles, as well as Tor Sync. This would use the same setup, but different circuit paths.
Encryption as Identity VPN
One of challenges of decentralized networks such as Tor, is that the nodes are a commodity. The end-user has no way to evaluate or even choose which nodes to use.
Instead of having randomly assigned nodes with no real accountability, HydraVeil follows the principle of encryption as identity. We use the same encryption type and format as Wireguard, which is ed25519. And generate the keys using the openssl library directly as a bash script.
openssl genpkey -out id_ed25519 -algorithm ED25519
openssl pkey -in id_ed25519 -pubout -out id_ed25519.pub
id_ed25519_pub="$(openssl pkey -in id_ed25519 -noout -text_pub | tail -n 3 | tr -d ': \n')"
From HydraVeil’s operator toolkit
Not only does ed25519 have a fast encryption verification speed, but also having shorter strings in the same format as Wireguard. This allows for faster parsing of Wireguard configuration files for these identity keys, than if full Nostr JSONs with Schnorr keys were used directly.
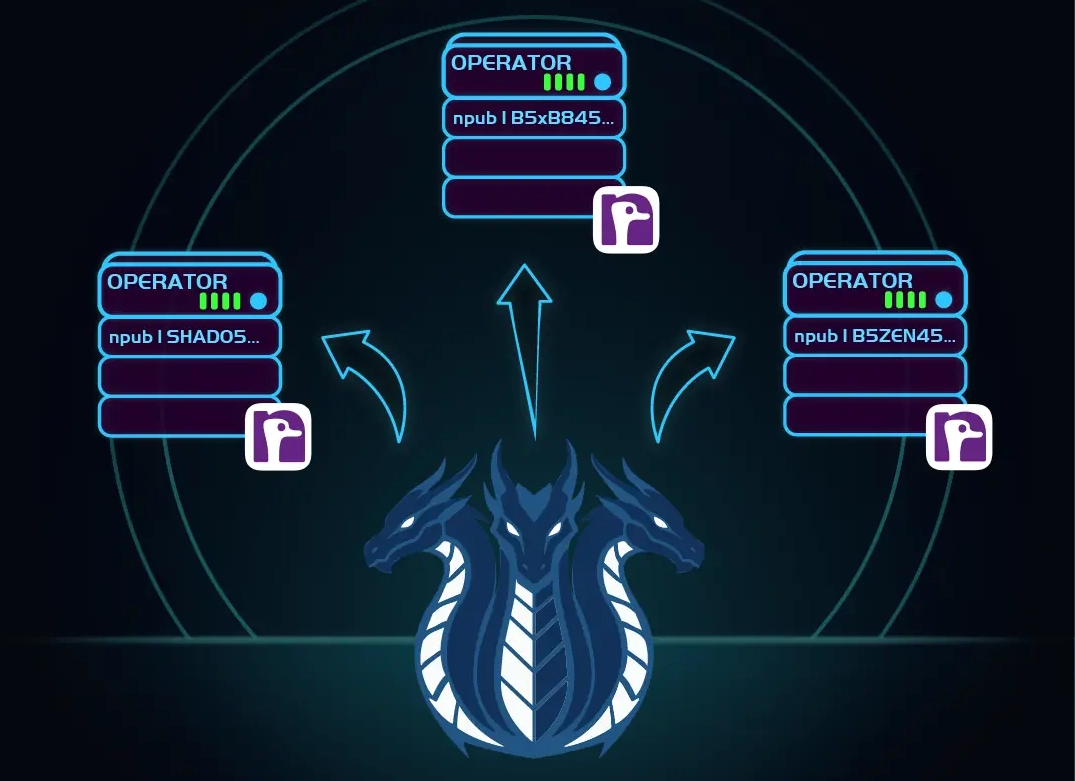
Then we tie these ed25519 keys to Nostr keys, by having the Nostr user post to public relays the Wireguard format ed25519 key. And our web-service serves the Nostr notes to the end-user, to avoid any privacy leaks from connecting to public relays. Finally, we display this Nostr note data to the end-user of the VPN when they pick which operator they wish to use.

Nostr is a well-known decentralized social media, which brings accountability, external verification, and a social meaning to these encryption keys. The HydraVeil client verifies the ed25519 identity key in the Wireguard configuration file on every single connection.
operator_public_key = ed25519.Ed25519PublicKey.from_public_bytes(bytes.fromhex(operator.public_key))
for wireguard_public_key in wireguard_public_keys:
operator_public_key.verify(base64.b64decode(signature), wireguard_public_key.encode('utf-8'))
Please see the commit
Security Features
Bubblewrap Filesystem
HydraVeil isolates apps from accessing the filesystem of the host through Bubblewrap as well. In the current implementation, apps can only see the user’s ‘Downloads’ folder.
bwrap \
--bind-try {home}/Downloads {home}/Downloads \
From the app’s init.ptl files.
So if the user wishes to upload files through an app (such as via a web browser), then they would have to put the files in the ‘Downloads’ folder first. This is very similar to how Tor Browser uses bubblewrap as well, as HydraVeil’s more unique uses are in the networking and DBUS.
No Sudo to Doxx
Traditional VPNs such as Proton and Mullvad are vulnerable on Linux to be immediately ripped down by any application without even needing sudo permission. An attacker can do so by using the DBUS, to take down virtual networking interfaces. By not even requiring sudo to rip down networking interfaces, the way Linux handles DBUS, provides a clear-cut method for any app to doxx a user behind a VPN. Once the real IP address is visible, then any app can then do an API call to any server for doxxing.
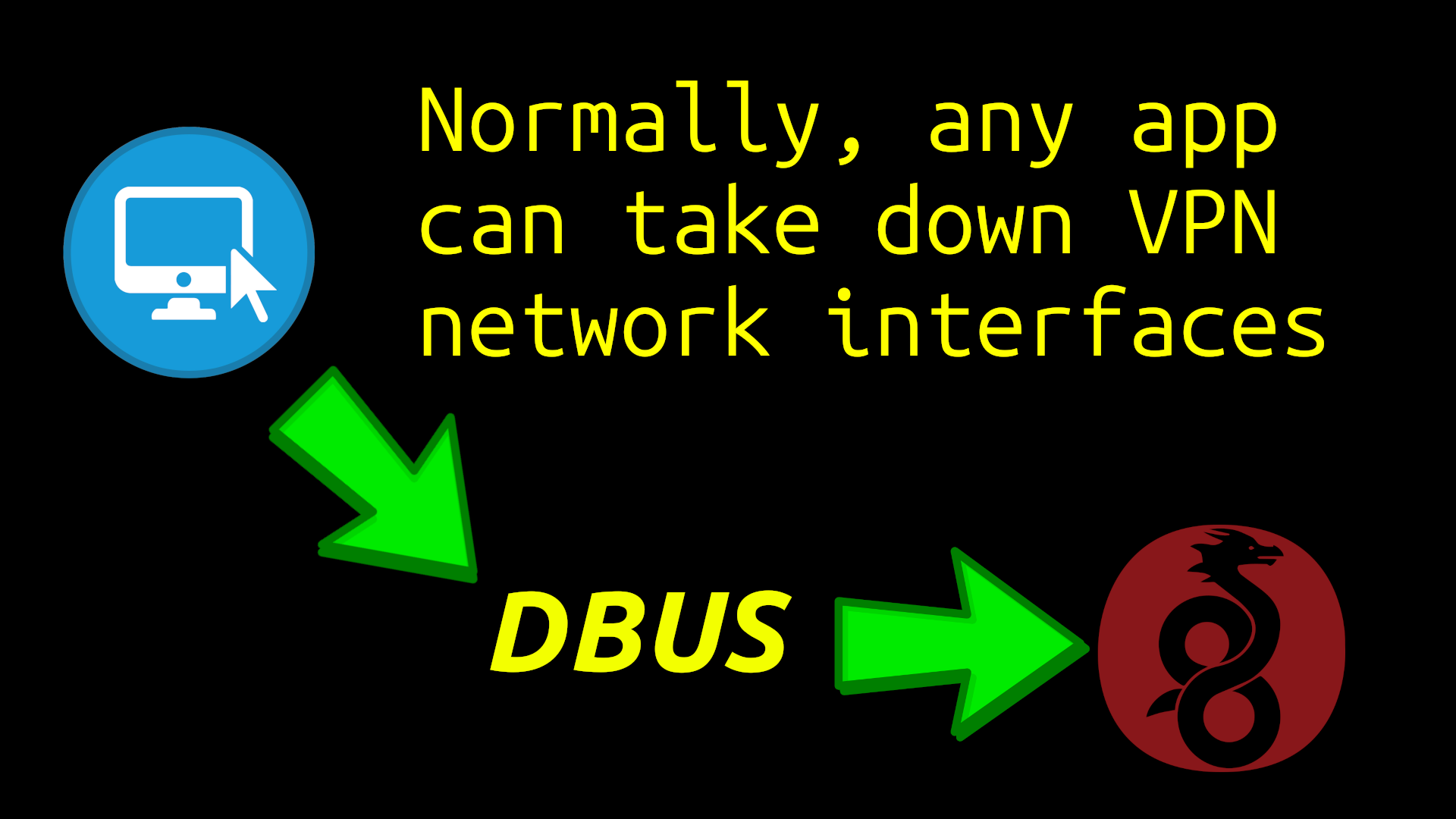 When we consider that having multiple web browsers for resisting fingerprinting means installing large amounts of new software. And when combined with any potential web browser vulnerability, or even malicious intent from Mozilla, Google, or other apps, this is a dangerous path for the privacy of end-users to be potentially compromised by sophisticated attackers.
