Why a Nostr VPN?!
How should node operators identify themselves?

Tor is a Conflict of Interest
The malicious group KAX17 had been identified as having run up to 35% of the middle relays, before the Tor Project removed 900 of their servers. But having the Tor Project remove government nodes is a conflict of interest, when their primary customer is the US government.
In the fiscal year 2021-2022, approximately 53.5% of the Tor Project's revenue came from U.S. government funds. This percentage reflects an increase from the previous fiscal year.
Even Tor’s founder admits the technology was designed to help the government gather info.
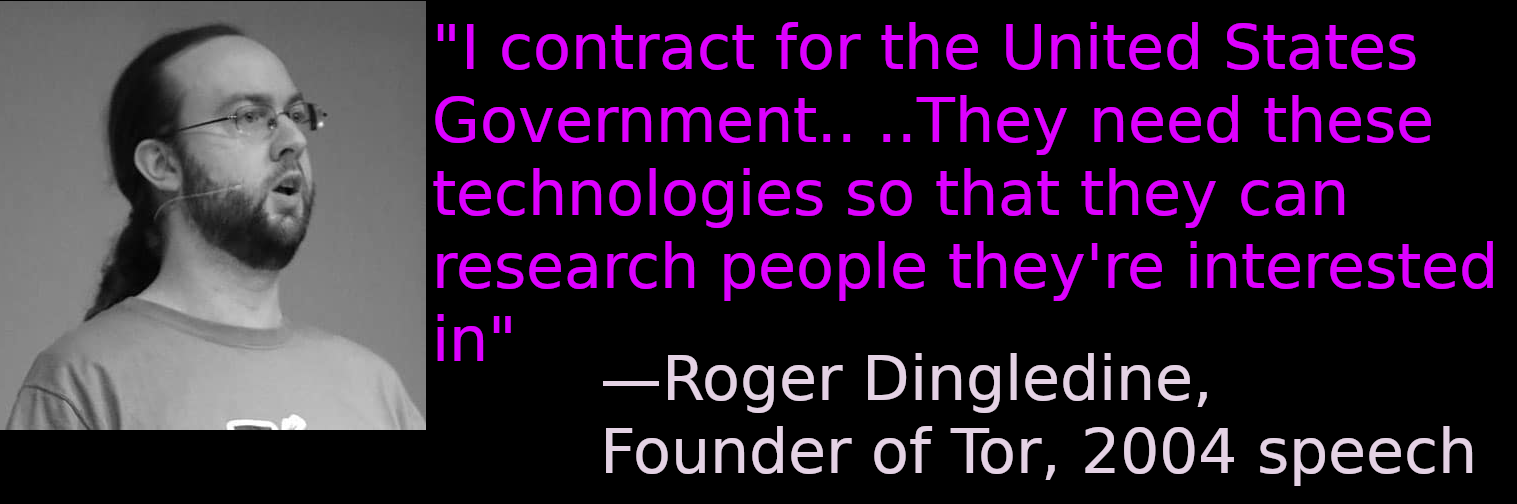
As CyberInsider reported, Tor developer Steven Murdoch discovered a vulnerability with the way Tor was handling TLS encryption. Roger Dingledine alerted two government agents about this vulnerability, before the general public. [1]

Because it’s a free socialist resource, it’s abused, which leads to the exit IPs being blocked.
Long List of Issues
As we wrote about previously, The Tor Project has a long history of problems and arrests with no explanation. For example in 2017, the FBI dropped a case against a school worker accused of downloading child pornography because the FBI would have rather let him go than reveal the source code for how they deanonymitized him through Tor. Now, some say these can be solved with good opsec or downplay the quantity of government nodes, but…
Tor Nodes are a commodity.
So the end-user has no real way to evaluate their legitimacy.
Maybe they are the government, maybe not.

