Solve Whonix's Flaws
These are Big Whonix Problems
Whonix is TWO virtual machines
One that you use (workstation), and another you don’t do anything in (gateway). The gateway just connects to the internet with nothing else in it.
Twos VMs is a lot of Resources
Not only storage space, but also RAM/CPU.
Because you need both a workstation and gateway, it’s an epic pain to have multiple ones. And you likely can’t have 4 VMs open up at once.

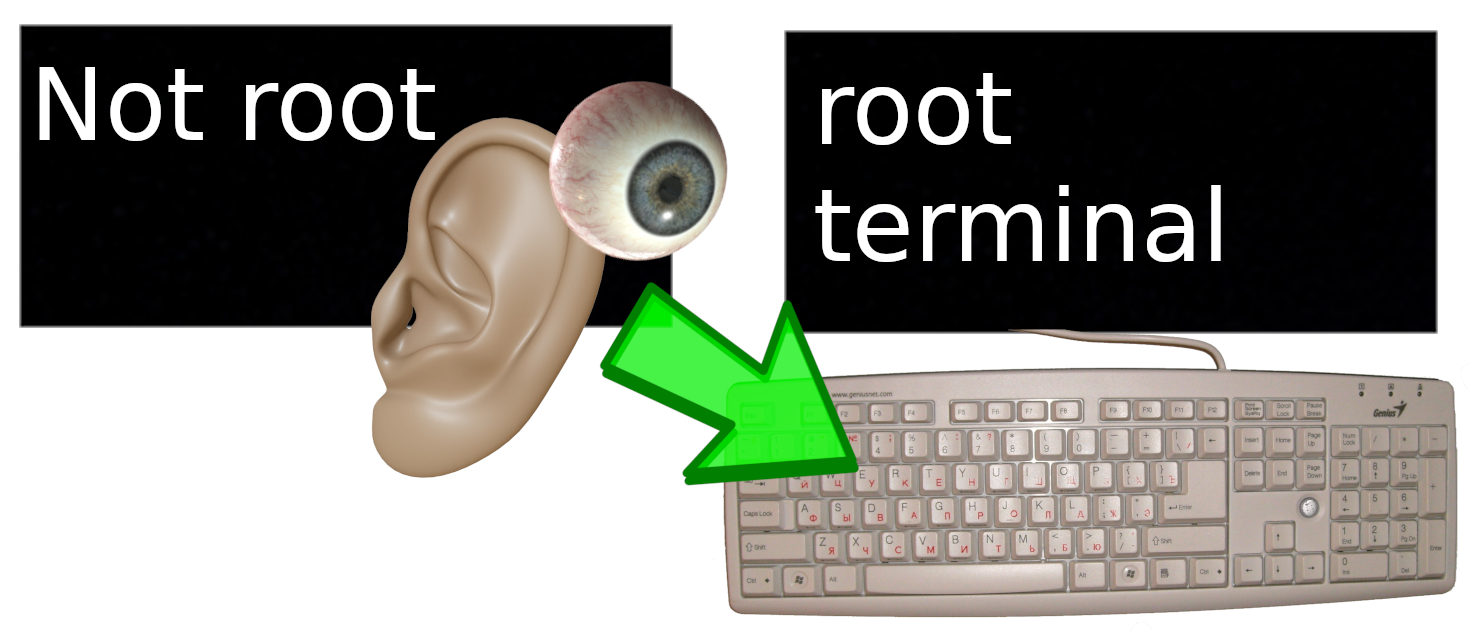
But doing everything in a single Whonix workstation is an issue, because it uses an X11 display manager by default.
There’s a huge flaw in Whonix’s X11,
ALL programs can see the display and keyboard for ALL other programs.

Whonix & Mint use X11
Every program can see you copy-paste in stuff into the Whonix VM. Even if your password manager is outside of it, it’s still a shared clipboard going in.