When we consider that having multiple web browsers for resisting fingerprinting means installing large amounts of new software. And when combined with any potential web browser vulnerability, or even malicious intent from Mozilla, Google, or other apps, this is a dangerous path for the privacy of end-users to be potentially compromised by sophisticated attackers.
Bubblewrap DBUS
To deal with these threats, HydraVeil bubblewraps the DBUS to prevent apps from touching the host’s networking interfaces and taking them down. This provides much stronger protection for the layer-1 ‘host’ Wireguard from these types of attacks. And these commands are found in the app’s init.ptl file.

bwrap \
$(find /run -mindepth 1 -maxdepth 1 ! -path /run/dbus -printf '--bind %p %p ' 2>/dev/null) \
From the app’s init.ptl files.
Demo Script & Video
Simplified Privacy has created a demo Linux bash script and a video to demonstrate both these types of attacks and HydraVeil’s solution. Please see the script’s article for instructions, video, and code.
Other VPNs
Most VPNs have the user connect to their centralized billing system on bootup to not only verify subscriptions, but also to dynamically get configurations on the fly. This means the VPN company can see every time it’s used or logged into.
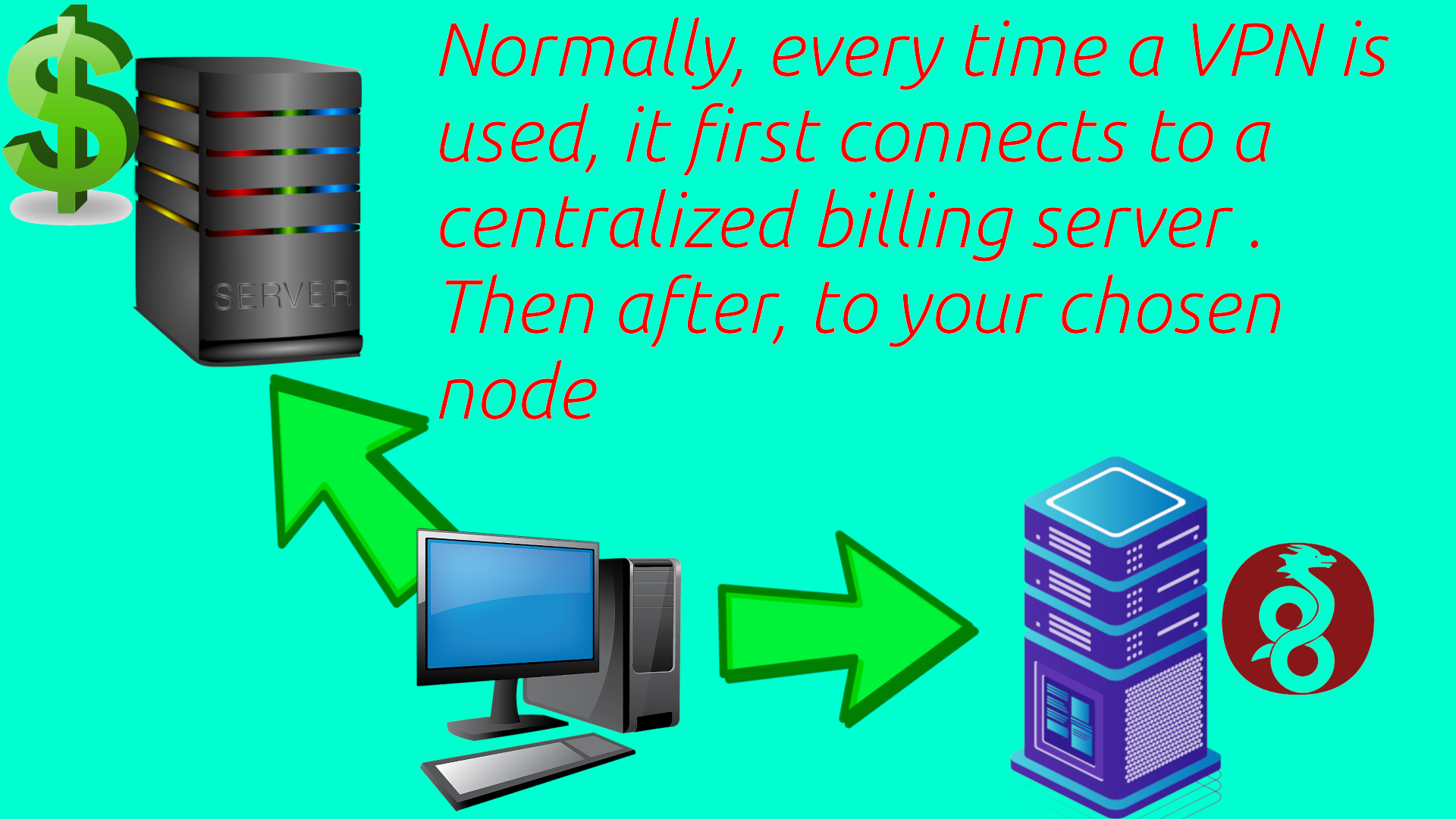
Sudo Daemon
And most VPNs require running a 24-7 sudo daemon to dynamically insert configurations on the fly. These daemons may run as a SystemD service on startup, and often any app can access them. For example Proton VPN heavily relies upon this type of strategy. But these daemons increase the attack surface by having elevated privileges that run all the time.

No Sudo Daemon
Instead, HydraVeil saves Wireguard configuration files locally on the user’s computer, and uses disposable Wireproxy connections for frequent changes. The advantage of saving Wireguard configurations, Wireproxy, and having a direct connection flow, is that it eliminates the need for a constant sudo daemon. Because the user can keep the same system-wide connection continuously, and change IP addresses on the “layer-two” with Wireproxy.

So HydraVeil allows the end-user to get the upside convenience of effortless IP address changes, but without the downside security burden of a 24-7 sudo daemon like other VPNs. We store the config in the /etc/ folder for security, and with nmcli, it only requires the sudo password a single time on the initial setup. And from then on, it can be used without entering the sudo password or requiring a constant daemon.
HydraVeil’s Direct Connections
Also this approach, of saving Wireguard configurations for future use, is much more private. Because when the user hits connect, they first directly connect to their chosen operator for that profile, and only if it can’t connect does it contact the billing server. These helps to hide metadata from the billing server about which identities are the end-user, by avoiding contacting it each time a profile is used.