Our Approach
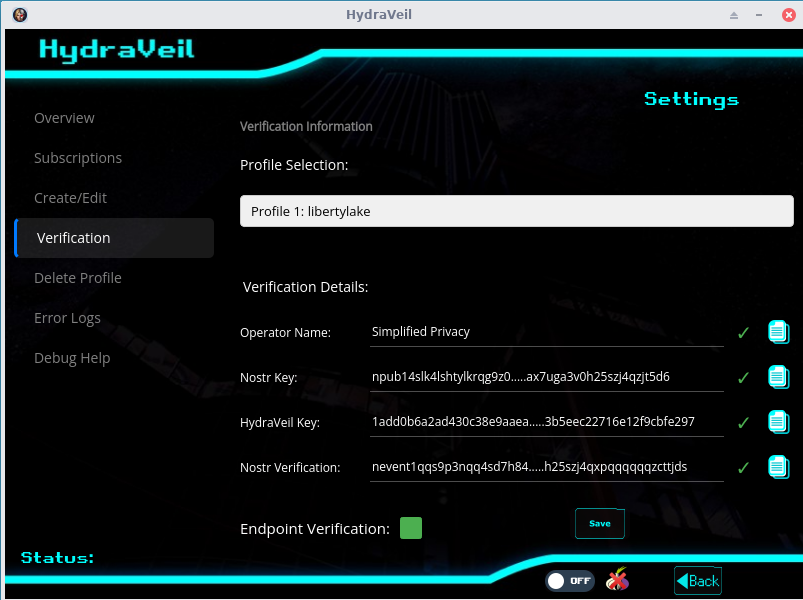
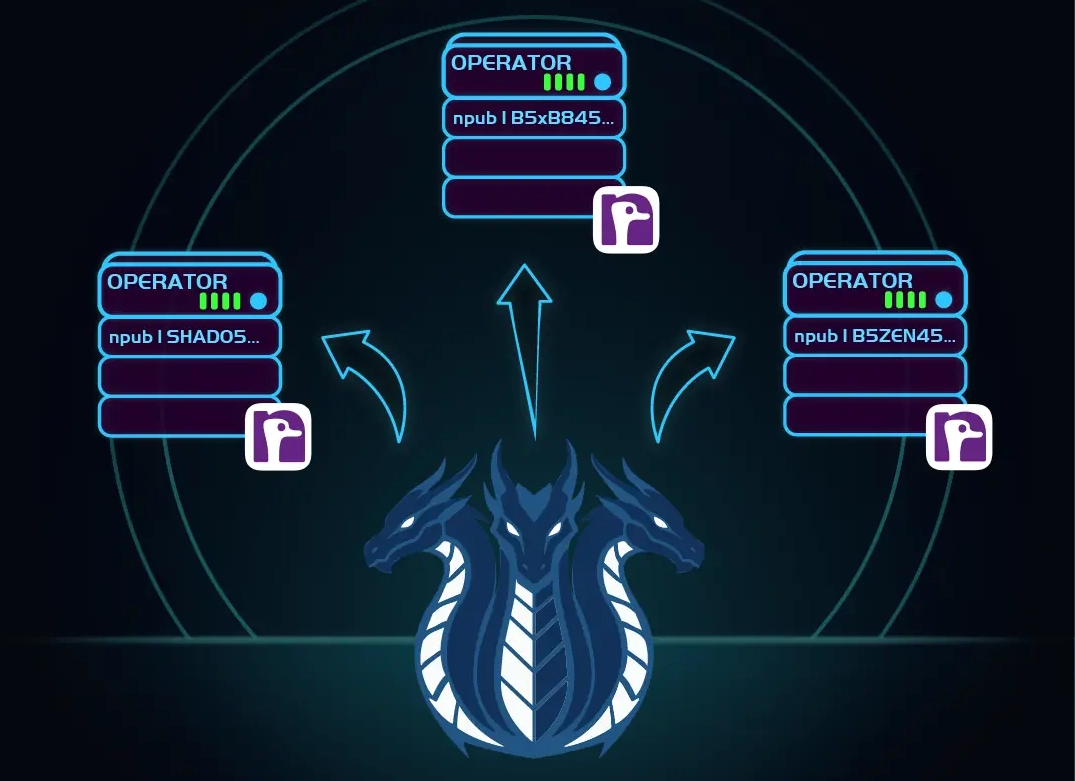
Instead of having random nodes with no way to evaluate, our network uses Nostr influencers who post (sign) to the social network their HydraVeil key.