Even if they can’t get the actual passwords, the programs could see the metadata of what accounts are your’s, such as usernames

QubesOS Chick
Joanna Rutkowska the creator of QubesOS complained about this X11 Flaw

Any app can see all keystrokes

Full QubesOS Dev Quote:
One application can sniff or inject keystrokes to another one, can take snapshots of the screen occupied by windows belonging to another one, etc. If you don't believe me, I suggest you do a simple experiment. Open a terminal window, as normal user, and run xinput list, which is a standard diagnostic program for Xorg (on Fedora you will likely need to install it first: yum install xorg-x11-apps):
$ xinput list
It will show you all the pointer and keyboard devices that your Xorg knows about. Note the ID of the device listed as \u201cAT keyboard\u201d and then run (as normal user!):
$ xinput test id
It should now start displaying the scancodes for all the keys you press on the keyboard. If it doesn't, it means you used a wrong device ID.
Now, for the best, start another terminal window, and switch to root (e.g. using su, or sudo). Notice how the xinput running as user is able to sniff all your keystrokes, including root password (for su), and then all the keystrokes you enter in your root session. Start some GUI app as root, or as different user, again notice how your xinput can sniff all the keystrokes you enter to this other app! [3]
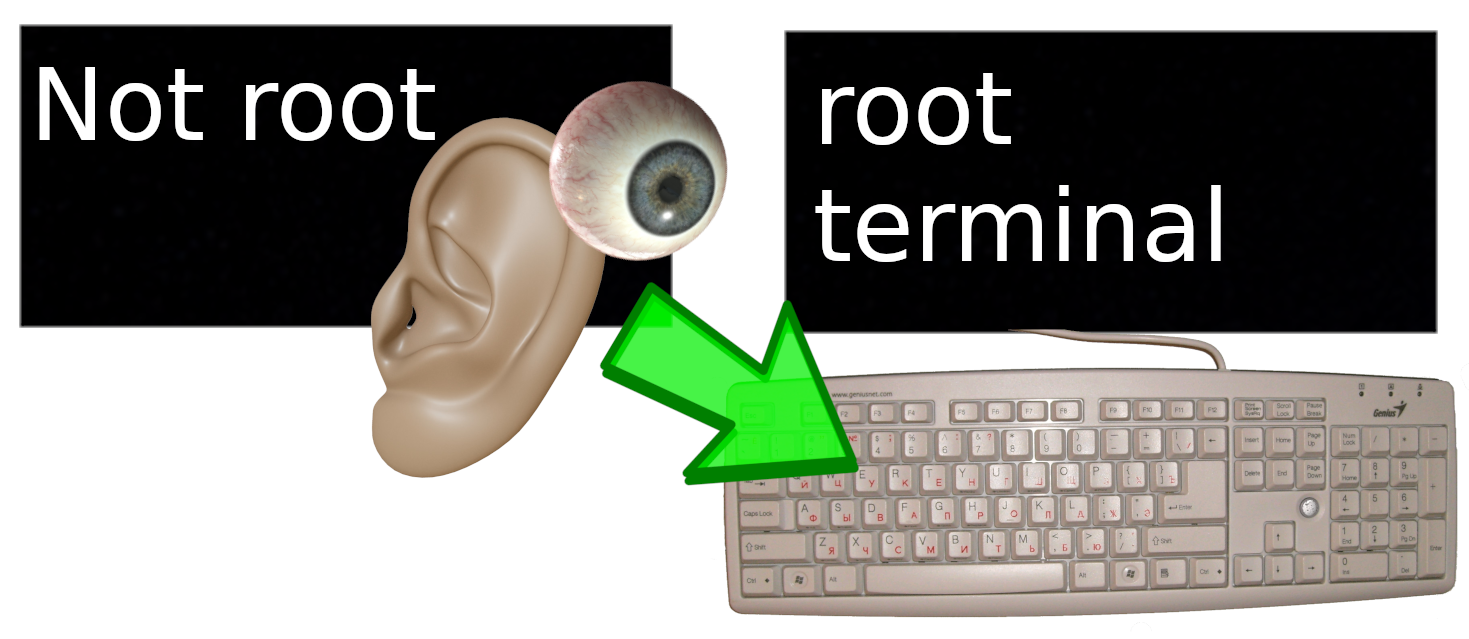
Both Whonix and Mint use X11