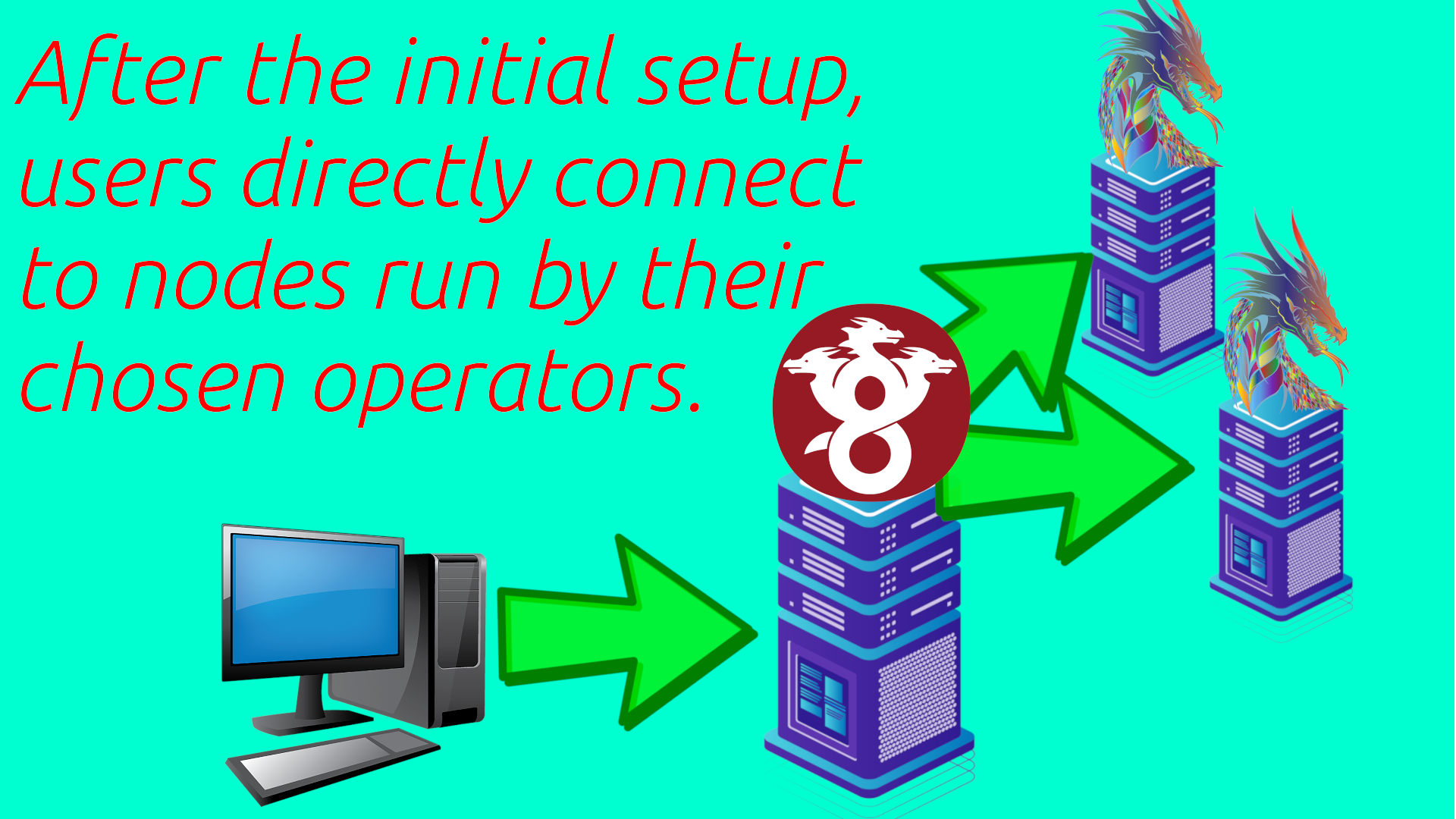
Relationship to Nostr
With isolated billing and two layers, this provides not only anonymity, but also accountability of operators as the user decides who to allocate these roles to. Ultimately the developers of HydraVeil look to let end-users decide which node operators to trust. And with multiple layers to minimize that trust as much as possible.
WireGuard Keys
To setup an initial Wireguard tunnel, the client has a public key to identify itself. In traditional Wireguard, when it does multi-hop, it uses this same public key for both servers.
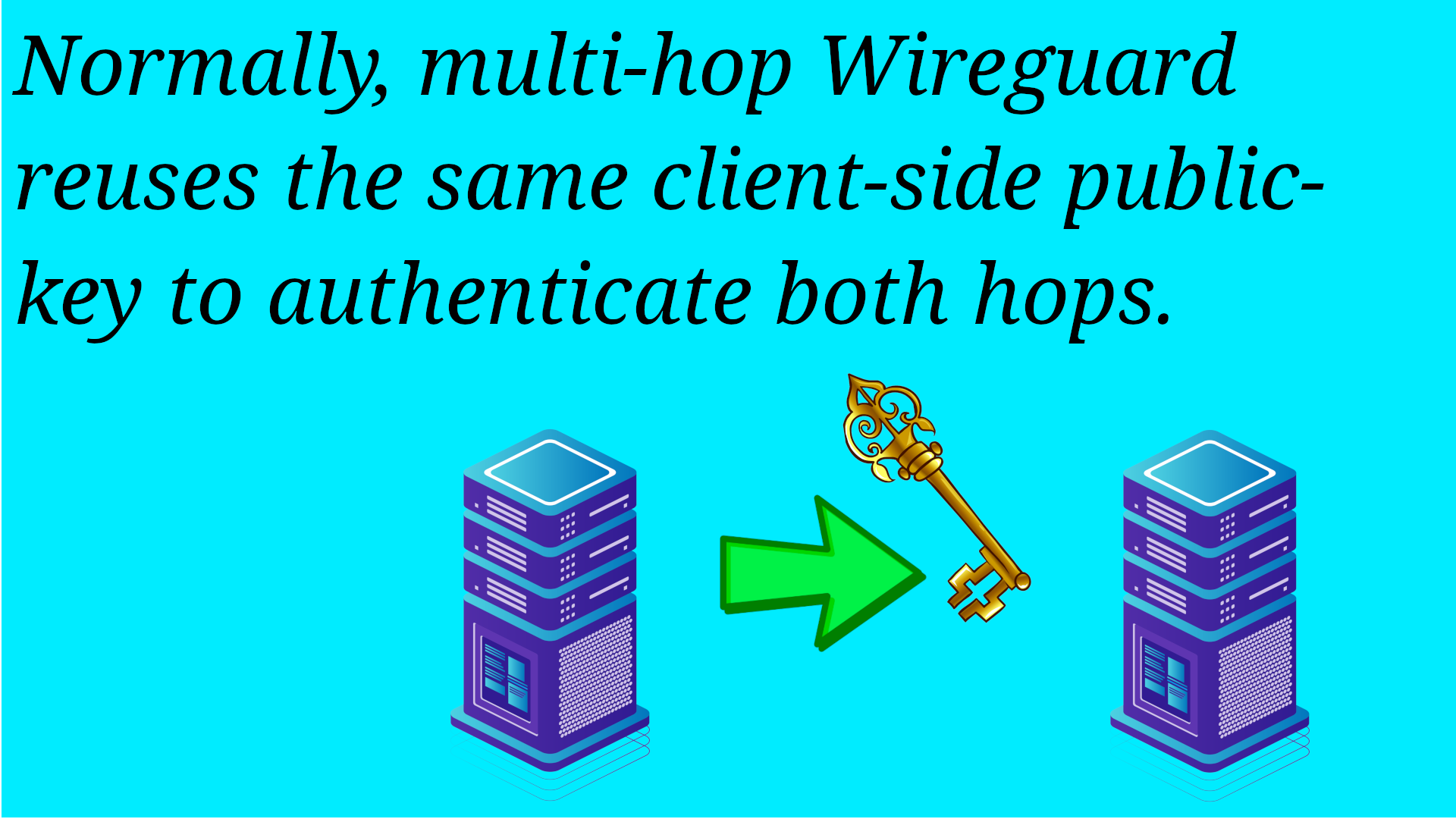
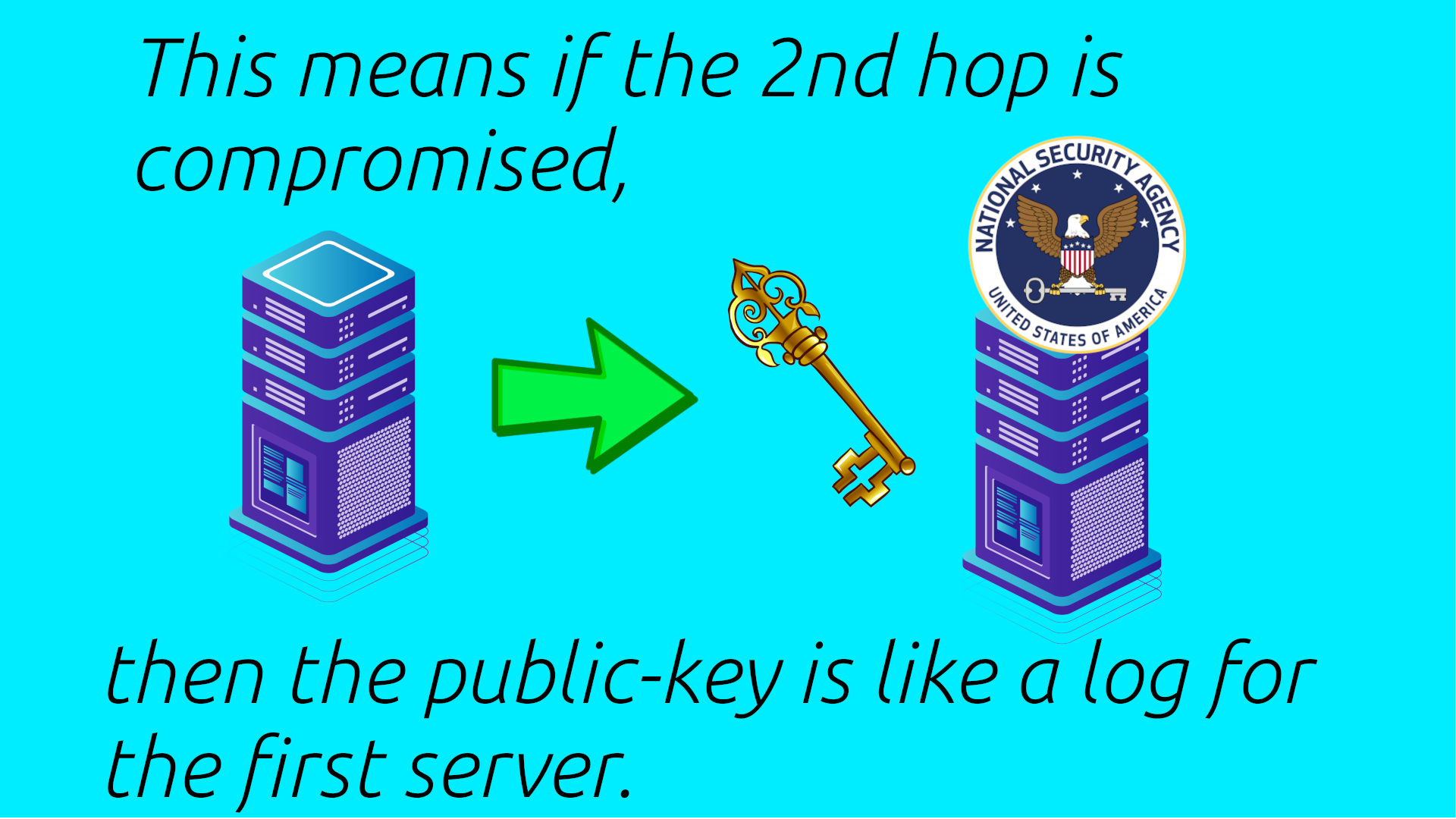
Key is like a Log
But this means if the second server is compromised, then the client’s public key is the starting point for an investigation into the first server.