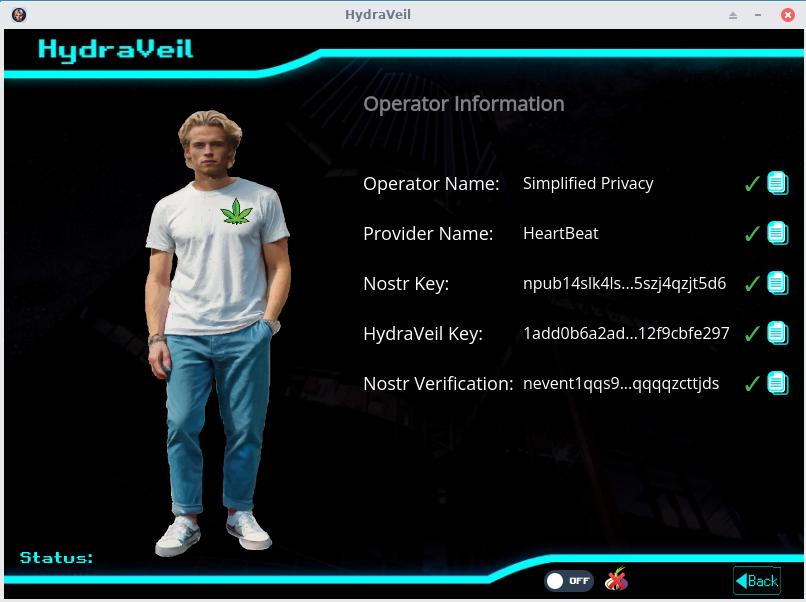
All our Wireguard Endpoints are signed by the operator.
And HydraVeil verifies the signed Wireguard Public key to establish a tunnel prior to connecting,
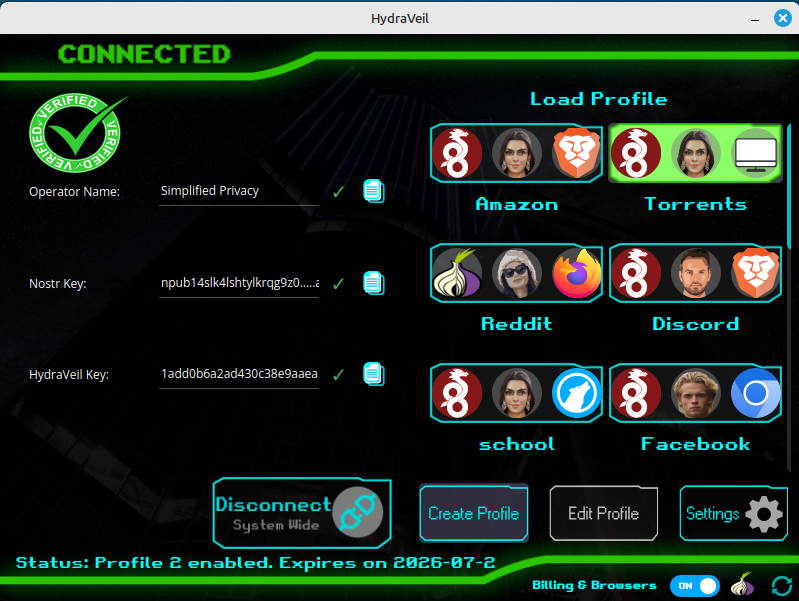
This provides undeniable cryptographic proof that particular Nostr member is running the node. Visible anytime in the settings and post-connection.