But isolation is the main reason you tolerate Whonix’s pains, such as..
Very often Tor IP addresses are blocked.
To solve this, one can use a socks5 proxy from inside Whonix, but this means a different browser.
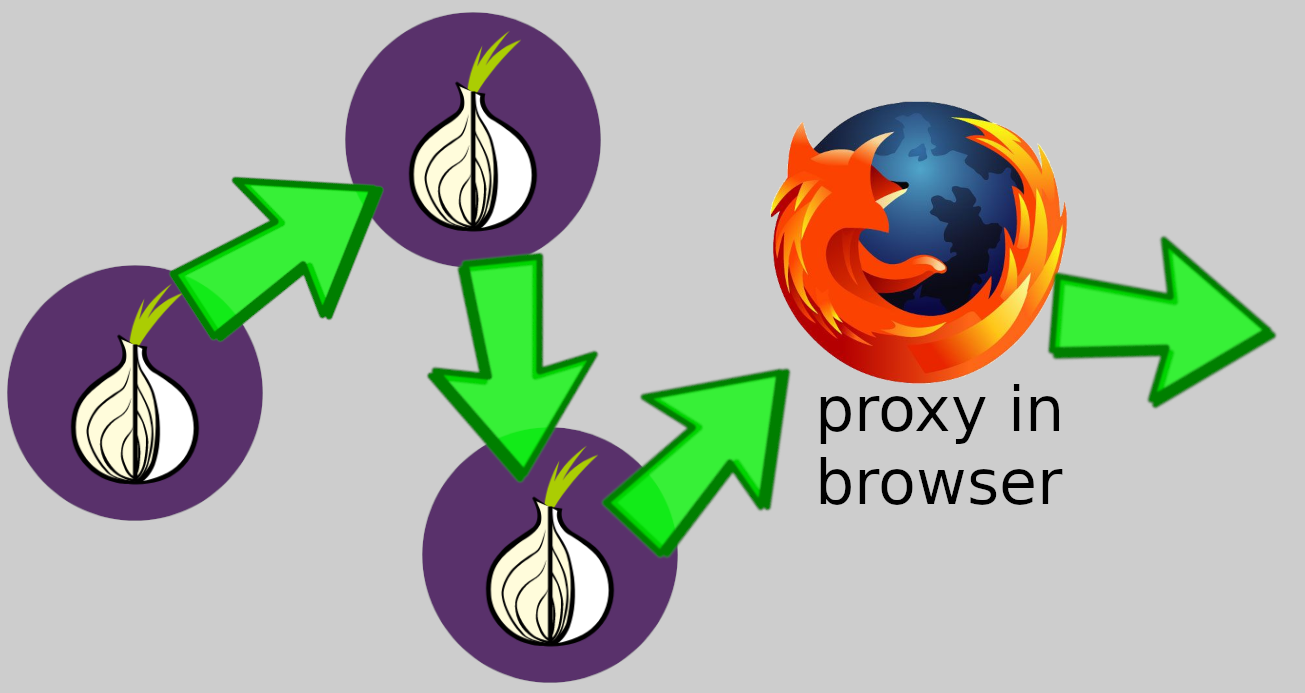
But without “Tor Browser”, you’d have browser fingerprint issues
In our previous article we discussed Browser Fingerprinting AI assigning you unique IDs
To Avoid Fingerprinting, You Install More Browsers
But now that’s more and more new forked software seeing your entire life’s usernames/password metadata, and all keystrokes.

Even worse Firefox-based browsers are insecure
As we covered in our previous article, all Firefox based browsers have serious security issues compared to Chromium ones. And this includes Tor, which is built upon evil Mozilla’s problems.

GrapheneOS dev, Daniel Micay Quote:
Firefox quite literally monkey patches libc to use their own horrible linker to ship libraries decompressed and force them into memory as needed based on deliberately crashing / recovering on usage instead of just mapping libraries from the apk which would be more secure, far simpler and way leaner on memory usage.
But Chrome proxy extensions suck!
Chromium proxy extensions have issues with password authentication. But without extensions, you’re in for a painful complex misery.
Mullvad Blocks Tor
“Trust me bro, Privacy is a Right”
Mullvad is ending support for OpenVPN, which means blocking Tor from being used before Mullvad. Because Wireguard uses UDP packets, and the Tor network is TCP.
Self-hosting Makes You Unique
When you self-host, you do all of this work, pay all this money, and then that IP address is associated with a single activity. Now each time you use it, they know that unique “snowflake IP” is the same user.
HydraVeil Solves ALL of these problems