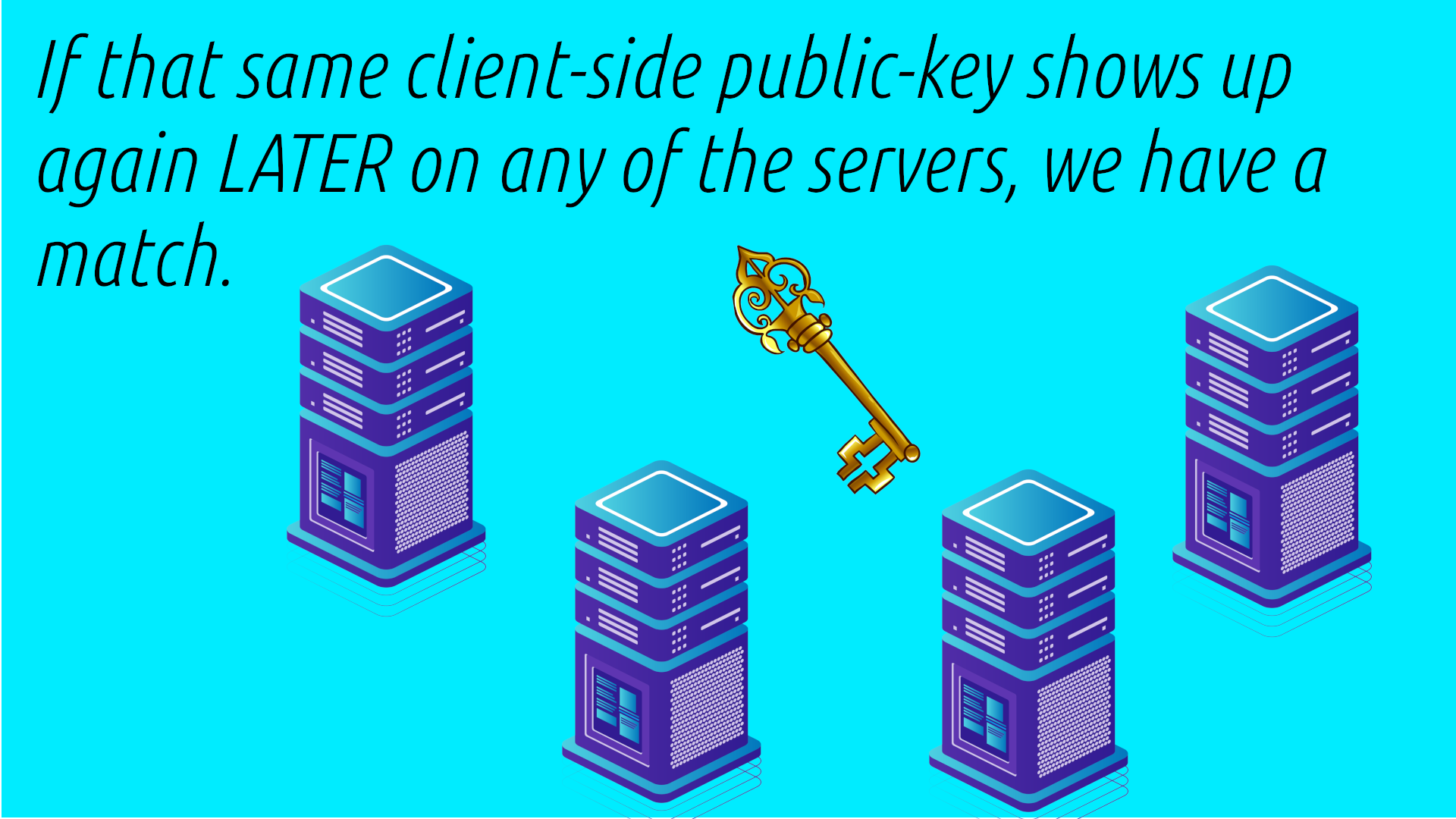
Now instead of the data being wiped forever, the attacker may have a long period of time to try to get access to other servers and see if that public key shows up again. And often VPNs rent servers from third parties in other countries, where they have limited ability to control if that business entity is forced to do memory dumps by that local government.
Mullvad’s Month
Mullvad completely depreciated config rotation from the UI of their Linux and Android clients. They force the user to logout and log back in to rotate. This is so they can save money on their billing server to not manage all of these changes. Now Mullvad does auto-rotate after a month, but that’s a very long time to essentially have a multi-hop log in the event of any of the 2nd hop servers being compromised. Also Mullvad has both anonymous and KYC identities using the same Wireguard public key.
Issues for Decentralization
This also presents serious problems for decentralized VPNs which may have third parties running servers that are not as well known by the end-user or coordinator.
Instead,
HydraVeil has each profile and layer with it’s own completely separate Wiregaurd configuration file and authentication key.