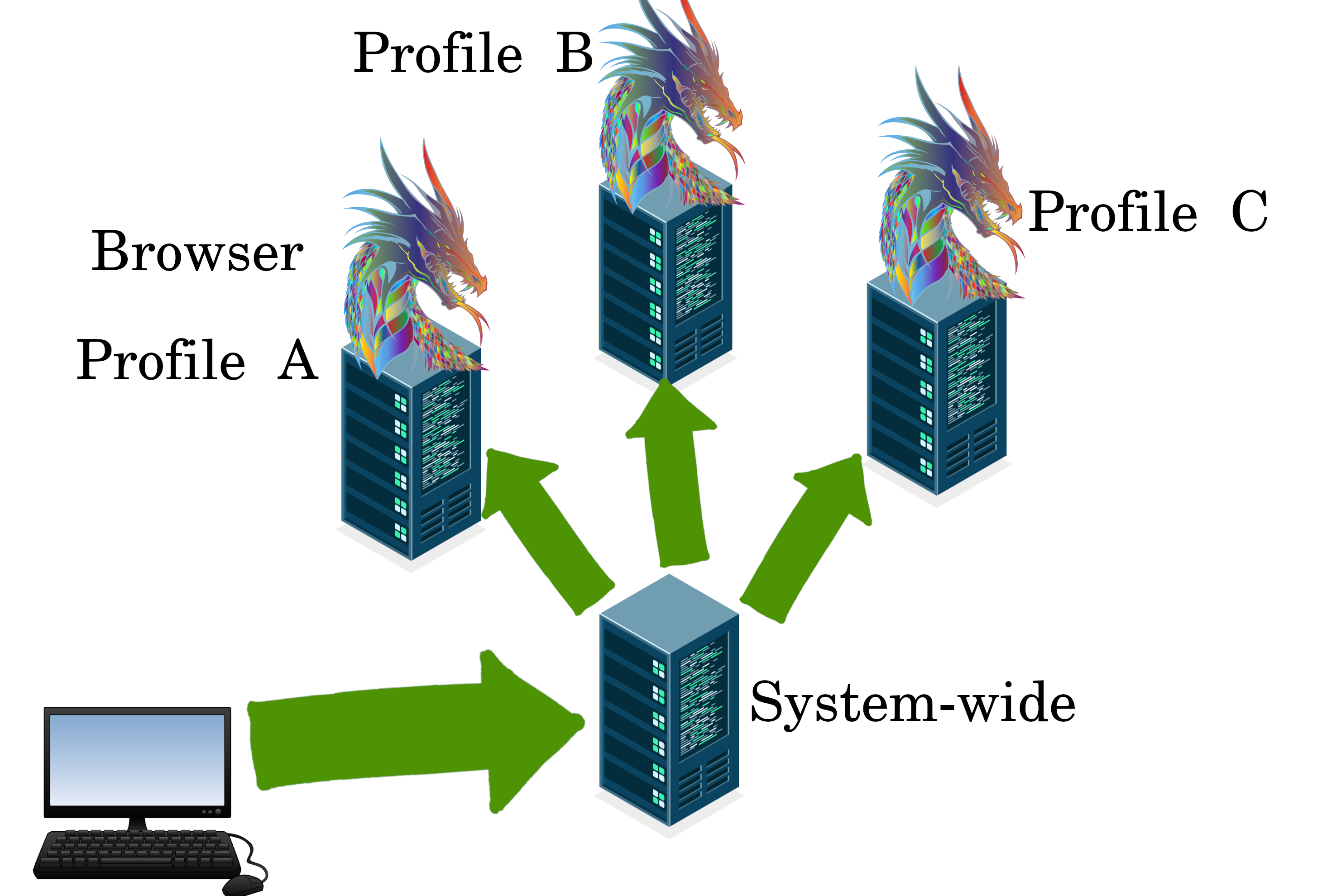
With two layers, it’s anonymous,
Since the first layer for system-wide can’t see the traffic. And the second layer, can’t see your real home IP address.
If you want a third hop, you could even put it on your router.
Tor Browser requires restricting JavaScript, which breaks websites.
While HydraVeil can’t be stopped, or even detected.