Run HydraVeil inside Whonix
Isolated X11 Display
From within Whonix, HydraVeil isolates and launches an X11 display environment, that prevents the browser from seeing chat apps or the rest of the system. This image shows it’s launching a socks5 proxy to evade the Tor blocks, using Chromium, and matches the environment’s timezone to the IP address (with burner crypto billing).
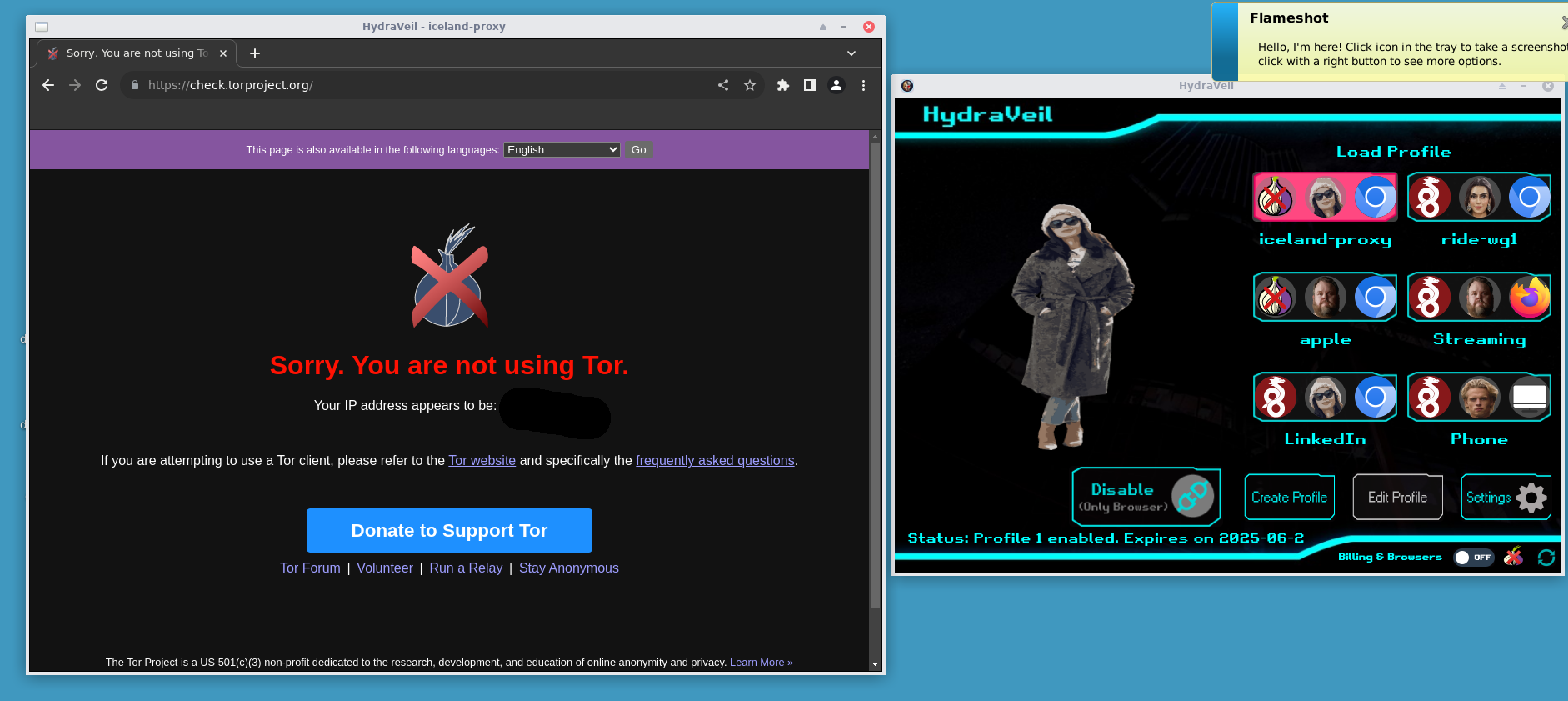
HydraVeil:
–Solves Whonix’s X11 Display Issues
–Solves Tor IP blocks
–Solves Tor Browser not working
–Solves Forced Firefox choice issues
–Solves Chromium proxy extension issues
–Solves Easy Browser Distribution
–Solves Timezone issue with Whonix UTC
–Solves Mullvad’s Tor Block
–Solves Unique Self-host IPs
–Isolated Burner Billing for Profiles
–$1 in Monero or Bitcoin Lightning
Get started for $1:
Click Here to Get Access
And here is the tutorial for Whonix.
Note: If you don’t feel like setting up Whonix, HydraVeil has native Tor options as well.
If you really want to learn and take your privacy to the next level, Learn about HydraVeil, Access our VPN, and subscribe to our new content via: Arweave Video RSS, Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts

How HydraVeil Works
Technical Deep Dive: The Yellow Paper
[SP]
Feb 20, 2026
Website Makeover
Learn the Concepts with Awesome Visuals
[SP]
Feb 14, 2026
Tor Sync & Tor Profiles Fixed | Release 2.2.1
Faster Initial App Startup
[SP]
Jan 20, 2026

New Sweden VPN Node
Run by AilliA of XMRBazaar
[SP]
Jan 18, 2026