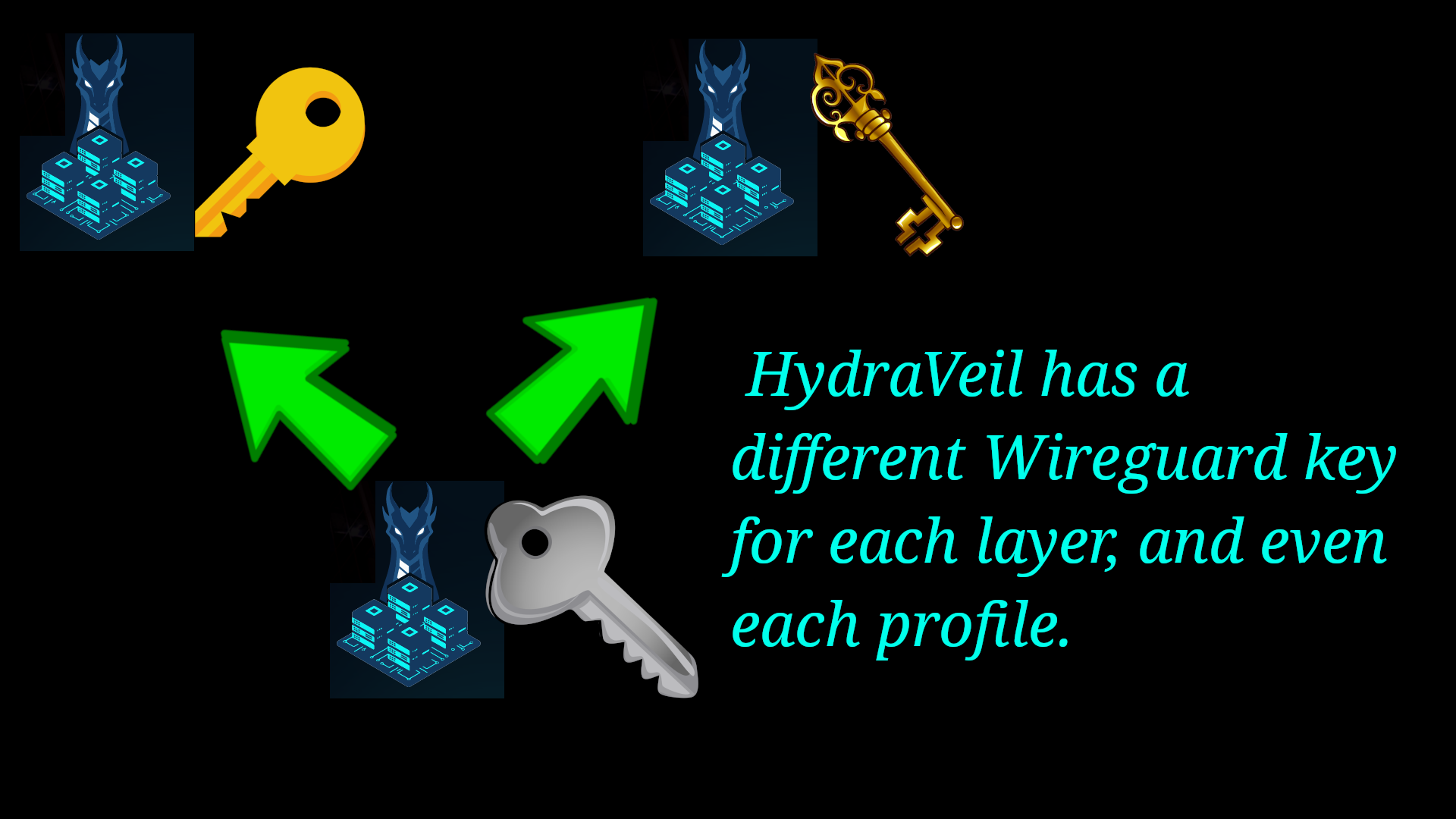
Not only does this protect the first layer from a compromised layer two. But it also protects layer-2 profile servers from one another, by isolating activity to only that profile.

These files are stored in:
Systemwide
/etc/hydra-veil/profiles
Profiles / Browser
.config/hydra-veil/profiles/
Quantum Challenges
HydraVeil’s system also provides significant quantum resistance, by splitting up data into different profiles with different keys. An attacker would be attempting to brute force crack a server’s key for setting up initial tunnels, but it would only yield metadata for that profile. Instead of having both KYC and anonymous identities under the same key metadata and tunnel.
Fingerprint Implementation
HydraVeil uses a variety of tools in unique ways to create realistic browser fingerprints.
Screen Size
Letterboxing
Mozilla’s Letterboxing is used by Tor Browser, to disguise microscopic differences in pixels from one browser window size from another. But Fingerprint-com literally sells the tech to identify and track users through letterboxing across websites. And their company an API system in place to check across their thousands of partners, every hour, when the browser’s window size changes. This is just one of the numerous examples to suggest that without restricting Javascript, Tor Browser is useless. It’s basically Firefox with a new icon. And Fingerprint-com is just some company, imagine what state-level actors can do, that we don’t know about.
Xephyr
Xephyr is a pre-made developer tool to create isolated X11 windows on Linux. HydraVeil uses Xephyr in a number of ways. First to realistically fool websites into thinking the Xephyr window is the user’s real screen-size.
Rat Poison
Xephyr by itself would create a window, but not fill it. To have apps such as a web browser fill out the required screen resolution, we use the very lightweight graphical environment ratpoison.
Organic Screen Size
In the selection of Xephyr & Ratpoison compared to alternatives, we were looking for the most realistic environment, while providing the least negative downsides. To aid in this selection process, we used evaluation tools such as the website deviceinfo.me to see how Javascript fingerprinters perceive artificial environments.
According to deviceinfo.me, Xephyr with Ratpoison did not trigger an artificial reading for the external window size, compared to Tor Browser which shows it as ‘spoofed’.
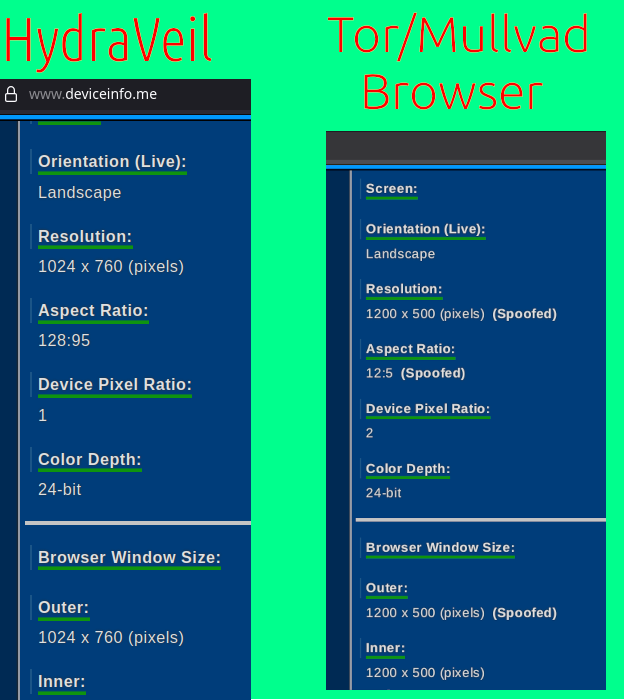
And Xephyr & Ratpoison offered this without any performance negatives, with an instant load and no effect on graphics. This is far faster to load and use as a daily driver than KVM virtual machines, especially when we consider VM setup times.
Cage the Browser
Another issue with Tor Browser’s screen size spoofing, is the user can accidentally full-screen the window, and the facade is over. To avoid this problem, HydraVeil puts web browsers in a tool called the cage. The cage prevents the window from being resized outside of the chosen dimensions, to completely end this source of leak.
Graphical Separation
One of the criticisms of X11 graphical environments for Linux is the lack of graphical separation between apps. So any app can see the typing, chats, and all displayed data of all other apps. This has negatives for things such as a password manager, and presents challenges for users who might be forced to download many different web browsers to avoid fingerprinting, which again means fully trusting large amounts of new software.
Wayland
Wayland solves most of these X11 issues, however not all the Linux distros and users have shifted over. Users should be switching over to Wayland, but some software still has Wayland compatibility issues. And this has been the case for many years.
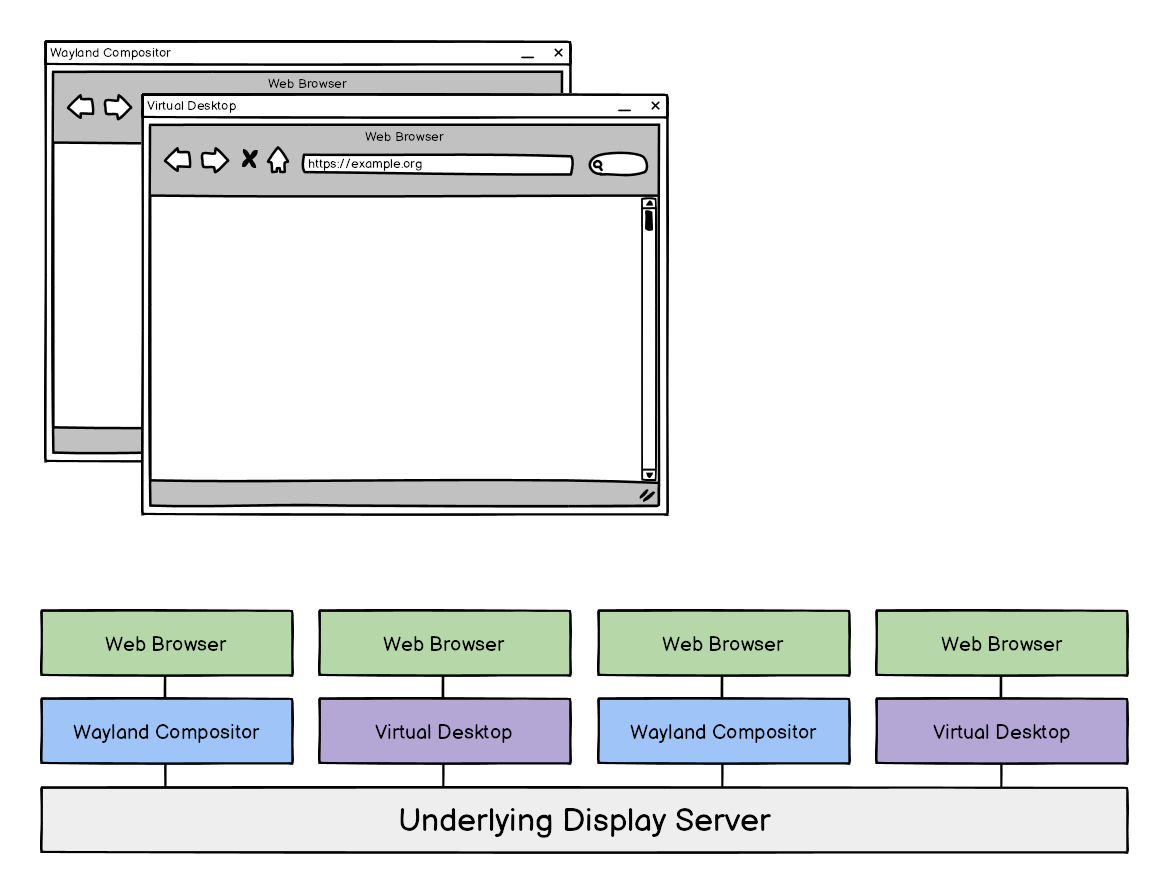
Graphical Isolation
Not only does HydraVeil use Xephyr to provide screen size and timezone privacy, but it also gives graphical isolation for apps, without requiring end-users to change OS or make potentially breaking changes.