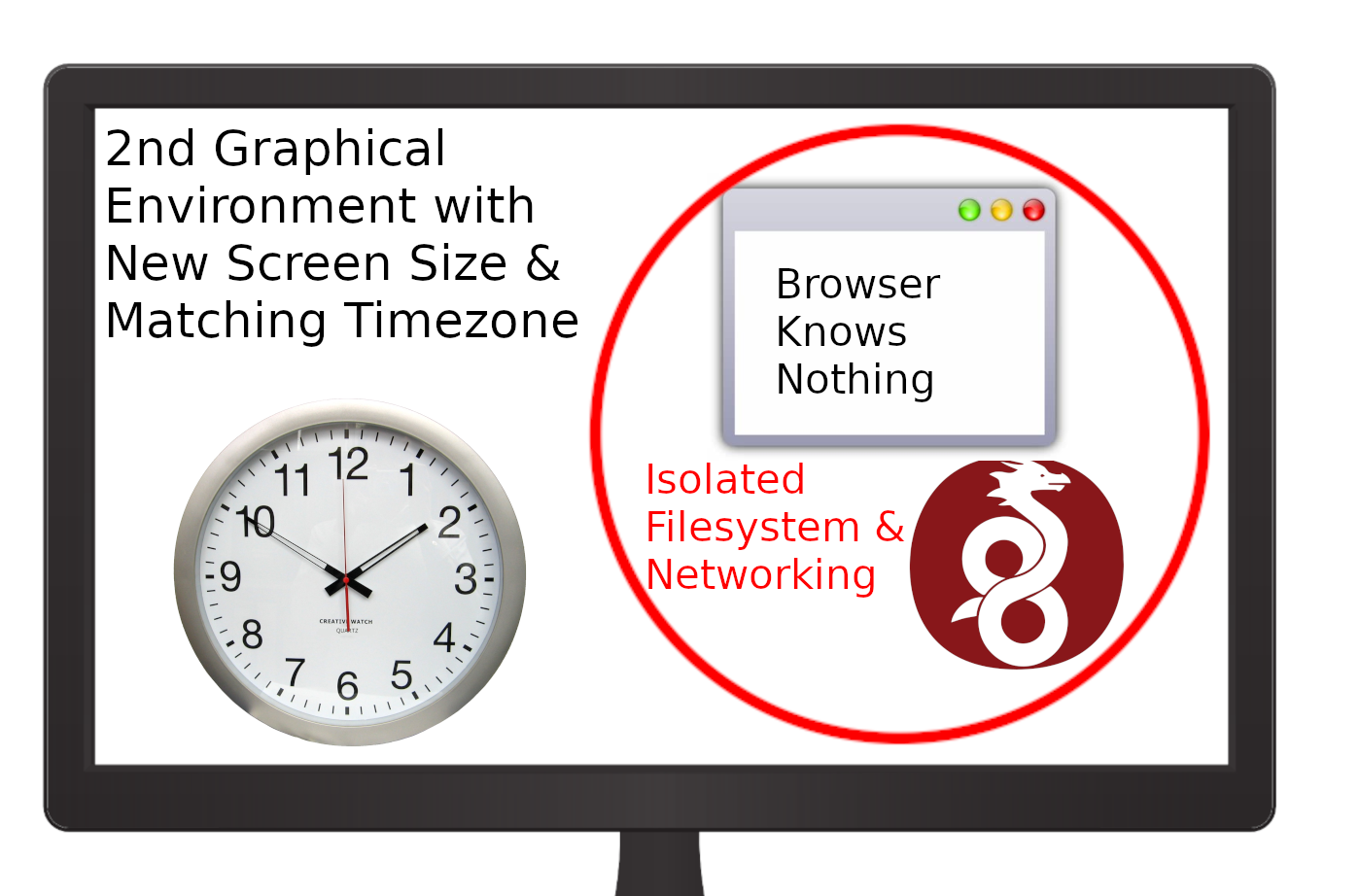
This looks like your real fonts, real screen size, real timezone (matching the IP), and more. So you’re hazed way less than Tor.