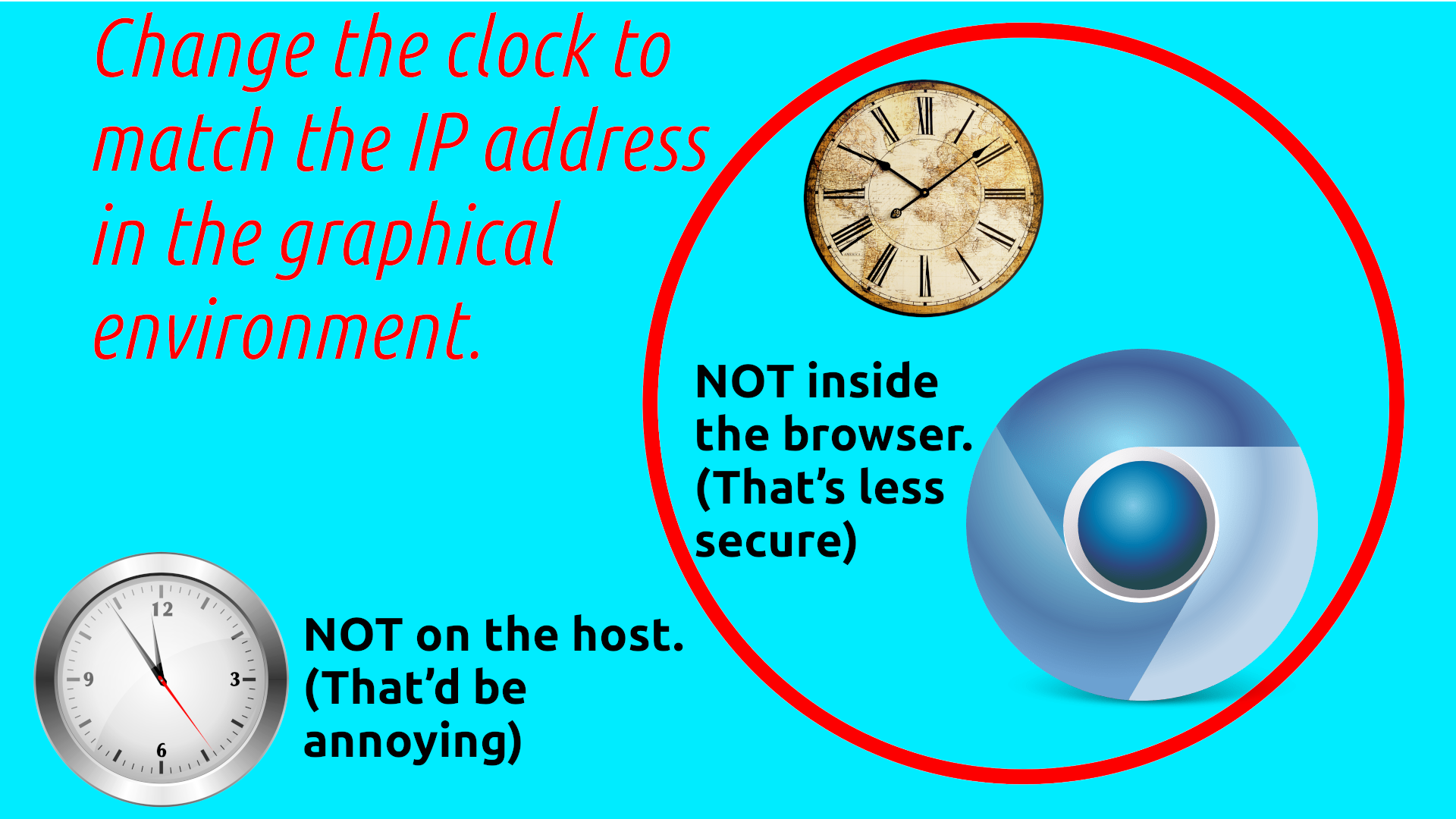
External Timezone
VPNs change the user’s IP address, but not the timezone of their computer’s clock. If there is a mismatch between these, it can provide a backdrop for unique identification from surveillance firms such as Fingerprint-com, and/or be used to haze users for VPN-use from bot detection firms such as Cloudflare and Google.
UTC Liars
Some browsers such as Tor Browser, Mullvad, and Librewolf change the timezone to UTC inside the browser, regardless of what country is being exited as an IP address. But this often conflicts with the timezone of their IP address, and may lead to triggering fraud related security systems for eCommerce or bot detection on social media. Additionally, by doing it in the web browser with spoofing techniques, it is much more vulnerable to an attacker to find the underlying timezone data.
Geoclue
Even worse, many web browsers such as Firefox are pre-configured to allow tools such as geoclue to access the user’s timezone and location. Although geoclue can of course be disabled, an attacker can try to abuse it (or other tools like it) against the will of the end-user to get access to timezone data. In older versions of Linux Mint, geoclue is enabled in the OS config levels by default. This provides a reason to do timezone modifications outside of the browser.
In the Graphical Environment
Within this context, HydraVeil utilizes the Xephyr graphical environment to change the timezone. The timezone is listed in the Wireguard configuration file as a comment, which is ignored by Wireproxy and nmcli. But the HydraVeil client parses it, and then modifies Xephyr to match the timezone to the IP address. And of course this doesn’t touch the user’s host computer timezone, which would be annoying and invasive.
Managed Fonts
Which fonts are installed on a user’s system is a fingerprintable trait, especially if any of these fonts stray from outside the defaults of the most popular distros. As we discussed in a previous article, some versions of Librewolf and Firefox present the same exact identifiable combinations of fonts.
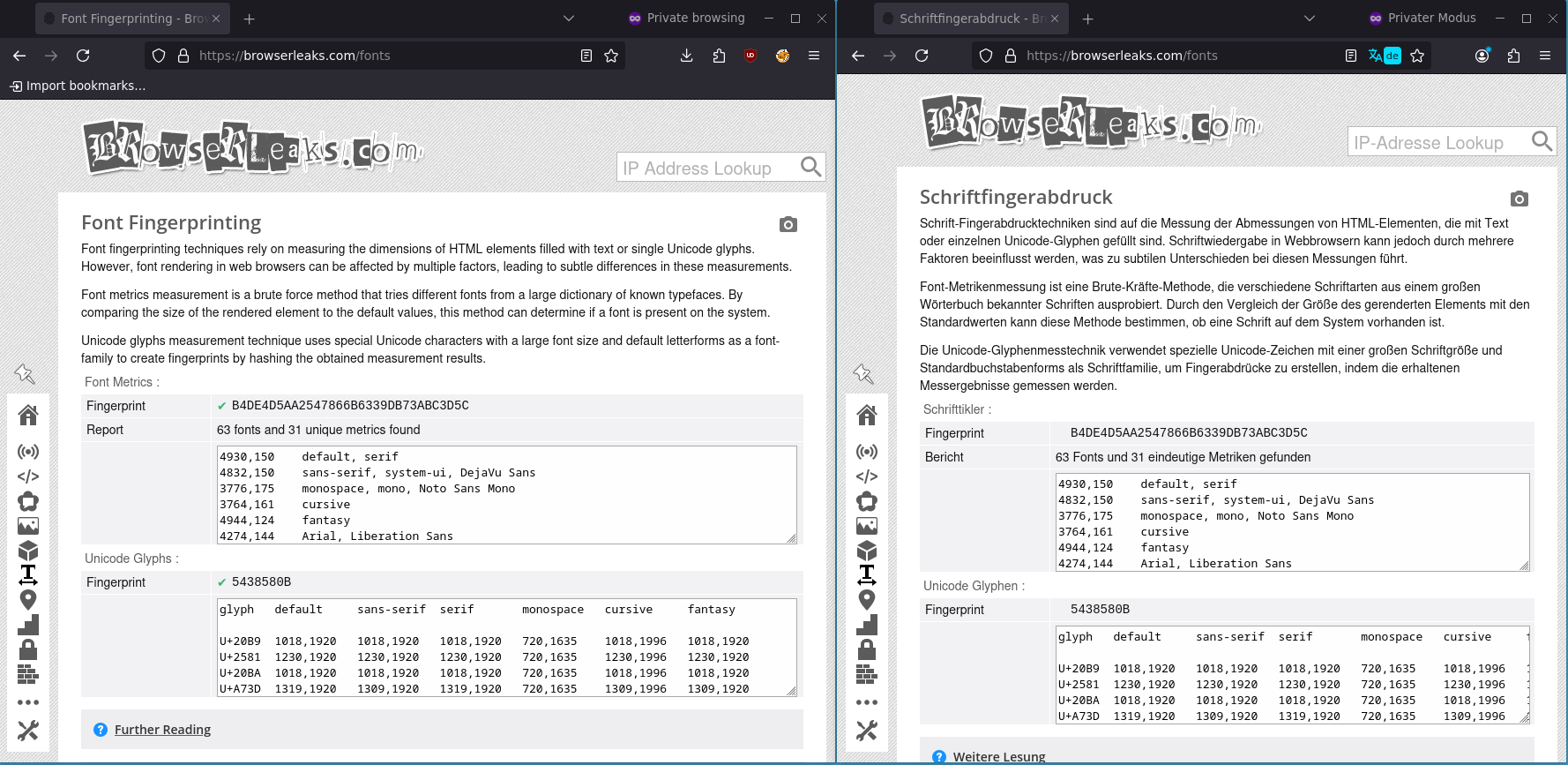
To guard against font fingerprinting, HydraVeil creates a unique set of fonts for each profile. It randomly selects fonts from popular pre-made choices, as well as the user’s own system fonts. This is happening outside the browser, within the profile’s environment.
Location of Fonts
Each profile has it’s own folder for the storage of font ttf files. This can be found in the fonts folder inside the associated profile number of:
~/.local/share/hydra-veil/profiles
Managed Canvas
The web browser canvas can be used to identify users if not properly managed. HydraVeil does this within the browser, and it’s randomized every time the profile is opened. All browser configuration files are open source, transparent, and visible to the end-user without obfuscation.
WebGL
All web browsers are configured to disable WebGL. We are open to expanding the project in the future to other solutions, but this measure handles the problem for now.
Browser Telemetry & Configurations
Most popular Linux distros pre-package vanilla Firefox with significant telemetry and spyware back to Mozilla. The average user does not have time to configure these settings, and may potentially find it too complex a topic to bother. This problem becomes even worse, when you take into account having many different web browsers to avoid fingerprinting.
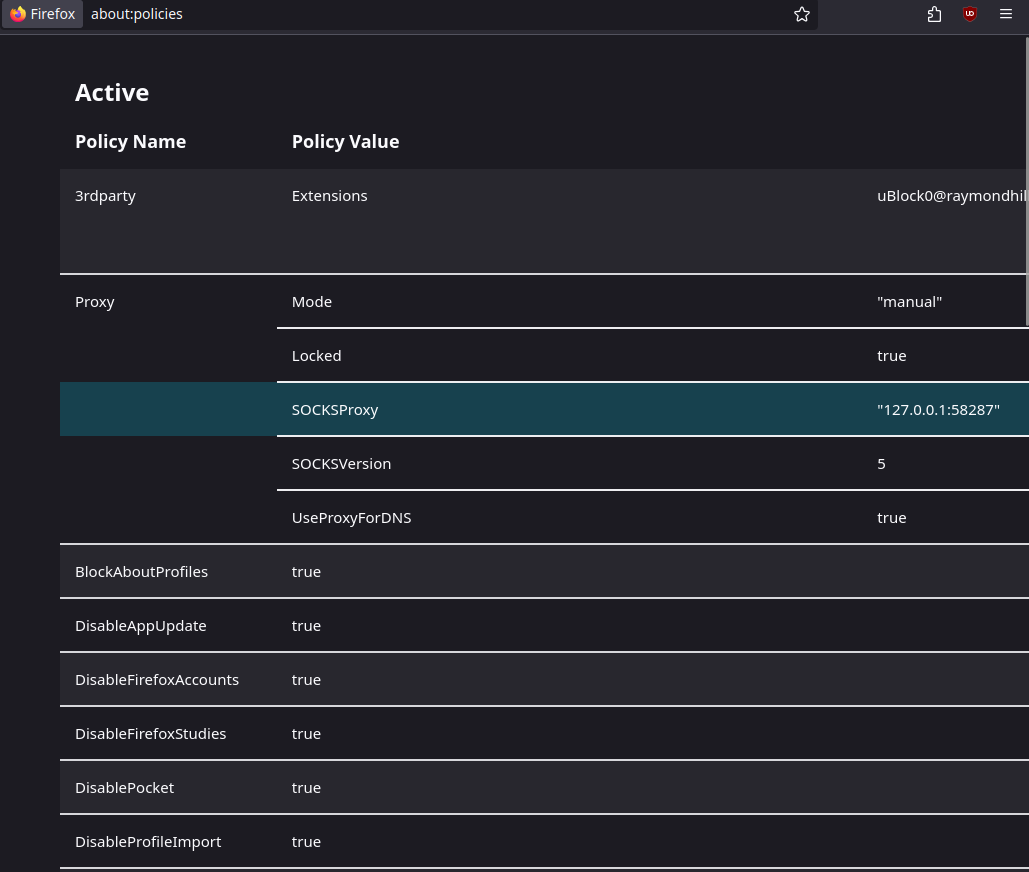
Enterprise Resource Policies
HydraVeil seeks to ease the pain of this problem, by providing an in-house browser distribution, with telemetry disabled and the appropriate settings for privacy. We do this using Enterprise Resource Policies, which are pre-configured settings that can be packaged for managing a browser environment. We utilize Enterprise Resource Policies to set the ports for Wireproxy and/or Tor/Socks5-proxies. And these exact policies can be viewed in the “about:policies” section of each web browser.
Application Type & Data
This could be used for other apps beyond web browsers. HydraVeil is compatible with any app that has a portable version. The same application could be used for different profiles, as the app and it’s related state files are stored separately.
Applications are Stored in:
.local/share/hydra-veil/applications
State Folder:
But each profile has it’s own state files:
.local/share/hydra-veil/profiles/1/persistent-state
As well as the
Storage of Fonts:
.local/share/hydra-veil/profiles/1
Server-side
The HydraVeil network encrypts customer Wireguard configs, between the billing server and the Wireguard node, using mTLS. While the Wireguard node can use any domain name, the billing server exclusively uses our own certificate authority. This not only protects metadata, but also provides significant security to the Wireguard node API. Because any server not signed by this authority, can’t even begin to open a connection. Let alone test that Wireguard node’s API password.