As we discussed previously, the intel agencies love to tap centralized choke points, such as ocean cables.

But Tor is indifferent to locations.
So Tor users bounce back and forth over tapped ocean cables with the same packet size.
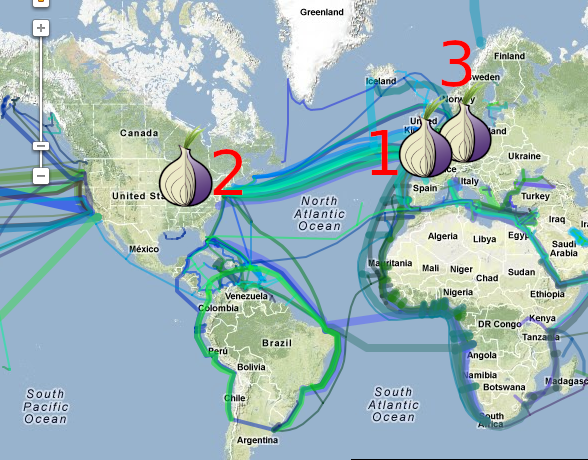
Tor arbitrarily divides nodes into public, clearly defined, static roles of entrance “guard”, middle “relay”, and exit nodes. This makes it far easier to track and predict the path, when the developers did NOT have to do this.
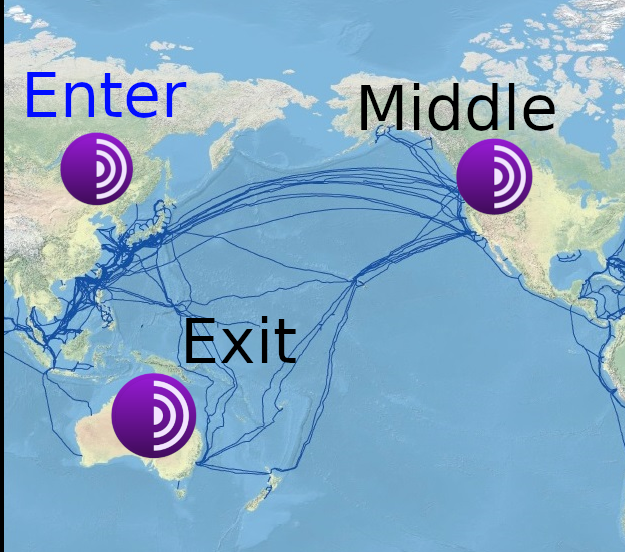

While as with HydraVeil,
All nodes could be an entrance or exit.
You could be coming or going. And you can travel through the infrastructure, as it moves farther away from you.

Tor Recap,
Slow
Socialism
Ineffective Routing
Tor Browser Breaks Websites
Forces JavaScript Restrictions
Conflict of Interest Devs
Can’t Evaluate Commodity Nodes
Blocked IP addresses
Can’t do Live Audio/Video (UDP)
Predefined Predictable Roles for Nodes
(Entrance, Middle, Exit)
HydraVeil Recap
Nostr Operators
User picks who they trust
User picks their route
All Websites Work
Fast yet Anonymous
Advanced Isolation Security
Clean IP addresses
Fingerprint protection without breaking websites
Appears to website as Real
Anonymous Audio/Video Web Apps
All Nodes Could be an Entrance or Exit

Learn How the Encryption Verification Works
Or Proceed to the Install Page
If you really want to learn and take your privacy to the next level, Learn about HydraVeil, Access our VPN, and subscribe to our new content via: Arweave Video RSS, Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts

Bareass Mullvad
How any app can rip these VPNs down without sudo
[SP]
Feb 20, 2026

How HydraVeil Works
Technical Deep Dive: The Yellow Paper
[SP]
Feb 20, 2026
Website Makeover
Learn the Concepts with Awesome Visuals
[SP]
Feb 14, 2026
Tor Sync & Tor Profiles Fixed | Release 2.2.1
Faster Initial App Startup
[SP]
Jan 20, 2026