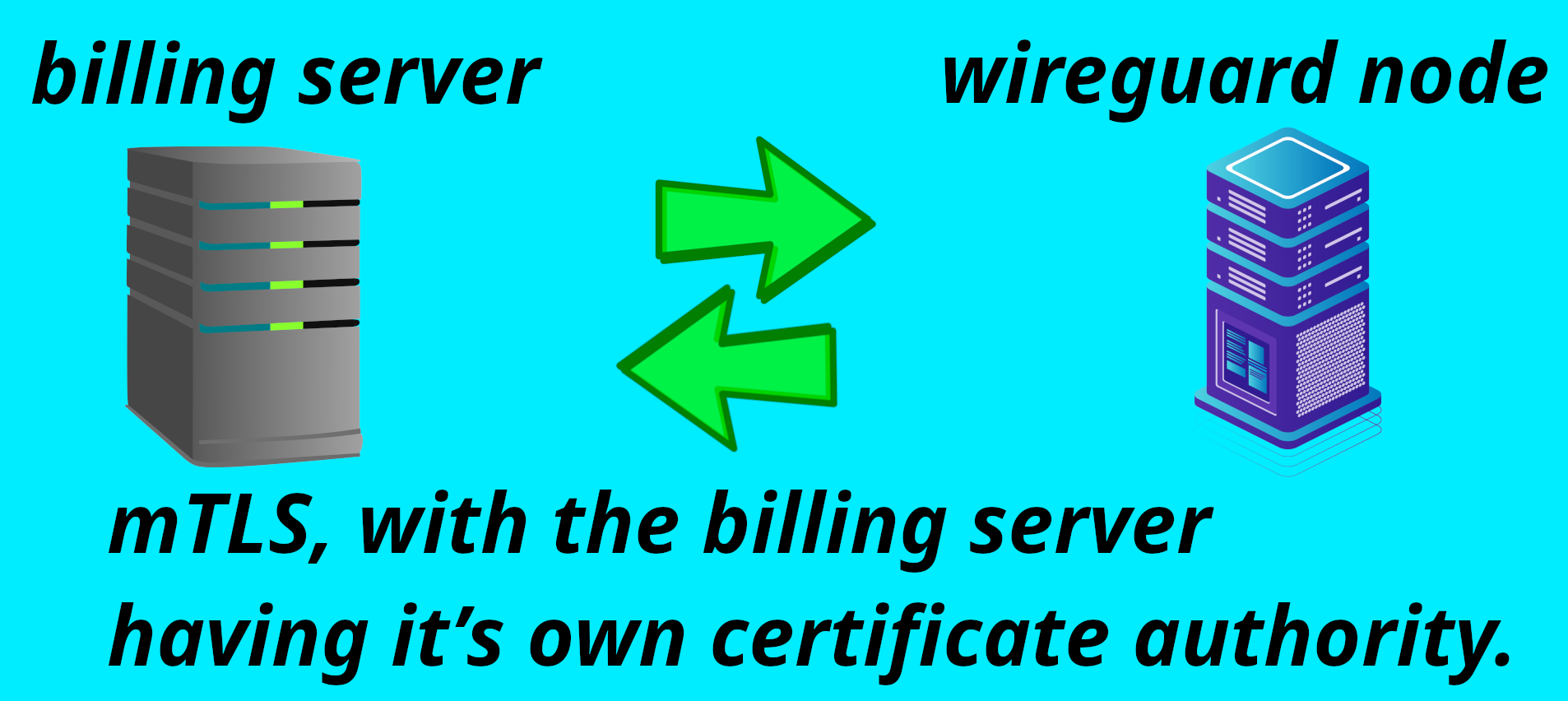
Offline Cold Storage
A certificate authority is different than a self-signed cert, because the authority’s key is kept in offline cold storage. This key then authenticates the billing server, and the public key is recognized as the true authority on all the wireguard nodes.

If the billing server is under duress, the cert authority can sign for a new billing server.

This provides some censorship resistance, to prevent the compromised billing server from contacting the Wireguard node APIs in the future. Since the Wireguard nodes all have the certificate authority’s key, to recognize that previous billing server no longer has a valid cert.
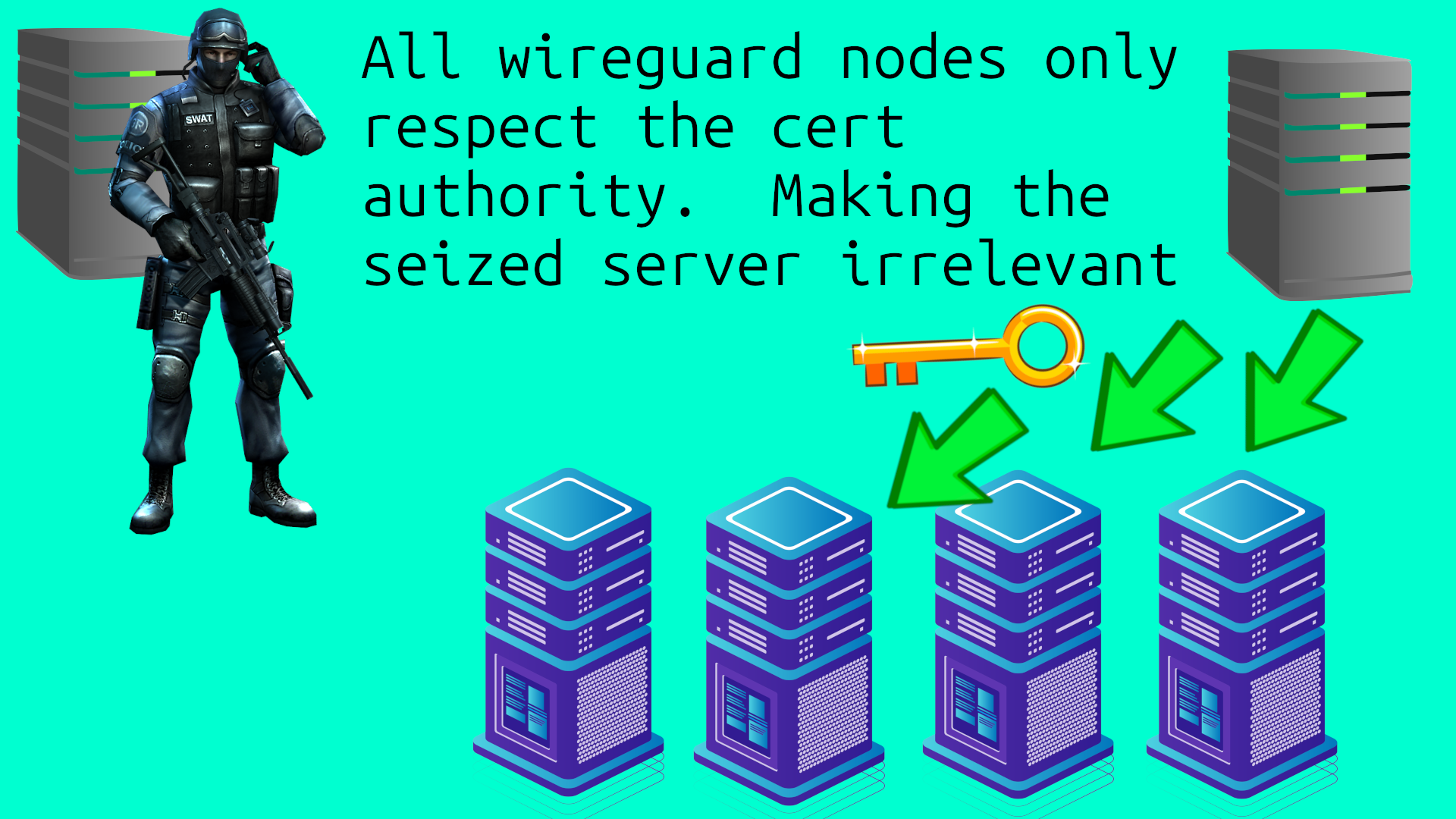
Note: This is far from perfect, and a compromised billing server could still wreck a lot of temporary havoc. But it would not permanently take down the service. And it avoids us having to print our own cryptocurrency to get some censorship resistance, which means an endless focus on making yet another new coin. When we should be focusing on making things people actually want to buy.
Conclusion
In summary, HydraVeil offers:
Privacy
-Realistic screen-size faking
-Timezone matching to the IP-address
-Managed fonts per profile
-Managed web browser canvas
Security
Bubblewrap Filesystem isolation
Bubblewrap DBUS blocking
Graphical/Keyboard isolation
Avoids a 24-7 sudo daemon
Networking
-Artificial networking environment
-Two layers of networking
-Masked Tor, via Tor->socks5 proxy
-Or Two layers of Wireguard for speed
-Wireproxy on the 2nd Layer
-Wireguard Key Isolation. (Uses Two Different Wireguard configs, which is unique for multi-hop.)
Unique Decentralization
-Encryption verification of VPN operators
-Use of ed25519 and Nostr
-Directly connects to the chosen node, to:
-Avoid contacting billing server each time
Browser Distro
-Telemetry stripped from Browsers
-Eases the Burden of Managing many browsers
-Uses Enterprise Resource Policies to manage settings
If you really want to learn and take your privacy to the next level, Learn about HydraVeil, Access our VPN, and subscribe to our new content via: Arweave Video RSS, Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts
Website Makeover
Learn the Concepts with Awesome Visuals
[SP]
Feb 14, 2026
Tor Sync & Tor Profiles Fixed | Release 2.2.1
Faster Initial App Startup
[SP]
Jan 20, 2026

New Sweden VPN Node
Run by AilliA of XMRBazaar
[SP]
Jan 18, 2026

1 Second Saved | Release 2.1.4
Faster Initial App Startup
[SP]
Jan 16, 2026